Hacking is often depicted as a mysterious and secretive activity, but in reality, it follows a clear and structured process. Ethical hackers, penetration testers, and cybercriminals alike follow similar stages in their approach to gaining unauthorized access to systems and data. Understanding these stages is not only important for cybersecurity professionals but also for anyone interested in learning about hacking from a defensive perspective.
In this blog, we will take you through the five stages of hacking, explain each phase in detail, and provide insights on how to protect yourself and your organization from these attacks.
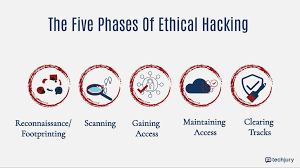
1. Reconnaissance (Information Gathering)
Reconnaissance is the first and most crucial stage of any hacking attempt. It’s often referred to as footprinting or information gathering. During this phase, the hacker collects as much information as possible about the target system, organization, or individual. The goal is to gather publicly available data that can be used to identify vulnerabilities or weaknesses in the system.
Types of Reconnaissance:
- Passive Reconnaissance: The hacker gathers information without directly interacting with the target system. This involves collecting data from public sources like websites, social media profiles, domain registration records (WHOIS), job postings, and more.
- Active Reconnaissance: In this phase, the hacker interacts directly with the target system, such as conducting network scans, ping sweeps, or DNS queries to gather more technical details like IP addresses, open ports, and services.
Tools Used:
- Google Dorks (Advanced Google search operators to find sensitive information)
- Shodan (Search engine for Internet of Things (IoT) devices)
- Whois (Domain registration lookup)
- Nmap (Network scanning tool)
Defensive Measures:
- Regularly audit your organization’s public-facing assets.
- Use services like Shodan to check for exposed devices or systems.
- Limit information shared on social media and public websites.
2. Scanning (Vulnerability Assessment)
Once the hacker has gathered sufficient information, the next step is scanning. During this phase, the attacker identifies potential vulnerabilities in the system by scanning the target’s network and systems for weaknesses. This is the phase where hackers look for open ports, running services, outdated software, misconfigurations, and other potential entry points.
Types of Scanning:
- Network Scanning: The hacker checks for active devices on the network and open ports that may allow unauthorized access.
- Port Scanning: Specific attention is given to identifying open ports and services that may be vulnerable.
- Vulnerability Scanning: Automated tools scan the system for known vulnerabilities in operating systems, software, or applications.
Tools Used:
- Nmap (For network and port scanning)
- Nessus (Vulnerability scanner)
- OpenVAS (Open-source vulnerability scanner)
- Nikto (Web server scanner)
Defensive Measures:
- Regularly update and patch all software and services.
- Use firewalls to block unnecessary ports and restrict access to critical services.
- Conduct regular vulnerability assessments and penetration testing.
3. Gaining Access (Exploitation)
After identifying vulnerabilities, the next stage is gaining access. This is where the hacker actively exploits the discovered weaknesses to gain unauthorized access to the system. Exploitation can involve a variety of techniques, such as leveraging software vulnerabilities, weak passwords, or social engineering tactics to gain a foothold inside the network.
Types of Exploitation:
- Privilege Escalation: After gaining initial access, the hacker attempts to elevate their privileges to gain full administrative control of the system.
- Password Cracking: Using brute force, dictionary attacks, or social engineering to crack weak or default passwords.
- Web Application Attacks: Exploiting vulnerabilities in web applications like SQL injection, Cross-Site Scripting (XSS), or Cross-Site Request Forgery (CSRF).
Tools Used:
- Metasploit (Exploitation framework)
- Hydra (Brute force tool)
- John the Ripper (Password cracking tool)
- SQLMap (Automated SQL injection tool)
Defensive Measures:
- Use strong, complex passwords and implement multi-factor authentication (MFA).
- Employ principle of least privilege to limit user access and permissions.
- Patch vulnerabilities as soon as they’re discovered.
- Use Web Application Firewalls (WAFs) to block common exploits.
4. Maintaining Access (Persistence)
After successfully gaining access to the target system, the hacker now focuses on maintaining access. This phase involves creating a backdoor or establishing persistent access to the compromised system so that the hacker can return later, even if the initial entry point is discovered and patched.
Types of Persistence Techniques:
- Backdoors: Installing malicious software that allows the hacker to access the system remotely, even if the original vulnerability is patched.
- Rootkits: Malicious software that hides the hacker’s presence on the system, making detection more difficult.
- Scheduled Tasks: Setting up tasks or scripts to ensure continued access to the system.
Tools Used:
- Netcat (Reverse shell tool)
- Meterpreter (Payload in Metasploit used for persistent access)
- Backdoor Factory (Backdoor creation tool)
Defensive Measures:
- Use endpoint detection and response (EDR) systems to monitor for suspicious activity.
- Monitor system logs and unusual user behavior for signs of backdoors or unauthorized access.
- Implement regular system audits and maintain up-to-date antivirus software.
5. Covering Tracks (Post-Exploitation)
The final stage of hacking is covering tracks. After gaining access and exploiting the system, the hacker works to remove any evidence of their activities. This helps prevent detection by security teams and ensures that their attack remains undetected for as long as possible.
Common Techniques to Cover Tracks:
- Clearing Logs: Deleting or modifying system and security logs to remove any trace of unauthorized activities.
- Deleting Malicious Files: Erasing files and tools used during the attack, like backdoors or exploitation scripts.
- Using Encryption: Encrypting data or communications to avoid detection by monitoring tools.
Tools Used:
- LogCleaner (To erase or alter logs)
- CCleaner (Used to delete temporary files and system logs)
Defensive Measures:
- Implement centralized log management and monitoring to track unusual activities.
- Use File Integrity Monitoring (FIM) tools to detect unauthorized file modifications.
- Employ intrusion detection systems (IDS) and intrusion prevention systems (IPS) to detect abnormal behavior.