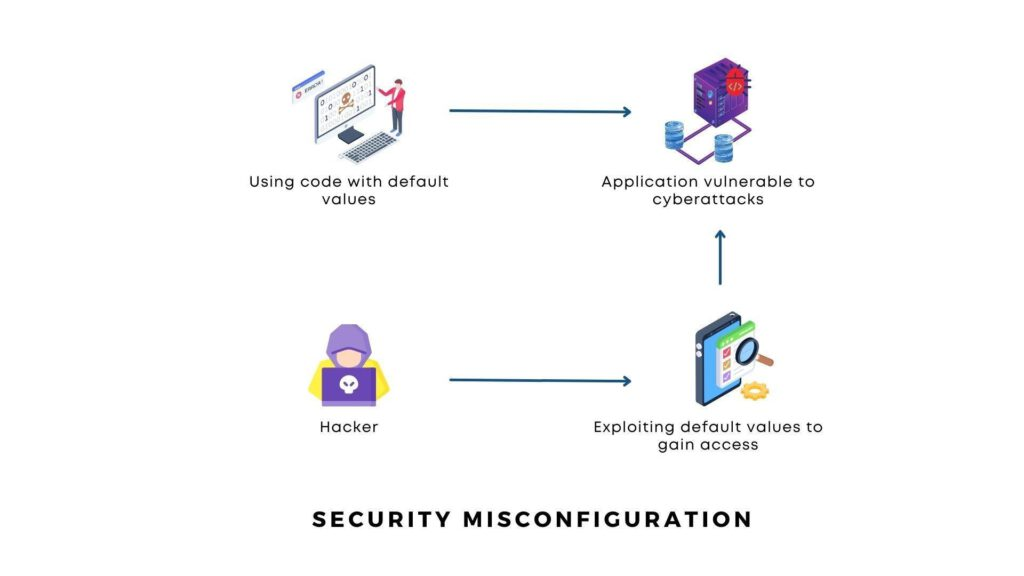
What is Security Misconfiguration?
Security misconfiguration occurs when an application, server, or database is insecurely configured, leaving it vulnerable to attacks. This type of vulnerability is often the result of incorrect or incomplete configuration settings in software, hardware, or the underlying infrastructure. While security configurations are meant to safeguard sensitive data and ensure secure access, misconfigurations can inadvertently expose the system to a range of attacks, such as unauthorized access, data breaches, and more.
Security misconfigurations can occur at any level of the application stack, including network, database, web servers, application servers, and cloud environments.
Common Causes of Security Misconfiguration
- Default Settings Left Unchanged
- Many systems come with default settings that are not secure. These can include weak passwords, unnecessary services enabled, and open ports that allow unauthorized access.
- Example: A web server with default admin credentials left unchanged, allowing attackers to easily gain access.
- Exposed Error Messages
- When error messages display stack traces or debug information, they can inadvertently reveal sensitive information about the system, including the underlying architecture, software versions, and configuration details.
- Example: An application that reveals its full directory structure and database details in the error message when something goes wrong.
- Overly Permissive Permissions
- Over-permissioning occurs when an application or database is given more privileges than necessary. This can expose sensitive data or allow attackers to exploit vulnerabilities to gain unauthorized access.
- Example: A database user with administrative privileges when the application only requires read-only access.
- Unnecessary Services or Ports Open
- Applications often leave unnecessary ports open or services enabled that aren’t required for normal operations, increasing the attack surface.
- Example: An application exposing unused management ports, like FTP or SSH, to the public without adequate security controls.
- Incomplete Security Hardening
- Failing to implement security hardening measures, such as disabling unused features, applying security patches, or using strong encryption, leaves the system vulnerable to attacks.
- Example: A web server running without encryption (HTTP instead of HTTPS) or missing patches for known vulnerabilities.
- Cloud Security Misconfigurations
- With cloud services, misconfigurations can easily occur due to complex permission models and settings. Public cloud services sometimes have default settings that allow broad access to resources if not properly configured.
- Example: Storing sensitive data in a publicly accessible S3 bucket without configuring appropriate access controls.
Real-World Examples of Security Misconfiguration
- GitHub’s Public API Key Leak (2019)
A developer accidentally uploaded an API key to a public GitHub repository, which was then indexed by search engines. This exposed private data from a production environment. This mistake occurred due to a misconfiguration in version control management. - AWS S3 Bucket Data Breach (2017)
Misconfigured AWS S3 buckets resulted in sensitive data leaks. Many companies mistakenly configured their S3 buckets to be publicly accessible, exposing personal data, financial records, and other sensitive information. - Apache Struts Vulnerability (2017)
The Apache Struts vulnerability, which led to the Equifax data breach, was caused by a security misconfiguration in the application’s web server. The failure to update an outdated software version allowed attackers to exploit known vulnerabilities.
How to Prevent Security Misconfigurations
- Automated Configuration Management Tools
Use tools like Ansible, Chef, or Puppet to automate configuration and ensure that systems are consistently configured securely, avoiding human error. - Enforce the Principle of Least Privilege
Only grant necessary permissions to users, services, and applications. This helps minimize the attack surface by restricting access to sensitive data and functionality. - Regular Security Audits and Penetration Testing
Conduct routine security audits and penetration tests to detect and correct configuration errors before attackers can exploit them. - Use Secure Defaults
Always configure software and systems with secure settings from the start. Change default passwords, disable unnecessary services, and close unused ports. - Keep Systems and Software Up-to-Date
Ensure all systems, services, and software are updated regularly with the latest security patches to close any potential vulnerabilities. - Implement Error Handling Best Practices
Configure applications to avoid revealing stack traces and sensitive information in error messages. Use custom error pages that provide minimal information to the user. - Use Security Hardening Guidelines
Follow security hardening guidelines for servers, databases, and applications. The OWASP Security Knowledge Framework and CIS Benchmarks provide specific configuration practices to help secure your environment. - Regularly Review Cloud Settings
For cloud services, ensure that access controls and permissions are regularly reviewed. Tools like AWS Config or Azure Security Center can help identify misconfigurations in cloud environments.
How to Detect Security Misconfigurations
- Automated Scanning Tools
Tools like Nessus, Qualys, and OpenVAS can automatically scan systems for misconfigurations, outdated software, open ports, and other vulnerabilities. - Manual Configuration Reviews
Regularly audit system configurations manually, checking for common misconfigurations like weak passwords, exposed services, or improperly set access control policies. - Use of Monitoring Tools
Implement continuous monitoring using tools like Splunk, Nagios, or OSSEC to track abnormal behavior or unauthorized changes in system configurations. - Cloud Configuration Auditing
Use cloud-native tools such as AWS Trusted Advisor or Azure Security Center to detect misconfigured cloud resources and services that could expose vulnerabilities.