Subdomain enumeration is a crucial part of reconnaissance in cybersecurity assessments. It involves identifying all the subdomains associated with a target domain. These subdomains can reveal valuable information about the target’s infrastructure, expose hidden services, and uncover potential vulnerabilities. This blog will guide you through subdomain enumeration techniques, tools, and best practices.
What is Subdomain Enumeration?
Subdomain enumeration is the process of discovering subdomains of a domain. For example, if the domain is example.com, subdomains like api.example.com, admin.example.com, or dev.example.com may exist. These subdomains often host different services and can provide attack vectors for penetration testers and bug bounty hunters.
Why is Subdomain Enumeration Important?
- Discover Hidden Services: Many organizations host critical services on subdomains that are not publicly advertised.
- Identify Attack Surfaces: Subdomains might expose unpatched or misconfigured applications.
- Understand Infrastructure: It provides insights into the structure and scope of the organization’s online presence.
- Gain an Edge in Bug Bounty Hunting: Bug bounty platforms often reward findings on lesser-known subdomains.
Techniques for Subdomain Enumeration
1. Passive Enumeration
Passive enumeration involves gathering information without directly interacting with the target server. It includes:
- Search Engines: Use search queries like
site:google.com to find indexed subdomains. - Certificate Transparency Logs: Sites like crt.sh list domains and subdomains associated with SSL certificates.
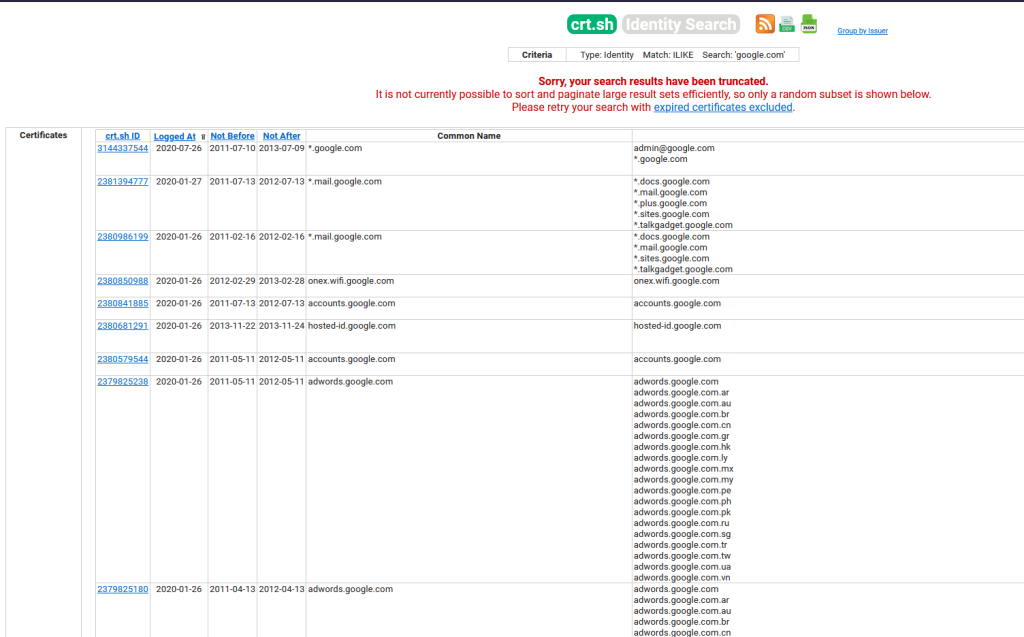
- DNS Dumps: Tools like virustotal can reveal DNS records.
- Public Repositories: Look for subdomains in GitHub or public forums.
2. Active Enumeration
Active enumeration involves querying the target domain for subdomain information. This may include:
- DNS Brute-forcing: Use a wordlist to guess subdomains.
- Zone Transfers: Exploit DNS misconfigurations to retrieve zone files.
- Subdomain Takeover Detection: Identify orphaned subdomains pointing to unclaimed resources.
Tools for Subdomain Enumeration
1. Amass
Amass is a powerful tool for discovering subdomains and mapping an organization’s external assets.
