Backdoor Accounts on Routers: A Hidden Cybersecurity Threat
A backdoor account on a router is a hidden user account created by the manufacturer, developer, or a hacker. This account allows someone to log in to the router and…
Bug Bounty : Subdomain Enumeration
Subdomain enumeration is a crucial part of reconnaissance in cybersecurity assessments. It involves identifying all the subdomains associated with a target domain. These subdomains can reveal valuable information about the…
Bug Bounty: Web Technology Identification
Introduction In the fast-evolving landscape of web technology, identifying the tools, frameworks, and platforms used by websites can provide valuable insights for developers, security professionals, and tech enthusiasts alike. Understanding…
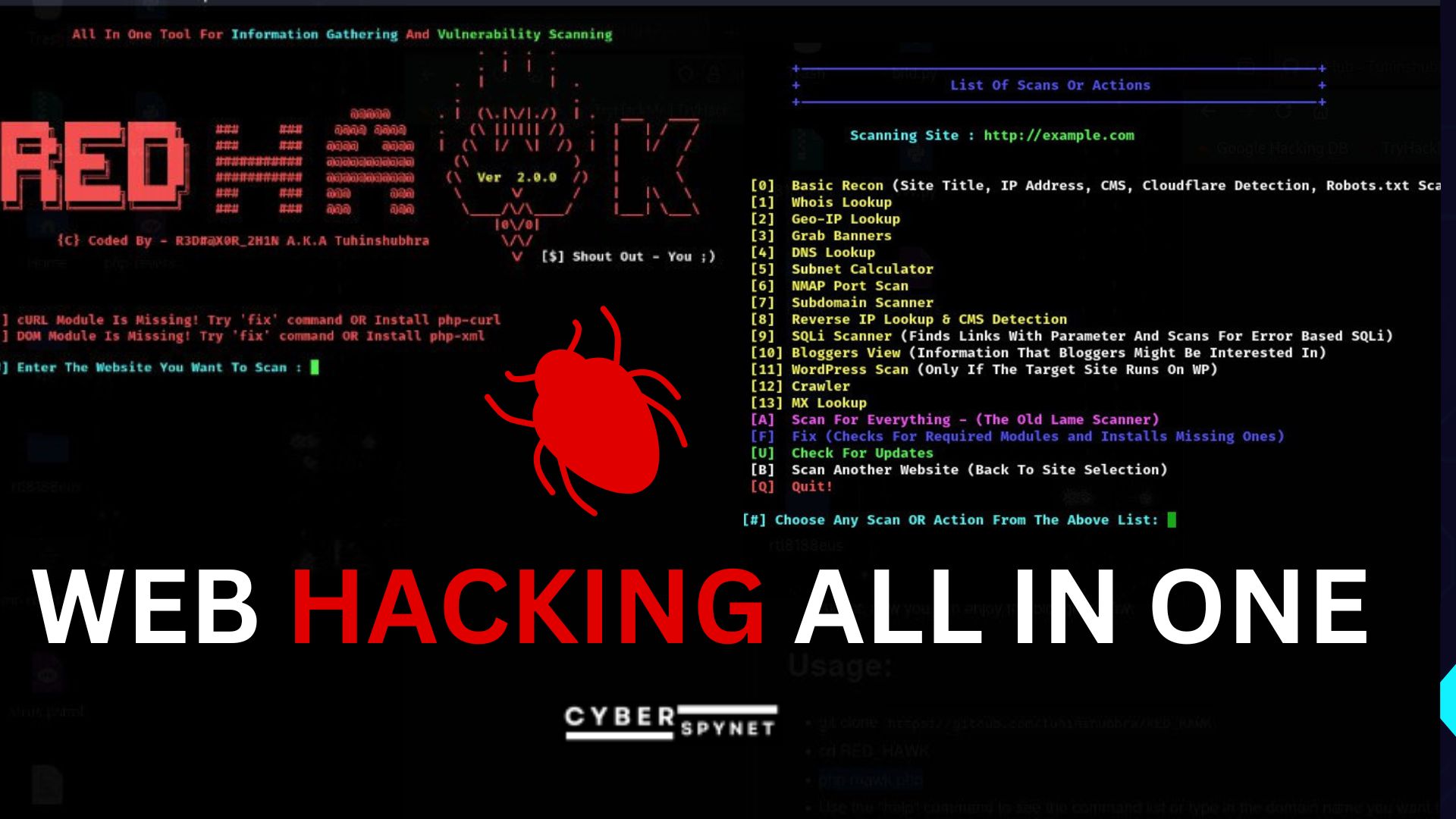
Web Hacking: RedHawk the All-in-One Tool for Ethical Hackers
Redhawk tools are designed to assist in ethical hacking and security testing for websites and web applications. These tools allow users to perform a range of scans to identify vulnerabilities…
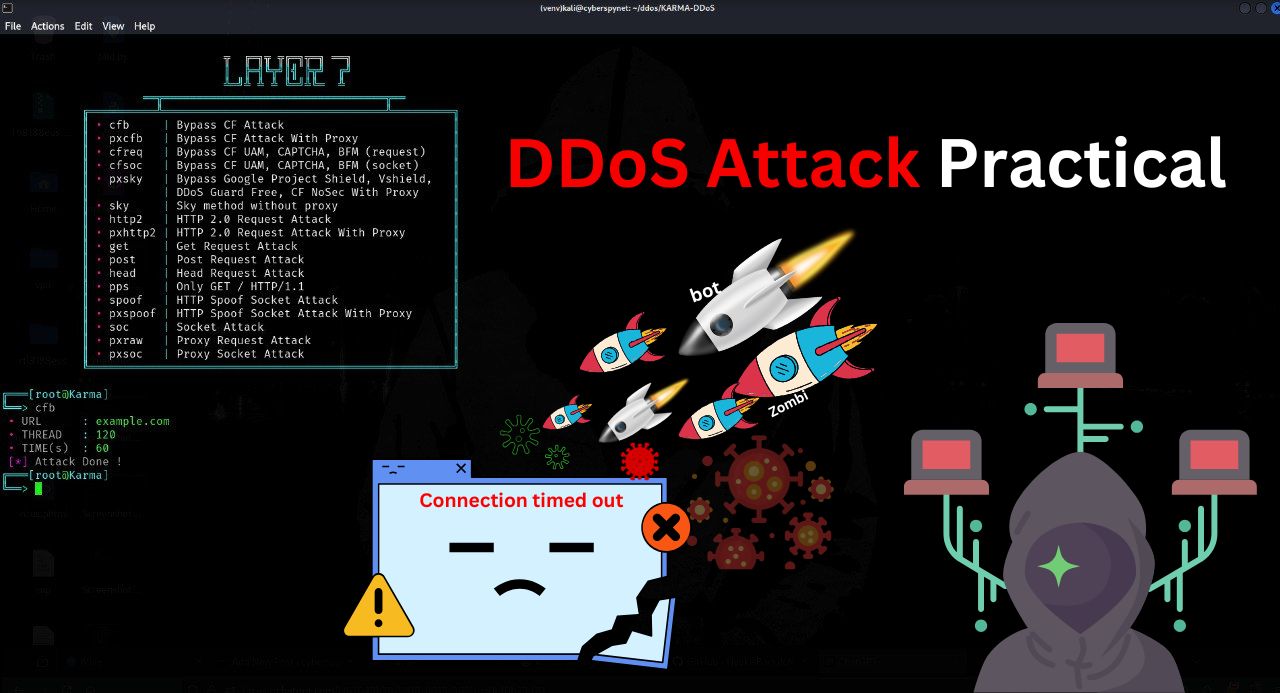
DDoS Attack Practical Guide: Performing a Website Attack Simulation
Learn how to simulate a DDoS attack on a website using the KARMA-DDoS tool in this step-by-step guide. Designed for educational and ethical testing purposes, this guide helps you understand…
Location Tracking : How Hacker can track anyone’s Location
In this blog we have covered how we are able to track anyone's location just by sending the links to victim.
What is a Web Application Firewall (WAF)? || WAF CheatSheet
A Web Application Firewall (WAF) is a special kind of firewall that protects web applications from malicious attacks. It sits in front of your web application, like a mediator, and…
How to Start Creating Tools with Any Programming Language as a Beginner
Want to learn how to create practical tools using programming languages? This beginner-friendly guide walks you through the process of building your own tools with Python, JavaScript, and more. Discover…
Digital Forensics: Importance, Scope, and Career Opportunities
Discover the importance of digital forensics, explore career opportunities in the field, and understand salary expectations for professionals in this growing industry.
Digital Forensics: An Introduction and Historical Evolution
This article outlines the evolution of digital forensics, from the 1978 Florida Computer Crimes Act to modern challenges like ransomware and cloud forensics. It highlights pioneers like Dr. Eric H.…