In an age where communication is increasingly digital, SMS (Short Message Service) remains one of the most widely used methods for sending text messages. However, this convenient tool has also become a target for malicious actors, especially in the form of SMS spoofing. This form of cyberattack can be used for fraud, phishing, and social engineering, putting both individuals and businesses at risk.
In this blog post, we’ll explore what SMS spoofing is, how it works, its potential dangers, and most importantly, how you can protect yourself from falling victim to this type of attack.
What is SMS Spoofing?
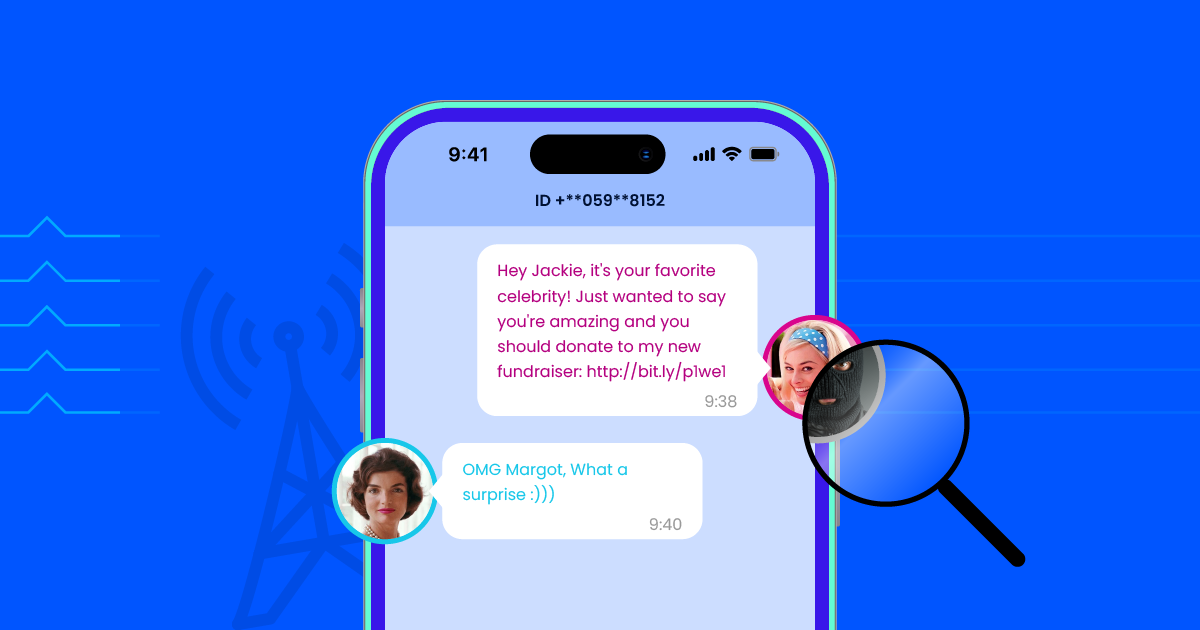
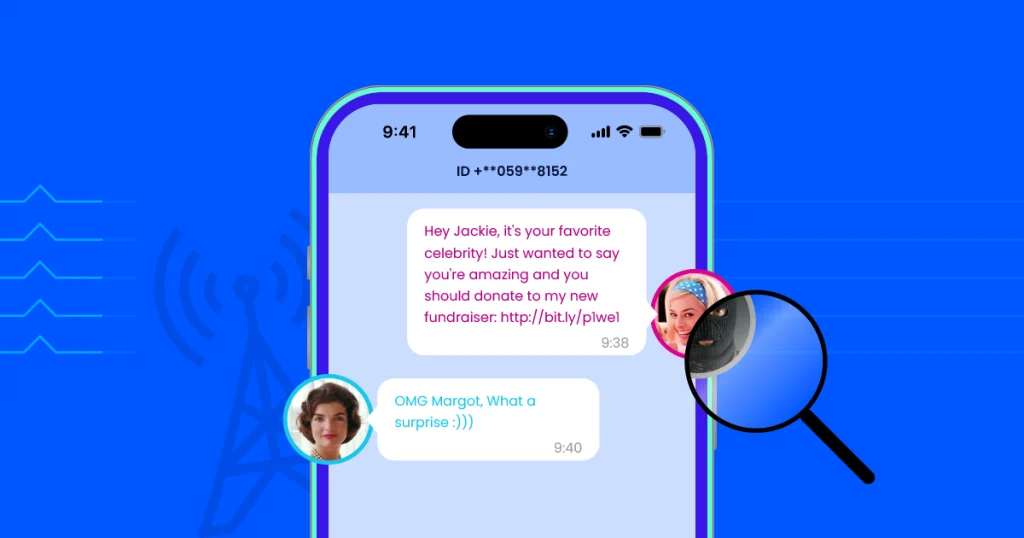
SMS spoofing refers to the practice of falsifying the sender’s information on a text message to make it appear as though it is coming from a trusted source when, in reality, it is not. In other words, the attacker “spoofs” the phone number or sender ID of the SMS, making it seem legitimate.