Example:
amass enum -d example.com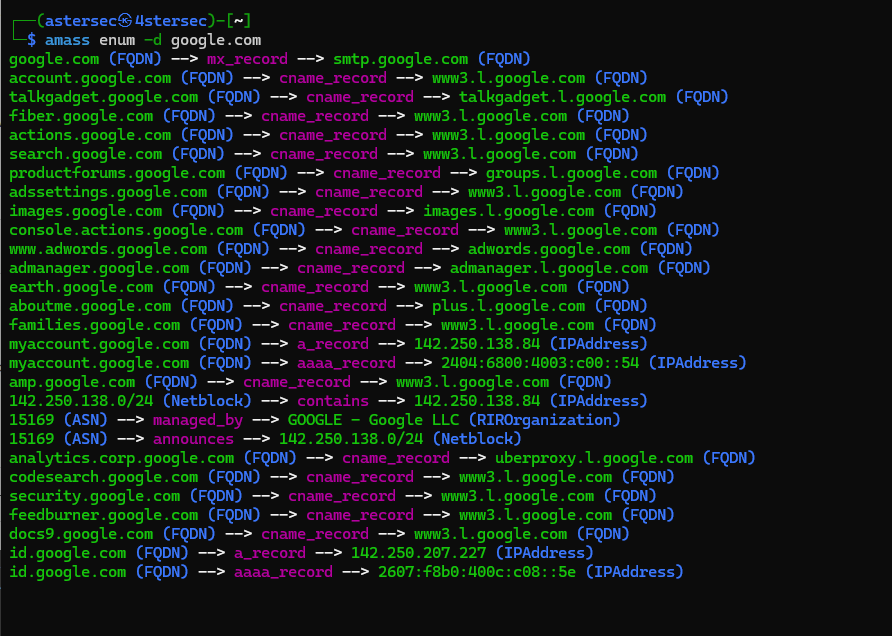
2. Sublist3r
Sublist3r is a Python-based tool for subdomain enumeration.
Example:
sublist3r -d example.com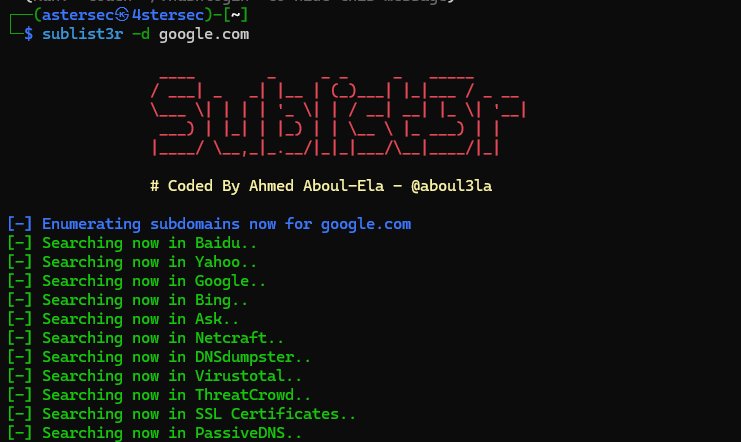
3. DNSRecon
DNSRecon is used for DNS enumeration, including subdomain discovery and zone transfers.
