Practicle Ethical Hacking : Lab Academy Walkthrough
first look its a default apace page nothing usual so i tried to enumerate more nmap scan results ports open 22 80 21 in which anonymous ftp is aloud at…
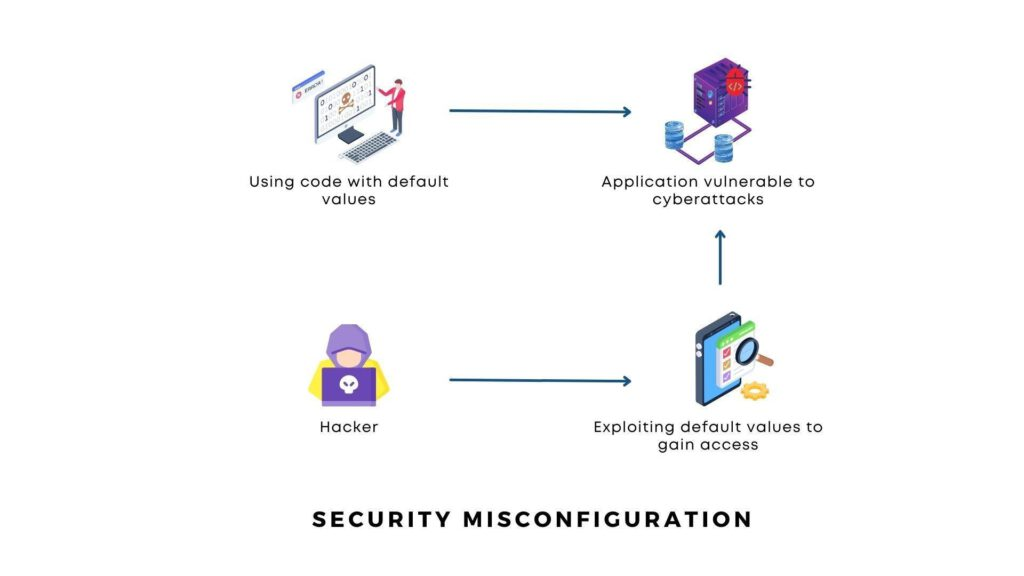
OWASP TOP 1O – Security Misconfiguration: Understanding, Risks, and Best Practices for Prevention
Security misconfiguration is a significant vulnerability that can expose systems, networks, and sensitive data to a wide range of attacks. By understanding the common causes, taking steps to prevent misconfigurations,…
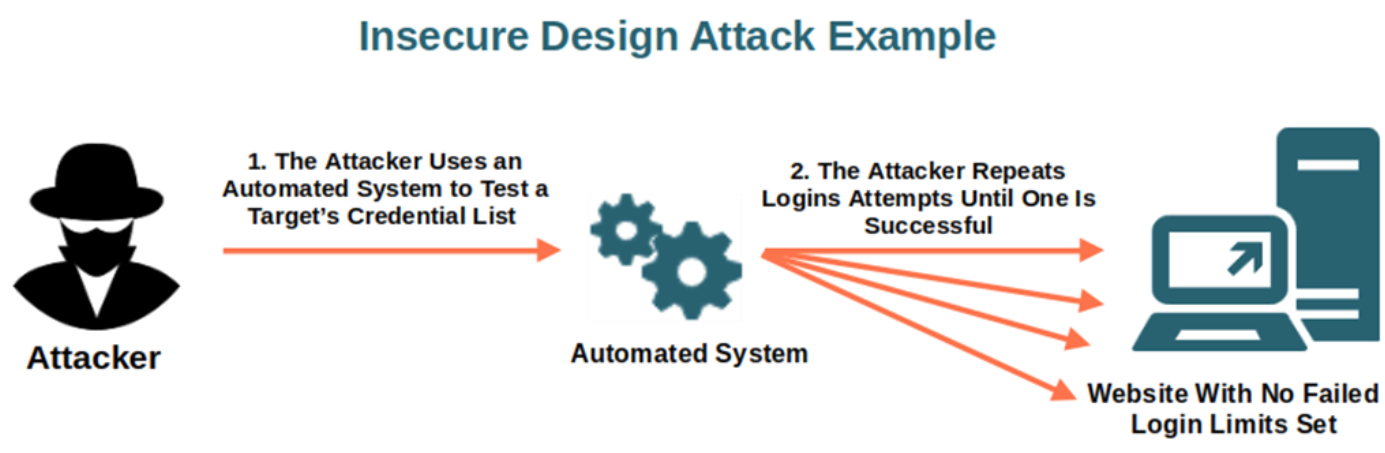
OWASP TOP 10 – Insecure Design Vulnerabilities: Understanding Risks and Prevention Best Practices