For example, a hacker might send an SMS that appears to come from your bank, a government agency, or a trusted business. This message may contain malicious links, fake alerts, or requests for sensitive information. The goal is typically to trick the recipient into performing a specific action, such as clicking on a malicious link, sharing personal details, or downloading malware.
How Does SMS Spoofing Work?
SMS spoofing is relatively easy to execute for a cybercriminal, and it doesn’t require advanced technical skills. Here’s a simplified overview of how the attack works:
- Sender ID Manipulation: The attacker uses a spoofing tool or software to change the sender’s number to a number that looks legitimate. This could be a phone number of a trusted organization (like your bank), a well-known company, or even a government agency.
- Message Delivery: The malicious message is sent out to the targeted victim(s) with the spoofed number as the sender.
- Tricking the Victim: Since the victim believes the message is from a legitimate source, they are more likely to click on any links or respond to the message with personal information, login credentials, or other sensitive data.
- Execution of Attack: The attacker can then use the victim’s information to steal money, access accounts, or infect the victim’s device with malware.
Common Uses of SMS Spoofing
SMS spoofing is often used in a variety of malicious activities, including:
- Phishing Attacks: A hacker may impersonate a bank, social media platform, or service provider and ask the victim to click on a link or provide personal information. For example, a fake bank alert might warn the victim that their account is compromised and prompt them to enter login details on a fraudulent website.
- Smishing: This is a form of phishing conducted through SMS, where an attacker sends fake messages that contain links to fraudulent websites designed to steal personal information. Smishing attacks can also involve attachments that contain malware.
- Fraudulent Activity: Attackers can use SMS spoofing to impersonate friends, family members, or even employees, and trick the victim into transferring money or providing access to sensitive data.
- Social Engineering: Hackers can manipulate victims into performing actions they normally wouldn’t, such as divulging sensitive information, by pretending to be someone they trust.
How to Protect Yourself from SMS Spoofing
While it can be difficult to prevent SMS spoofing entirely, there are several measures you can take to protect yourself from falling victim to these attacks.
1. Be Cautious with Unknown Numbers
If you receive an SMS from an unknown number or a number that seems suspicious, exercise caution before responding. Legitimate organizations generally do not send unsolicited messages, especially those requesting personal information.
2. Don’t Click on Suspicious Links
If you receive a text that includes a link or attachment, avoid clicking on it unless you are absolutely sure the message is legitimate. Even if the message seems to be from a trusted source, it’s always safer to visit the official website directly or contact the organization using a verified phone number.
3. Use Two-Factor Authentication (2FA)
For extra security, enable two-factor authentication (2FA) wherever possible. Even if a hacker manages to obtain your login credentials through an SMS phishing attack, 2FA provides an added layer of protection by requiring an additional form of identification, such as a code sent to your phone.
4. Verify the Sender
If you receive an unexpected message claiming to be from a bank, government agency, or other trusted entity, always verify the sender’s identity. Contact the organization directly through their official phone number or website to confirm whether the message is legitimate.
5. Install Security Software
Use reliable security software on your phone to detect and block potential threats, including smishing and other types of malware delivered via SMS.
6. Report Suspicious SMS Messages
If you receive a suspicious text message, report it to your mobile carrier. Many carriers have dedicated services to help block fraudulent or spoofed messages. Additionally, you can report smishing attempts to authorities or cybersecurity organizations in your area.
7. Avoid Sharing Personal Information via SMS
Never share sensitive information like passwords, credit card details, or social security numbers via SMS. Legitimate organizations will not ask for this information via text.
All of the information in this blog is just of educational purposes