Example:
dnsrecon -d example.com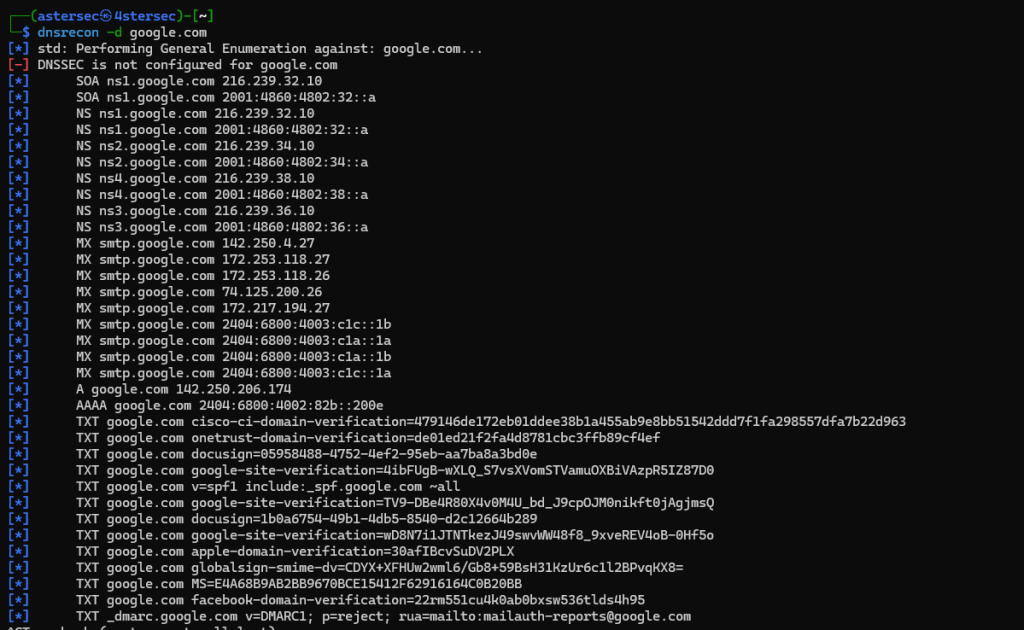
4. Assetfinder
Assetfinder is a fast tool for subdomain discovery.
Example:
assetfinder --subs-only example.com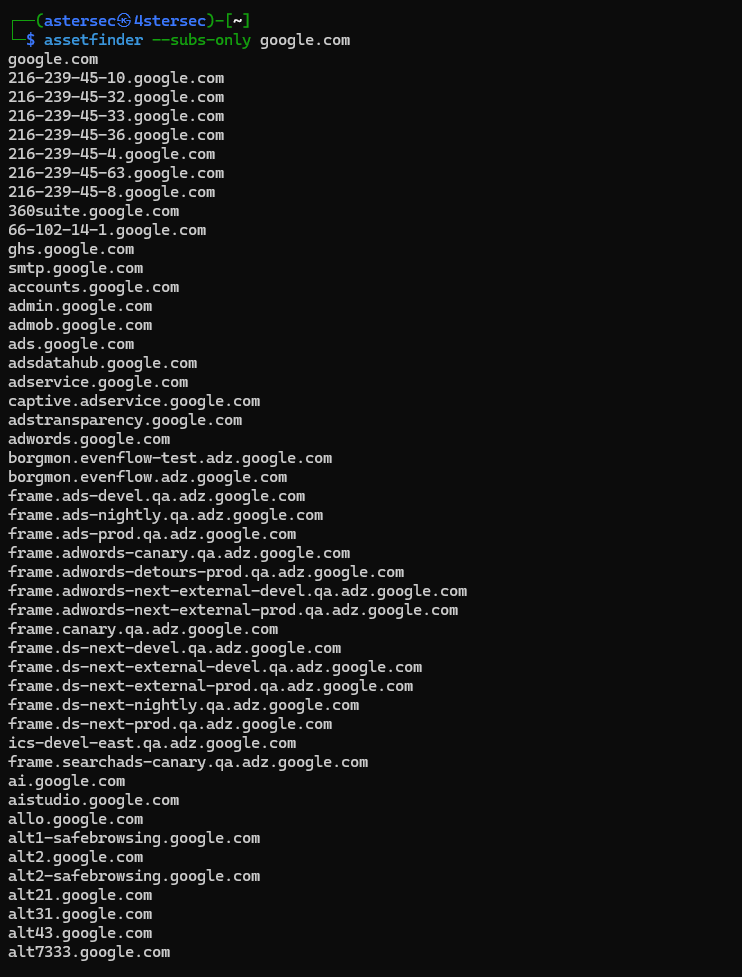
Best Practices for Subdomain Enumeration
- Combine Tools: Use multiple tools to ensure comprehensive coverage.
- Validate Findings: Verify discovered subdomains for accuracy and accessibility.
- Respect Boundaries: Always operate within the legal and ethical scope of the engagement.
- Document Results: Keep detailed records of subdomains, including their IP addresses and services.