The Surface Web, Deep Web, and Dark Web: A Comprehensive Guide
The Surface Web, Deep Web, and Dark Web form three distinct layers of the internet, each with its own unique characteristics and risks. While the surface web is what most…
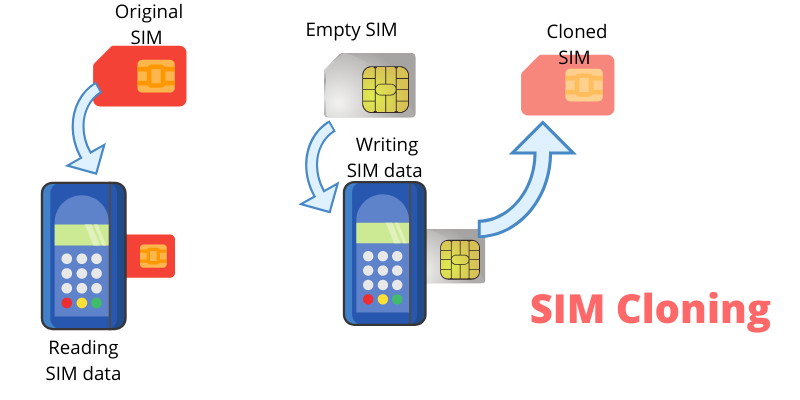
SIM Cloning and Its Mitigations: Understanding the Threat and How to Protect Yourself
SIM cloning is a dangerous and growing threat that can compromise your privacy, security, and financial safety. However, by taking proactive steps to protect yourself, such as using stronger authentication…
Understanding Call Spoofing Attacks: How It Works, Real-Life Examples, and Protection Methods
By understanding call spoofing, recognizing the signs of a scam, and taking preventative measures, you can protect yourself and your loved ones from falling prey to this modern digital deception.
Linux for Beginners Master the Linux Command Line: A Beginner’s Guide to Essential Commands.
Unlock the full potential of Kali Linux with advanced penetration testing and ethical hacking techniques. Master its powerful tools and commands to perform in-depth security assessments and enhance your cybersecurity…
android hacking : Unlocking android hacking : Ethical Hacking with Metasploit
Metasploit and MSFvenom are essential tools for ethical hackers, offering a streamlined way to create payloads and test vulnerabilities. From generating Android-specific payloads to exploiting potential weaknesses, these tools help…
Mail Spoofing Attack: Understanding SMTP-based Email Spoofing and How to Defend Against It
Email spoofing via SMTP is a common and dangerous attack technique used by cybercriminals to deceive recipients and gain access to sensitive information. While SMTP itself is not inherently insecure,…
SQLmap: The Ultimate Guide for Penetration Testing and SQL Injection
SQLmap is one of the most powerful and versatile tools in a penetration tester's toolkit. It automates the process of finding and exploiting SQL injection vulnerabilities, making it easier for…
Gobuster: A Comprehensive Guide for Cybersecurity Professionals
Gobuster is a versatile and powerful tool for cybersecurity professionals, enabling efficient and fast directory brute-forcing and subdomain enumeration. Whether you're conducting a penetration test or performing a vulnerability assessment,…
Mastering Wi-Fi Security: The Art of Cracking WPA2 Passwords
Unlock the secrets of Wi-Fi security with this guide on ethical hacking and password cracking techniques. Learn how to test your network, capture WPA2 handshakes, and use powerful wordlists to…
RootMe TryHackMe Writeup
This walkthrough covered the essential steps for exploiting vulnerabilities on the RootMe machine, including scanning for open ports, exploiting a web server, gaining a reverse shell, escalating privileges, and ultimately…