If you’re diving into the world of web security, you’ve likely come across the term “Cross-Site Scripting,” or XSS. It’s one of the most common and dangerous vulnerabilities in web applications today. XSS allows attackers to inject malicious scripts into websites, potentially compromising user data, hijacking sessions, and wreaking havoc on web apps.
In this post, we’ll take a deeper look into XSS, how it works, and how to protect your applications from such attacks. We’ll even use a vulnerable PHP-based website (shown in the screenshot as an example to help understand how XSS works in action.
What is Cross-Site Scripting (XSS)?
Cross-Site Scripting, or XSS, is a security vulnerability that allows an attacker to inject malicious scripts into web pages. These scripts can execute in the context of a victim’s browser, leading to a wide range of issues, such as:
- Stealing sensitive data (like login credentials or session cookies)
- Hijacking user sessions
- Redirecting users to malicious websites
- Modifying website content
In short, XSS allows attackers to interact with your users, hijacking their experience and potentially exposing their personal data.
Types of XSS Attacks
- Stored XSS: The malicious script is permanently stored on the server (such as in a database) and gets executed when the affected page is viewed by other users.
- Reflected XSS: The script is immediately reflected off the server and executed in the user’s browser as a result of a malicious request.
- DOM-Based XSS: The script runs in the browser itself and manipulates the DOM (Document Object Model) in an unsafe way, causing malicious execution.
Analyzing the Vulnerable PHP Web Application
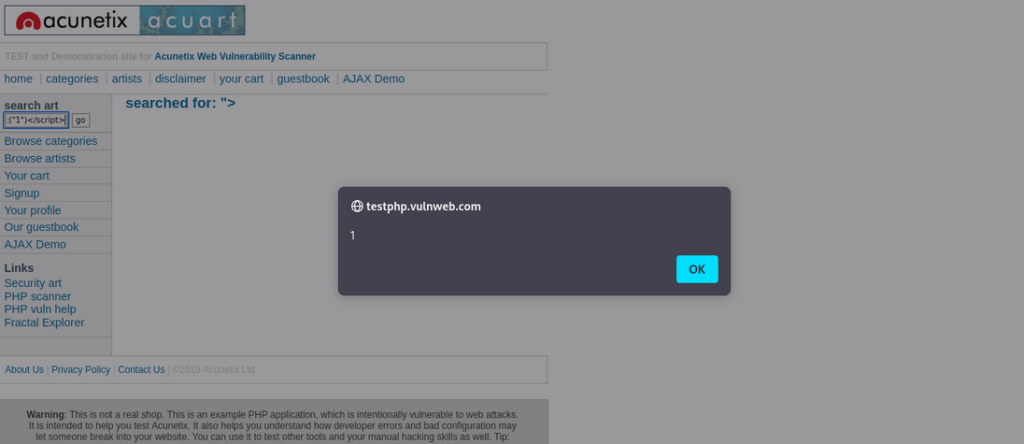
Now, let’s take a look at the screenshot you provided. It shows a vulnerable PHP-based web application where an input field (used to search for art) is not properly sanitized. This is a classic example of how XSS can sneak in.
How Does It Work?
In the screenshot, the “Search art” input field allows the user to type in a query. However, it doesn’t sanitize the input properly before displaying it back to the user. So, when you enter a malicious payload (like <script>alert('XSS')</script>), the server reflects this input back to the user’s browser as part of the search results. As a result, the browser executes the script, triggering an alert box with the message “XSS.”
This is an example of reflected XSS. The attacker’s script gets reflected immediately when the victim interacts with the vulnerable input field.
How to Exploit XSS (In Simple Terms)
Here’s how an attacker could exploit this vulnerability:
- Step 1: Find a vulnerable input field—like the one shown in the search box.
- Step 2: Inject malicious JavaScript into the input. For example:
<script>alert('XSS')</script>. - Step 3: Submit the form or search query, causing the injected script to be reflected back and executed in the victim’s browser.
When executed, this malicious JavaScript could do much worse than just show an alert. It could steal the user’s session cookies, redirect the victim to a phishing site, or even submit data to the attacker’s server.
Tools for Testing XSS Vulnerabilities
If you’re a web developer or security researcher, you’ll want to use tools to test for XSS vulnerabilities in your application. Here are a few that can help:
- Burp Suite: A popular tool for scanning and exploiting web vulnerabilities, including XSS. It helps you automate the detection of such issues.
- OWASP ZAP: Another great tool for security testing, helping you identify XSS and other common vulnerabilities.
- XSSer: A specialized tool designed to test for and exploit XSS vulnerabilities in web apps.
- Acunetix: As seen in the screenshot, Acunetix is a web vulnerability scanner that automatically detects XSS and other security flaws.
How to Prevent XSS Vulnerabilities
Now that you understand how XSS works and how it can be exploited, it’s time to talk about how to prevent it. Here are the best practices to safeguard your web applications from XSS attacks:
- Validate and Sanitize User Inputs: Always validate and sanitize any input from users, including form data, query strings, and HTTP headers. Use functions like
htmlspecialchars()in PHP to escape characters that could be interpreted as HTML or JavaScript. - Use a Content Security Policy (CSP): Implement a CSP header to restrict the types of content that can execute on your website. For example, you can disallow inline scripts, which is one of the main vectors for XSS.
- Escape Data Before Displaying It: Always escape dynamic content before displaying it back to the user. This prevents any injected JavaScript from being executed.
- HttpOnly Cookies: Set your cookies with the
HttpOnlyflag, ensuring they can’t be accessed through JavaScript. This helps mitigate the impact of XSS attacks like session hijacking. - Regular Security Audits: Regularly conduct security audits and penetration testing to identify and fix XSS and other vulnerabilities in your web application.
- Educate Your Development Team: Make sure your development team is aware of XSS and other web security issues. Regular training and code reviews are crucial in preventing vulnerabilities.










