In this comprehensive guide, we’ll dive deep into the various types of hackers, breaking them down based on their intentions, methods, and impact.
The world of cybersecurity is vast, and its defenders and offenders are often portrayed as mysterious figures behind screens. However, hacking is not a one-size-fits-all activity, and there are distinct types of hackers, each with their own skills, motivations, and methods. From ethical hackers to malicious attackers, the hacking community is full of varied and often conflicting roles. Understanding these roles is critical in appreciating how cybersecurity works, what threats exist, and how to protect yourself from them.
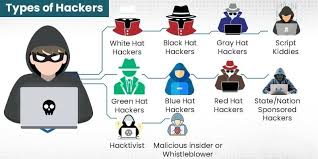
1. White Hat Hackers (Ethical Hackers)
Who They Are: White hat hackers are the “good guys” in the world of hacking. They are skilled professionals who use their knowledge and expertise to identify security vulnerabilities and fix them before malicious hackers can exploit them.
Primary Role: Their job is to test and evaluate systems, networks, and software for vulnerabilities. White hat hackers often work as part of security teams in organizations or as independent consultants in the field of penetration testing (pentesting).
Motivation: Their goal is to improve security by identifying weaknesses and helping to patch them. They work with companies and organizations to find vulnerabilities that could be exploited and report them, often in exchange for a fee or compensation (bug bounties).
Legal Standing: White hat hackers have permission to access the systems they test, making their actions legal.
2. Black Hat Hackers (Malicious Hackers)
Who They Are: Black hat hackers are the “bad guys” in the hacking world. They use their skills to exploit systems for personal gain, whether financial or otherwise. These hackers break into systems illegally, often for malicious purposes.
Primary Role: Their activities include stealing data, spreading malware, conducting denial-of-service (DoS) attacks, and exploiting vulnerabilities in systems for financial gain, espionage, or destruction.
Motivation: Black hat hackers are typically driven by personal gain, whether it’s financial (stealing credit card numbers, conducting ransomware attacks), political (hacktivism), or just for the thrill of causing chaos.
Legal Standing: Their actions are illegal, and they operate outside the law. They face criminal charges if caught and prosecuted.
3. Grey Hat Hackers
Who They Are: Grey hat hackers fall somewhere in between white and black hat hackers. They may break into a system without authorization, but unlike black hats, they typically do not have malicious intent. Instead, they may report the vulnerability they find to the system owner, sometimes for a reward.
Primary Role: Grey hat hackers may exploit security vulnerabilities but do so to bring attention to them. They might not cause harm but often act without permission, which puts them in a gray area legally.
Motivation: While they may not seek personal gain, they might engage in hacking activities to demonstrate their skills or to get recognized for finding security flaws. Some grey hats may want to get hired as ethical hackers.
Legal Standing: While grey hat hackers don’t intend harm, their actions are often still illegal because they don’t have authorization to access systems. This makes their position legally ambiguous.
4. Red Hat Hackers
Who They Are: Red hat hackers are the vigilantes of the hacking world. While similar to white hat hackers, red hats take a more aggressive approach in their tactics. Their goal is to stop black hat hackers, often through offensive actions.
Primary Role: These hackers work to track down and eliminate black hat hackers by targeting their systems and infrastructures. Red hat hackers typically go after black hat hackers without waiting for legal authorities to intervene.
Motivation: Their main aim is to stop criminal hackers by taking matters into their own hands. While their intention may be to protect systems, their tactics often involve extreme actions that may cross ethical or legal lines.
Legal Standing: Like black hats, red hat hackers may break laws when attempting to stop black hat hackers, making their methods controversial.
5. Blue Hat Hackers
Who They Are: Blue hat hackers are individuals who use their hacking skills to test and ensure that the security measures of a system or organization are strong. They are typically hired by companies to perform last-minute vulnerability testing before a system’s launch.
Primary Role: Their primary job is to conduct security testing and vulnerability assessments to prevent potential attacks. Blue hats are often contracted by companies as a part of their quality assurance or security testing process.
Motivation: They want to help organizations ensure their systems are secure before going live. They typically work to find weaknesses and fix them before they are exploited.
Legal Standing: Blue hat hackers usually work within legal boundaries and are hired for their expertise. Their activities are authorized by the organization they are contracted to.
6. Hacktivists (Political Hackers)
Who They Are: Hacktivists are individuals or groups of hackers who use their skills for political or social causes. Their hacking activities are often targeted at government organizations, corporations, or institutions they believe are acting unjustly.
Primary Role: Hacktivists engage in cyberattacks like defacing websites, stealing sensitive information, or launching DoS attacks. Their goal is to draw attention to a political issue or to take down what they perceive as corrupt organizations.
Motivation: Hacktivists are motivated by political or ideological reasons, using hacking as a form of protest or activism. Their attacks are often meant to make a statement rather than for personal gain.
Legal Standing: Despite their ideological motivations, hacktivism is still illegal. Hacktivists often face criminal charges if caught.
7. Script Kiddies
Who They Are: Script kiddies are individuals who lack the advanced skills of a true hacker but still engage in cyberattacks by using pre-written hacking tools and scripts. They often rely on hacking software created by others and may not fully understand the complexities of what they are doing.
Primary Role: Script kiddies engage in relatively low-level hacking activities, such as launching basic DoS attacks, exploiting simple vulnerabilities, or defacing websites. They typically target easy-to-hack systems and may cause disruptions, but they don’t have the knowledge or skill to perform sophisticated attacks.
Motivation: They are often motivated by the thrill of hacking, the desire to impress others, or to gain a sense of belonging in the hacker community. They may also engage in hacking for attention or peer recognition.
Legal Standing: While their methods are less sophisticated, script kiddies are still engaging in illegal activity and can face criminal charges if caught.
8. State-Sponsored Hackers (Nation-State Hackers)
Who They Are: State-sponsored hackers are highly skilled individuals or groups who are employed or funded by a government to carry out cyberattacks for political or military purposes. These hackers are often part of national intelligence agencies or military units.
Primary Role: State-sponsored hackers conduct espionage, cyber warfare, sabotage, and influence operations. They may target other governments, businesses, or individuals to steal sensitive information, disrupt operations, or manipulate public opinion.
Motivation: Their primary motivation is often geopolitical. They may seek to gain intelligence, weaken adversaries, or disrupt critical infrastructure to benefit their nation’s interests.
Legal Standing: While their actions are legal within their own countries, state-sponsored hackers often operate outside international laws, leading to global tensions and conflicts.