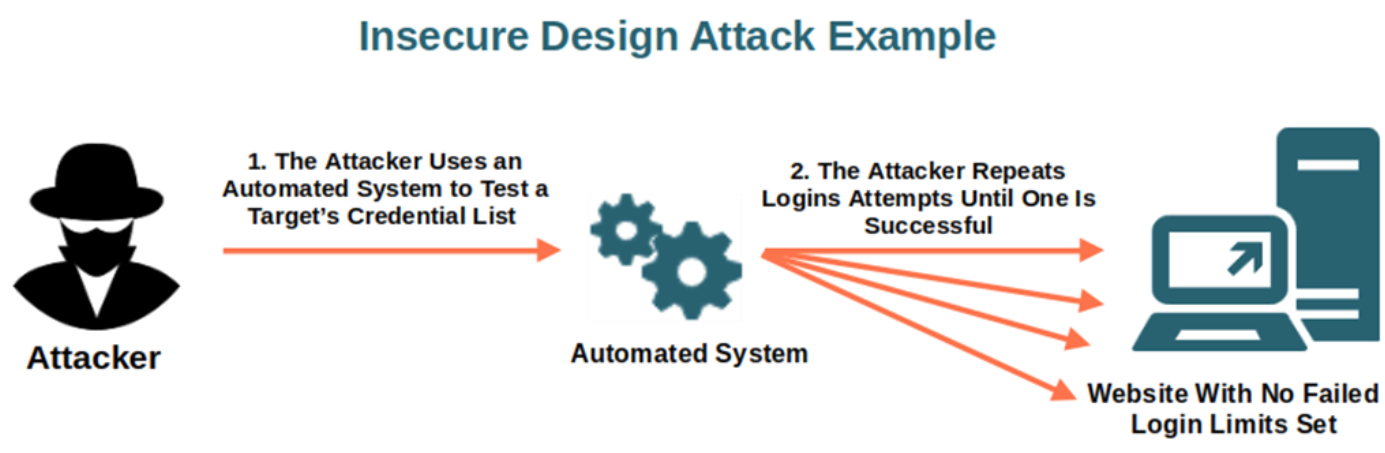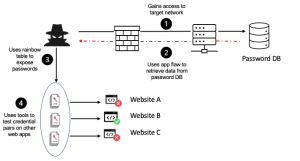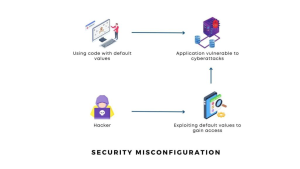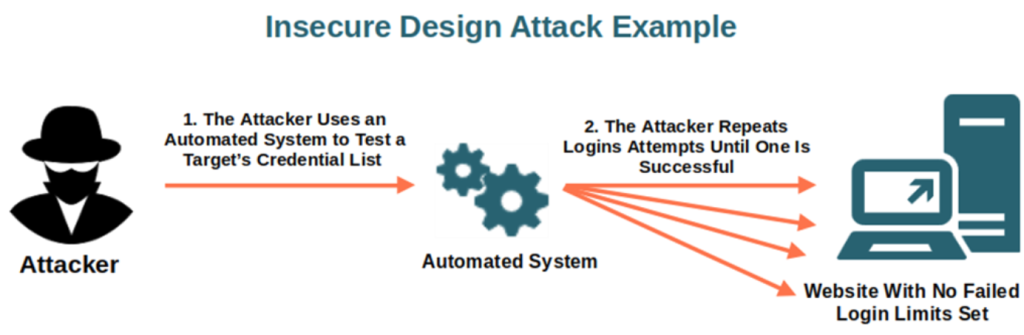
What is Insecure Design?
Insecure design refers to a flaw in the architecture of a system that makes it vulnerable to exploitation. This typically occurs when the system’s design fails to consider security as a fundamental part of its structure. Unlike implementation bugs (like those caused by coding errors), insecure design vulnerabilities exist in the foundational elements of the application or infrastructure.
These flaws can lead to data leaks, unauthorized access, privilege escalation, and a variety of other serious security breaches.
