In today’s interconnected world, mobile phones have become essential tools for communication, banking, socializing, and even securing access to sensitive accounts. However, as technology advances, so do the risks associated with it. One such threat is SIM cloning, a malicious technique that can lead to identity theft, unauthorized access to accounts, and severe privacy breaches. In this blog, we will explore what SIM cloning is, how it works, its potential risks, and most importantly, how to protect yourself from this growing threat.
What is SIM Cloning?
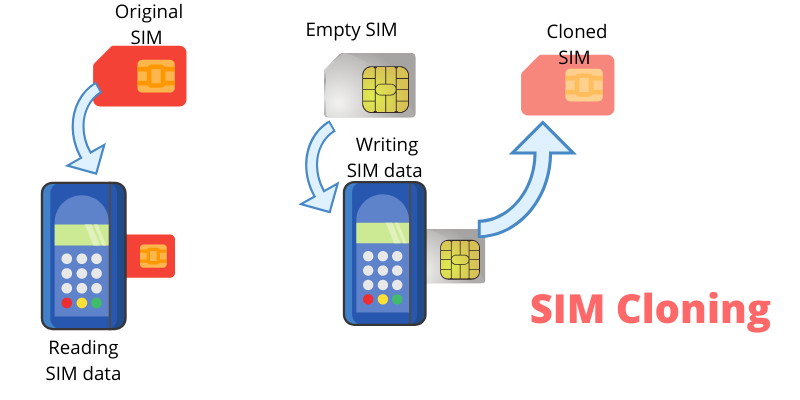
SIM cloning is the process of copying the unique information stored on a SIM (Subscriber Identity Module) card and transferring it to another card. Each SIM card contains a unique International Mobile Subscriber Identity (IMSI) number and a secret key used for encryption and authentication purposes. By cloning this information, an attacker can impersonate a victim’s phone, make calls, send messages, or access sensitive accounts associated with the number.
SIM cloning typically involves stealing a victim’s SIM card data through various means, such as phishing attacks, SIM swap attacks, or physical access to the SIM card. Once cloned, the attacker can use the stolen identity to carry out fraudulent activities, including accessing banking applications, social media accounts, and two-factor authentication codes.
How SIM Cloning Works
- Stealing SIM Data: The attacker typically gathers the IMSI number and authentication key from the victim’s SIM card. This may be achieved through physical theft, hacking, or exploiting vulnerabilities in the GSM network.
- Creating a Clone SIM: The attacker copies the victim’s SIM data onto a new, blank SIM card. This new card behaves like the original SIM, enabling the attacker to access services and make calls as if they were the victim.
- Exploiting the Cloned SIM: With the cloned SIM card in their possession, the attacker can make unauthorized calls, send messages, and even hijack banking services or social media accounts by bypassing security mechanisms like SMS-based 2FA (Two-Factor Authentication).
Common Methods of SIM Cloning
- SIM Swap Attacks: A SIM swap attack is one of the most common ways a SIM can be cloned. In this attack, the attacker convinces the victim’s telecom provider to switch the victim’s number to a new SIM card. Once the attacker has control of the number, they can gain access to sensitive services and bypass security features like 2FA.
- Phishing: Attackers may use phishing emails or fake websites to trick victims into revealing their personal details, including SIM card information. Once the attacker has enough information, they can clone the SIM card and impersonate the victim.
- SIM Card Cloning Software: Some hackers use SIM cloning software to copy the data from one SIM card to another. This is usually done through a card reader and specialized software.
Risks of SIM Cloning
SIM cloning poses serious risks to individuals and organizations, including:
- Identity Theft: With the ability to intercept calls and messages, attackers can steal personal information and gain access to sensitive data such as banking details, passwords, and private communications.
- Financial Fraud: By impersonating the victim, attackers can initiate fraudulent transactions, transfer money, or even make online purchases.
- Unauthorized Access: SIM cloning can bypass security features like SMS-based 2FA, allowing attackers to access critical services such as online banking, email accounts, and social media profiles.
- Loss of Privacy: Since the attacker can impersonate the victim’s phone, it compromises the victim’s privacy and exposes them to potential blackmail, harassment, and scams.
Mitigating the Risk of SIM Cloning
While SIM cloning is a serious threat, there are several steps you can take to mitigate the risk and protect your personal information.
1. Use Strong Authentication Methods
Instead of relying solely on SMS-based two-factor authentication (2FA), use more secure alternatives such as:
- Authenticator Apps: Google Authenticator, Authy, or Microsoft Authenticator provide time-based codes that are more secure than SMS.
- Hardware Tokens: Physical hardware tokens, such as YubiKey, are extremely difficult to clone and provide an additional layer of security.
2. Avoid Sharing Personal Information
Be cautious when sharing your personal information. Avoid responding to unsolicited emails, text messages, or phone calls that ask for sensitive data. Scammers often use phishing tactics to steal your information and clone your SIM.
3. Set Up a PIN or Password with Your Mobile Carrier
Most telecom providers offer an additional layer of security, such as a PIN or password, to prevent unauthorized SIM swaps. Ensure you enable this feature to make it more difficult for attackers to initiate a SIM swap.
4. Monitor Your Account for Suspicious Activity
Regularly monitor your phone and mobile carrier account for any suspicious activity. If you notice a sudden loss of service or strange messages, it could be a sign that your SIM has been cloned or swapped.
5. Contact Your Carrier Immediately
If you suspect your SIM has been cloned or swapped, contact your mobile carrier immediately. Request a new SIM card, change your PIN or password, and ask them to investigate any fraudulent activity on your account.
6. Use Encryption and Secure Communication Apps
For highly sensitive communications, use end-to-end encrypted messaging apps like Signal or WhatsApp, which provide more security than traditional SMS. These apps ensure that even if someone clones your SIM, they cannot intercept your encrypted messages.
7. Stay Informed About Security Threats
Keep yourself informed about the latest security threats, including SIM cloning techniques and scams. By staying aware, you can better protect yourself against evolving threats.
Conclusion
SIM cloning is a dangerous and growing threat that can compromise your privacy, security, and financial safety. However, by taking proactive steps to protect yourself, such as using stronger authentication methods, being cautious with personal information, and working with your telecom provider, you can reduce the risk of falling victim to this attack.
While SIM cloning can be difficult to prevent entirely, staying informed, using secure communication methods, and acting quickly in the event of suspicious activity can go a long way in safeguarding your mobile identity and personal data.
This Blog is just for educational purposes ; hope you guys like the article









