WordPress powers over 40% of all websites on the internet, making it a prime target for malicious hackers. Ethical hacking helps identify vulnerabilities before attackers can exploit them. WPScan is one of the most powerful tools for security professionals to audit WordPress installations.
What is WPScan?
WPScan is a free, open-source WordPress security scanner written in Ruby. It’s designed to help security professionals and website administrators identify vulnerabilities in WordPress installations. The tool checks for:
- Outdated WordPress core versions
- Vulnerable plugins and themes
- Weak passwords
- Misconfigurations
- Known security issues
Installing WPScan
Before using WPScan, you’ll need to install it on your system. Here’s how to install it on various platforms:
On Linux (Kali Linux/Debian-based)
sudo apt update
sudo apt install wpscan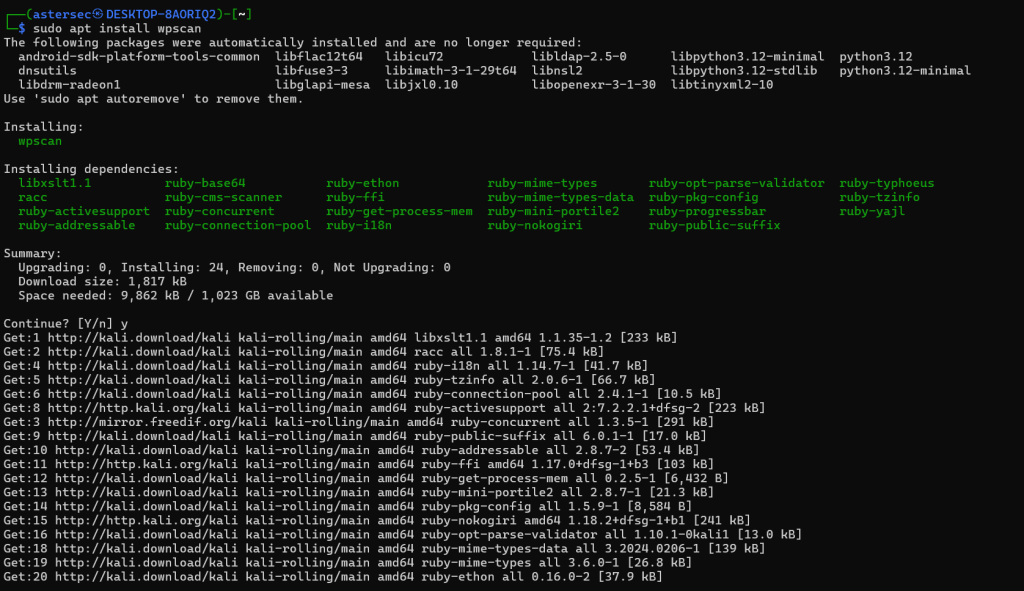
On macOS (using Homebrew)
brew install wpscanUsing Docker
docker pull wpscanteam/wpscan
docker run -it --rm wpscanteam/wpscan --url example.comBasic WPScan Commands
Here are some fundamental commands to get started:
- Basic scan:
wpscan --url https://yourwebsite.com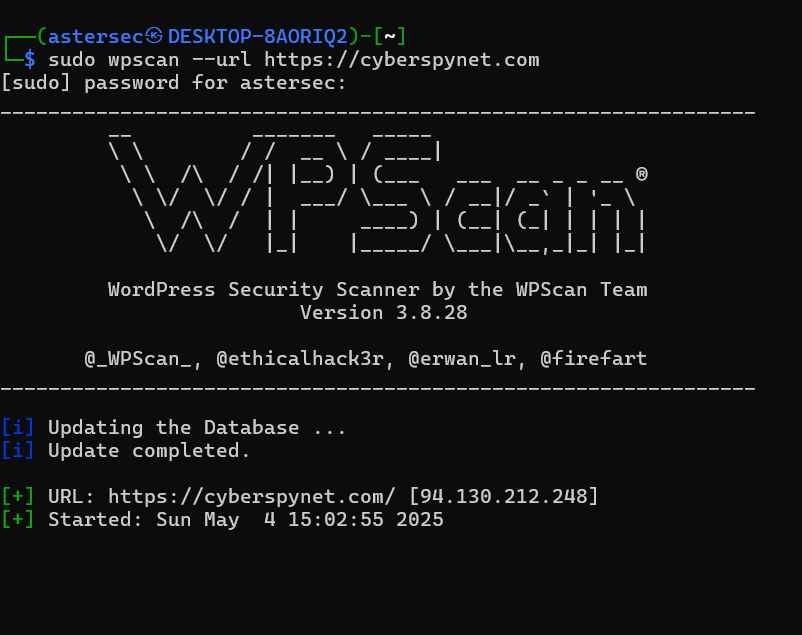
- Enumerate plugins:
wpscan --url https://yourwebsite.com --enumerate p- Enumerate themes:
wpscan --url https://yourwebsite.com --enumerate t- Password brute force attack:
wpscan --url https://yourwebsite.com --passwords /path/to/wordlist.txt --usernames adminEthical Considerations
When using WPScan, it’s crucial to remember:
- Always get permission – Never scan websites you don’t own or have explicit permission to test
- Use responsibly – These tools can cause denial of service if used aggressively
- Follow laws and regulations – Unauthorized scanning is illegal in many jurisdictions
- Disclose responsibly – If you find vulnerabilities, report them properly to the site owner
Protecting Your WordPress Site from WPScan
Since WPScan reveals vulnerabilities, here’s how to protect your site:
- Keep WordPress core updated
- Update all plugins and themes regularly
- Use strong passwords and limit login attempts
- Implement a Web Application Firewall (WAF)
- Disable XML-RPC if not needed
- Limit user enumeration by adding code to functions.php
- Change the default admin username from “admin”
Advanced WPScan Techniques
For more thorough testing:
- API token usage (get one from WPScan.com):
wpscan --url https://yourwebsite.com --api-token YOUR_TOKEN- Aggressive plugin detection:
wpscan --url https://yourwebsite.com --enumerate ap- TimThumb vulnerability detection:
wpscan --url https://yourwebsite.com --enumerate ttConclusion
WPScan is an essential tool for WordPress security professionals when used ethically. Regular scanning helps maintain strong security postures and prevents successful attacks. Remember that with great power comes great responsibility – always use these tools within legal and ethical boundaries.