Introduction
In the digital age, passwords are the gatekeepers of our personal and professional information. Password hashing is one of the most effective ways to protect this sensitive data. However, no system is completely foolproof, and attackers constantly try to crack these hashes. To safeguard our systems, it’s crucial to understand the principles of hashing, how attackers crack passwords, and the best methods to strengthen our defenses.
This article will not only explain how password hashes are created and used but will also show you how they can be cracked, using practical examples and tools. If you’re a security enthusiast or a developer, this guide will help you understand the key concepts and challenges around password hashing and cracking.
What is Password Hashing?
In simple terms, password hashing is a one-way cryptographic function that converts a password into a fixed-length string, which is then stored in the system’s database. The primary purpose of hashing is to ensure that even if the data is compromised, the original password cannot be easily retrieved.
Unlike encryption, which can be reversed, a hash is designed to be irreversible. Once hashed, a password can’t be directly converted back to its original form. But the challenge comes in cracking these hashes, which is why strong hashing methods are necessary.
1. Cracking MD5 Hashes
- Example Hash: f74a10e1d6b2f32a47b8bcb53dac5345
- MD5 hashes are fast to crack because of their simplicity. Using Hashcat, an attacker can attempt to match the hash to a precompiled list of possible passwords (dictionary attack) or attempt all possible combinations (brute-force).
hashcat -m 0 -a 0 <hashfile.txt> /path/to/rockyou.txt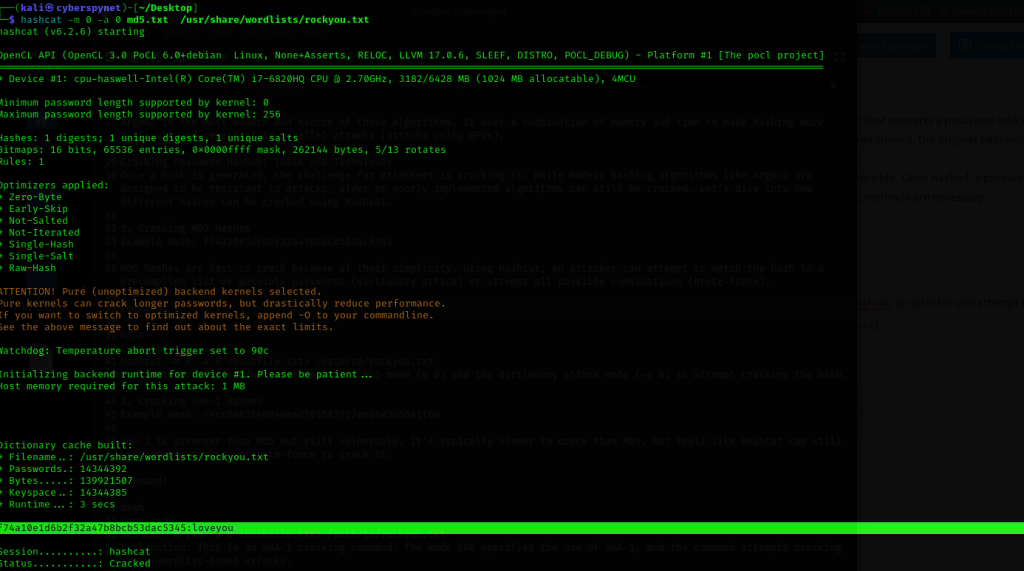
Explanation: This command uses Hashcat’s MD5 mode (m 0) and the dictionary attack mode (-a 0) to attempt cracking the hash.
2. Cracking SHA-1 Hashes
- Example Hash: f4cc6e82140048ead7015f2917eb56e3e50a1f00
- SHA-1 is stronger than MD5 but still vulnerable. It’s typically slower to crack than MD5, but tools like Hashcat can still use rainbow tables or brute-force to crack it.
hashcat -m 100 -a 0 <hashfile.txt> /path/to/rockyou.txt
Explanation: This is an SHA-1 cracking command. The mode 100 specifies the use of SHA-1, and the command attempts cracking using wordlist-based attacks.
3. Cracking SHA-256 Hashes
- Example Hash: 848be944013cc3374ddfef3655d6816c060610161c835c71a9665e6dc18f6542
- SHA-256, part of the SHA-2 family, is significantly stronger than MD5 and SHA-1. It takes more computational resources to crack but is still not immune to brute force.