Insecure design vulnerabilities are serious security risks that can compromise the confidentiality, integrity, and availability of a system. These flaws typically occur at the architectural level, and preventing them requires…
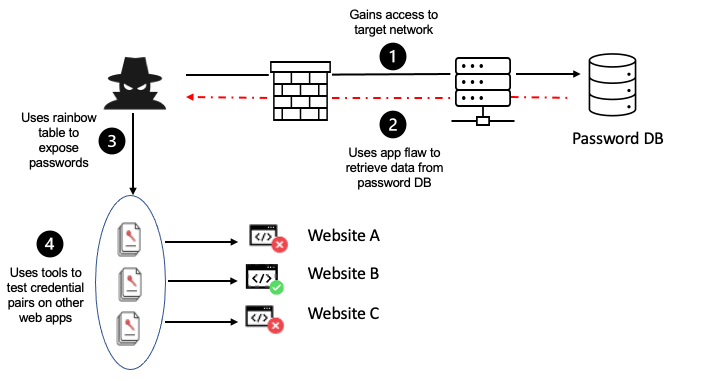
OWASP TOP 10 – Cryptographic Failures: Understanding Vulnerabilities in Secure Systems
What is Cryptographic Failure? Cryptographic failures occur when algorithms, protocols, or their implementations are flawed, leading to insecure encryption, decryption, or hashing processes. These failures can undermine the entire security…
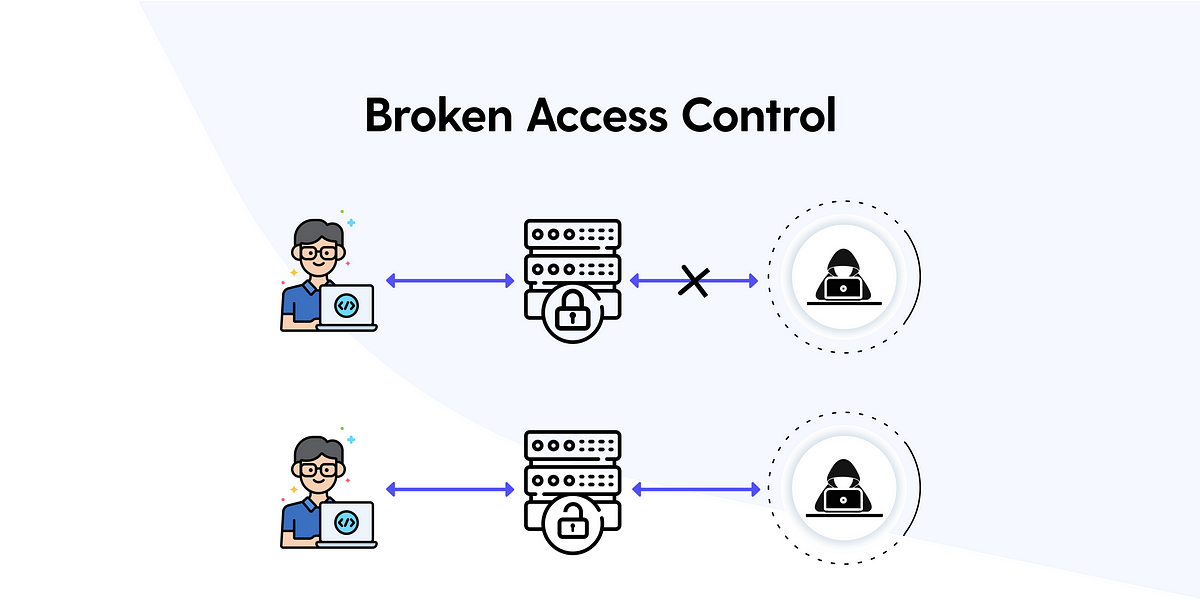
OWASP TOP 10 – Broken Access Control Vulnerabilities
Broken Access Control (BAC) is a critical vulnerability that can lead to serious security breaches, including unauthorized data access, privilege escalation, and even complete system compromise. By enforcing strict server-side…
