What is SQL Injection (SQLi)?
SQL Injection (SQLi) is a critical web vulnerability that manipulates a website’s interaction with its database. By injecting malicious SQL statements into input fields, attackers can bypass authentication, exfiltrate sensitive data, modify or delete records, and even execute administrative operations on the database.
Impact:
- Unauthorized data access (e.g., usernames, passwords, credit card details)
- Data corruption or deletion
- Administrative account compromise
- Full server compromise if the database is connected to the operating system
How SQL Injection Works
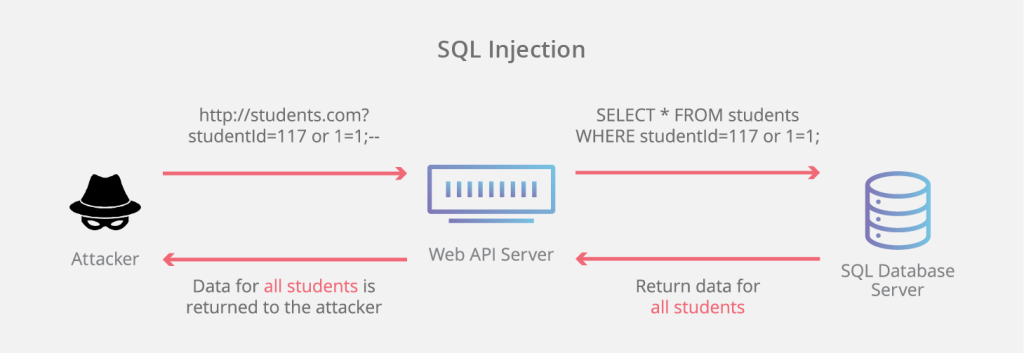
Example Query in Action:
SELECT * FROM users WHERE username = 'input_username' AND password = 'input_password';Malicious Input:
' OR '1'='1
This transforms the query into:
SELECT * FROM users WHERE username = '' OR '1'='1' AND password = '';
Here, '1'='1' is always true, allowing attackers to bypass authentication.
Types of SQL Injection
- Classic SQL Injection:
Directly inject SQL payloads into an application’s input fields to manipulate queries. - Error-Based SQL Injection:
Relies on error messages from the database to extract information.
- Example: Inputting
"'results in a message likeSyntax error near ' at line 1.
- Union-Based SQL Injection:
Combines the results of multiple queries using theUNIONoperator.
- Payload:
plaintext ' UNION SELECT null, username, password FROM users --
- Blind SQL Injection:
The application doesn’t return data directly but behaves differently based on query results.
- Example:
plaintext ' AND 1=1 --
(Success implies the query is valid.)
- Time-Based Blind SQL Injection:
Exploits delays to infer database responses.
- Payload:
sql ' AND IF(1=1, SLEEP(5), 0) --
- Out-of-Band SQL Injection:
Uses alternate channels (e.g., DNS requests) to exfiltrate data.
Real-World Impacts of SQL Injection
- Data Breaches:
Attackers retrieve sensitive data like user credentials, PII, and financial details. - Authentication Bypass:
By crafting specific payloads, attackers gain unauthorized access to accounts. - Account Takeover:
Exploiting SQLi vulnerabilities in admin panels can allow attackers to reset or hijack accounts. - Data Tampering:
SQLi enables modification or deletion of critical data, disrupting operations. - Privilege Escalation:
Exploiting database configuration flaws can allow attackers to execute OS-level commands. - Denial of Service (DoS):
Injecting resource-intensive queries can crash the database or application. - Spreading Malware:
SQLi can inject malicious scripts into database-stored content, leading to cross-site scripting (XSS).
Practical SQL Injection Examples
1. Basic SQL Injection:
Payload for Login Bypass:
' OR '1'='1 --
Transforms query into:SELECT * FROM users WHERE username = '' OR '1'='1' AND password = '';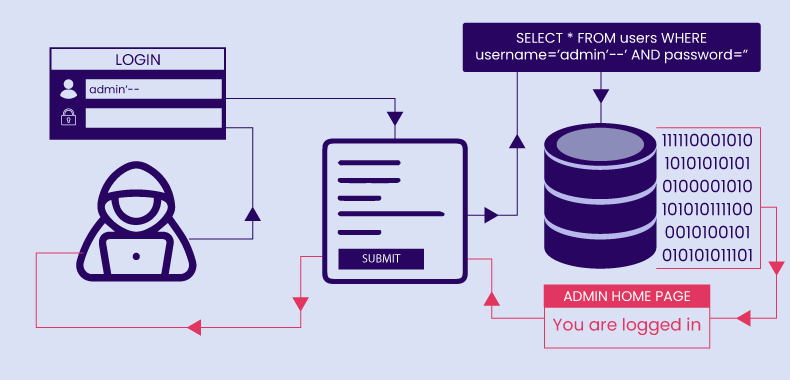
2. Finding Number of Columns (Union-Based):
http://<domain>.com/products?id=1 ORDER BY 3 --Options Breakdown:
ORDER BY: Tests the number of columnsIf the page breaks at ORDER BY 4, there are 3 columns.
3. Extracting Data with UNION SELECT:
http://<domain>.com/products?id=1 UNION SELECT null, username, password FROM users --SQL Injection Vulnerabilities
Common Bugs Exploited by SQL Injection
- Improper Input Sanitization:
Applications directly insert user inputs into queries without validation. - Lack of Parameterized Queries:
Failing to use prepared statements allows direct query manipulation. - Excessive Database Permissions:
Applications running with high privileges (e.g.,root) increase the impact of SQLi. - Verbose Error Messages:
Revealing database errors exposes valuable information for attackers. - Unrestricted Data Queries:
Allowing unrestricted use of operators likeUNIONor subqueries. - Dynamic Query Building:
Using concatenation for query strings opens the door to SQLi.
How to Test for SQL Injection
Manual Testing:
- Use special characters like
',",--,#in input fields to observe behavior. - Modify URL parameters to inject payloads.
Tools for Automated Testing:
- SQLMap:
sqlmap -u "http://<domain>.com/products?id=1" --dbs- Burp Suite: Proxy requests to manipulate parameters and identify vulnerabilities.
- OWASP ZAP: Open-source tool for automated web vulnerability scanning.
Preventing SQL Injection
- Use Parameterized Queries:
Always use placeholders in SQL queries.
Example in Python:
cursor.execute("SELECT * FROM users WHERE username = %s AND password = %s", (username, password))- Validate User Input:
Reject inputs that don’t meet strict validation criteria. - Limit Database Privileges:
Assign minimum permissions to application database users. - Implement Escaping:
Use database-specific escaping functions to handle special characters. - Use Web Application Firewalls (WAFs):
WAFs like ModSecurity can detect and block malicious SQL queries. - Monitor and Log Database Activity:
Track unusual or unauthorized queries to identify potential breaches. - Use ORM Frameworks:
Frameworks like Django ORM and SQLAlchemy abstract SQL queries.