hashcat -m 1400 -a 0 <hashfile.txt> /path/to/rockyou.txt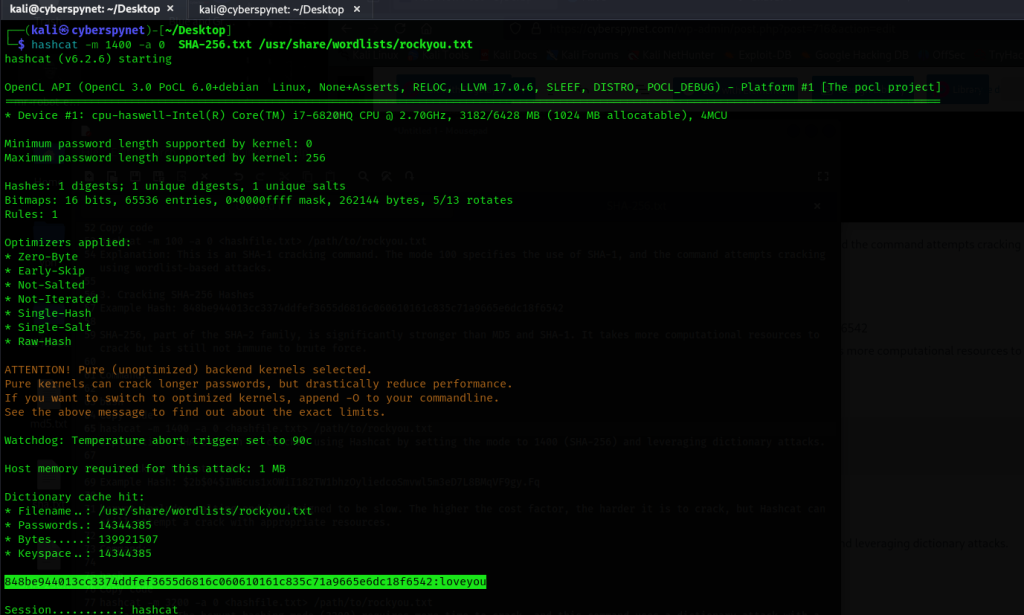
Explanation: SHA-256 can be cracked using Hashcat by setting the mode to 1400 (SHA-256) and leveraging dictionary attacks.
4. Cracking bcrypt Hashes
- Example Hash: $2b$04$IWBcus1xOWiI182TW1bhzOyliedcoSmvwl5m3eD7L8BMqVF9gy.Fq
- bcrypt includes salting and is designed to be slow. The higher the cost factor, the harder it is to crack, but Hashcat can still attempt a crack with appropriate resources.
hashcat -m 3200 -a 0 <hashfile.txt> /path/to/rockyou.txt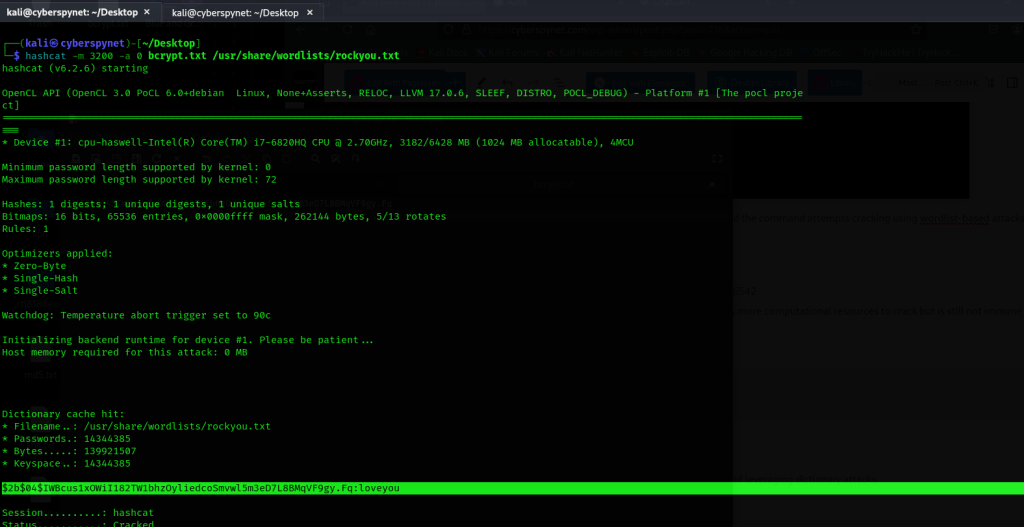
Explanation: The bcrypt hashing mode (3200) requires more time to crack, and this command uses a dictionary attack with a given wordlist.
5. Cracking Argon2 Hashes
- Example Hash: $argon2id$v=19$m=8,t=1,p=1$xP+9PrFOhw4X5XTzv5YmNw$Fjz2KVAFENCX31iMD7SxBMRN1iADI1Eak55kg16YfRY
- Argon2 is the most secure algorithm and designed to resist attacks by using memory-hard operations. Cracking Argon2 hashes requires substantial resources.
hashcat -m 20710 -a 0 <hashfile.txt> /path/to/rockyou.txtExplanation: Argon2 (mode 20710) requires significant memory and time to crack, but Hashcat can still attempt brute-force or dictionary-based attacks.
Conclusion: Strengthening Password Security
- The process of cracking password hashes highlights the need for secure password storage. While MD5 and SHA-1 are now outdated and insecure, more modern algorithms like SHA-256, bcrypt, and Argon2 provide better protection.
Disclaimer
- This guide is for educational purposes only. CyberSpynet does not endorse any illegal or unethical use of password cracking techniques. All demonstrations are intended to raise awareness about security vulnerabilities and promote responsible use of cybersecurity knowledge in compliance with the law.