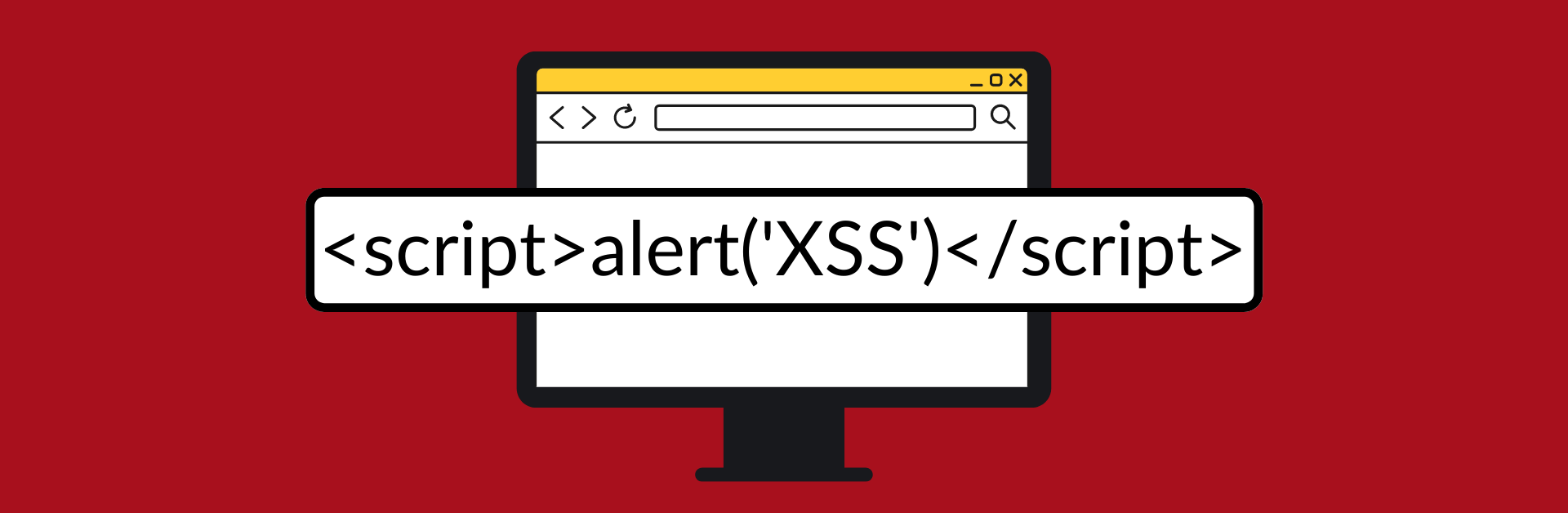
OWASP TOP 10 – Cross-Site Scripting (XSS) Vulnerabilities and Mitigation
ross-Site Scripting (XSS) is a severe vulnerability with far-reaching consequences for users and businesses. By implementing robust defenses like input validation, output encoding, and CSPs, developers can significantly reduce the…
OWASP TOP 10 – SQL Injection: A Deep Dive into the Threat, Impact, and Mitigation
SQL Injection remains one of the most dangerous web application vulnerabilities. Understanding its mechanics, testing for weaknesses, and adopting secure development practices are essential steps toward robust security. Regular penetration…