Common Causes of Insecure Design
Insecure design issues are often rooted in fundamental mistakes made during the planning or blueprinting stages of a system’s architecture. Some of the common causes include:
- Lack of Secure Authentication and Authorization Models
Poor design decisions related to how users authenticate and what resources they can access. For example, allowing unauthenticated access to sensitive endpoints or improperly managing user roles and permissions. Example:
- Admin Access: An application design where regular users can access admin features simply by modifying a URL or manipulating request parameters.
- Hardcoded Credentials
Hardcoding sensitive data, such as API keys, passwords, or database credentials, directly in the application code. This makes it easy for attackers to extract these values if they gain access to the code. Example:
- Hardcoded API Keys: A developer embeds API keys in the source code for ease of use, leaving them exposed to anyone who has access to the code or repositories.
- Lack of Input Validation
Failing to validate or sanitize user input at the design stage, leaving the application vulnerable to common attacks like SQL injection, XSS, or buffer overflow attacks. Example:
- A web application that doesn’t sanitize user input in search fields, allowing an attacker to inject malicious code or queries.
- Unencrypted Data Transmission
Designing systems that transmit sensitive data (such as passwords, financial information, or personal details) without encryption, or using weak encryption methods. Example:
- An application that sends login credentials over HTTP instead of HTTPS, making them vulnerable to man-in-the-middle (MITM) attacks.
- Failure to Implement Proper Access Controls
If the application is designed without granular access controls, users may be able to access resources or data they shouldn’t be allowed to view. Example:
- A user who can view files uploaded by other users without proper permissions, exposing sensitive information to unauthorized individuals.
- Poor Session Management
Insecure design can result in weak session handling mechanisms, such as failure to expire sessions properly or not using secure session identifiers. Example:
- A user can stay logged in indefinitely even after logging out, or session tokens are predictable, enabling attackers to hijack the session.
Real-World Examples of Insecure Design
- Facebook API Bug (2018)
A bug in the Facebook API exposed users’ personal photos to third-party apps. The insecure design allowed apps to access photos that users had never shared publicly, leading to a massive data leak. - Uber Data Breach (2016)
Uber’s poor design allowed a group of attackers to access the personal data of 57 million Uber users. The design flaw involved a compromised AWS key that was hardcoded into the code and lacked proper access control. - Capital One Breach (2019)
In this case, a vulnerability in the design of Capital One’s cloud infrastructure allowed a former employee of a third-party contractor to access sensitive data of over 100 million customers. The design flaw was related to misconfigured firewalls and access permissions.
How to Prevent Insecure Design Vulnerabilities
- Adopt Secure Design Principles
Design systems with security in mind from the start. Use frameworks like OWASP’s Secure Software Development Lifecycle (SDLC) to integrate security measures at every stage of the design and development process. - Use Proper Authentication and Authorization
Implement strong multi-factor authentication (MFA), utilize robust session management practices, and ensure role-based access control (RBAC) is applied throughout the system. - Encrypt Sensitive Data
Always encrypt sensitive data both in transit and at rest using modern cryptographic protocols (e.g., TLS 1.2 or higher for transport encryption, and AES for data storage). Avoid transmitting sensitive data over insecure protocols like HTTP. - Validate User Input and Use Prepared Statements
Always validate user inputs (e.g., using whitelists, regex patterns) and employ parameterized queries to protect against SQL injection and other common attacks. - Conduct Security Threat Modeling
Perform regular threat modeling exercises during the design phase to anticipate potential attack vectors and ensure your application is resilient to known and unknown threats. - Regular Security Audits and Penetration Testing
Regularly audit your application design and conduct penetration tests to identify potential design flaws before they are exploited by attackers.
How to Detect Insecure Design Vulnerabilities
- Security Audits
Perform detailed security reviews at the design stage. This should include a thorough check of data flows, authentication mechanisms, access control measures, and the use of encryption. - Penetration Testing
Penetration testing can reveal insecure design flaws in an application. Test for vulnerabilities like improper authentication flows, hardcoded credentials, and weak session management practices. - Threat Modeling
Use threat modeling tools and frameworks (such as STRIDE) to identify and mitigate design flaws early in the development cycle. - Automated Static Analysis
Tools like Checkmarx, Veracode, or SonarQube can help detect insecure design patterns, such as hardcoded credentials or poor session management, in the codebase.