Mastering Password Hashing and Cracking: Complete Guide with Practical Commands and Examples
Learn about common password hashing algorithms like MD5, SHA-1, SHA-256, bcrypt, and Argon2, and how attackers use tools like Hashcat to crack them. This guide focuses on understanding security vulnerabilities…
Hydra Password-Cracking Tool: A Comprehensive Guide
Hydra is a powerful password-cracking tool used by cybersecurity professionals for penetration testing. One of its core features is its ability to perform brute-force attacks across various protocols, including SSH.…
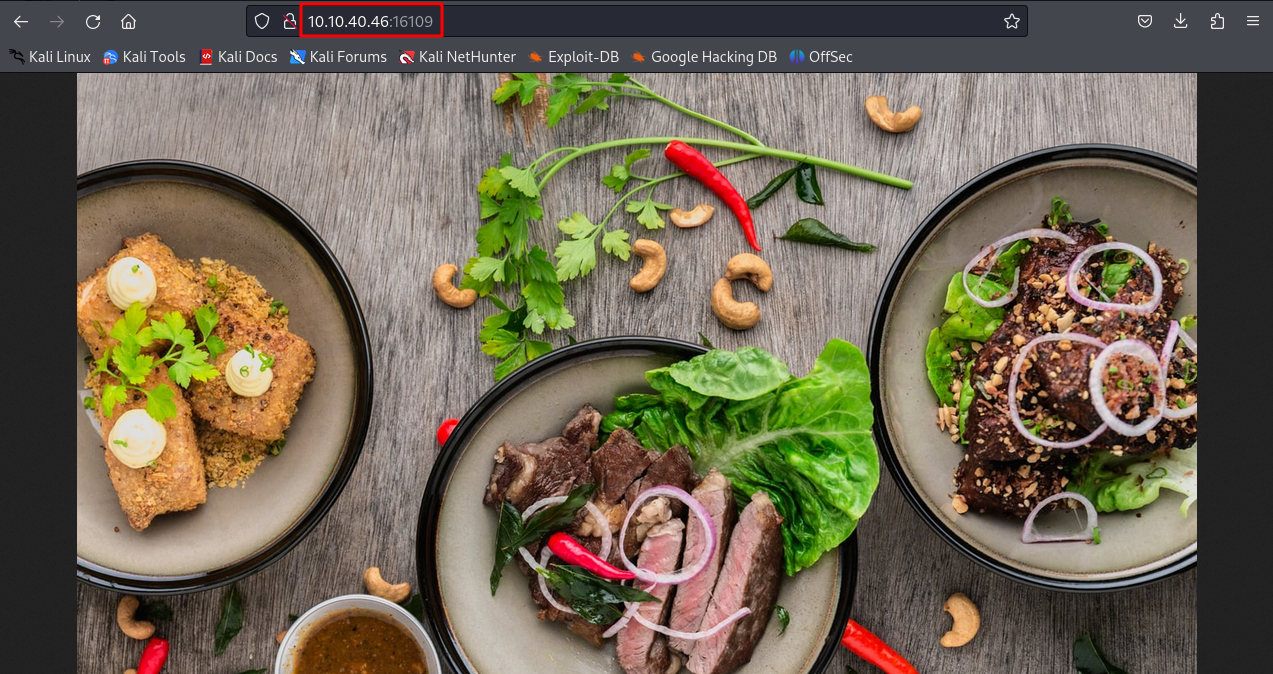
Food koth tryhackme
Join the Food KOTH challenge on TryHackMe to capture flags and sharpen your hacking skills.