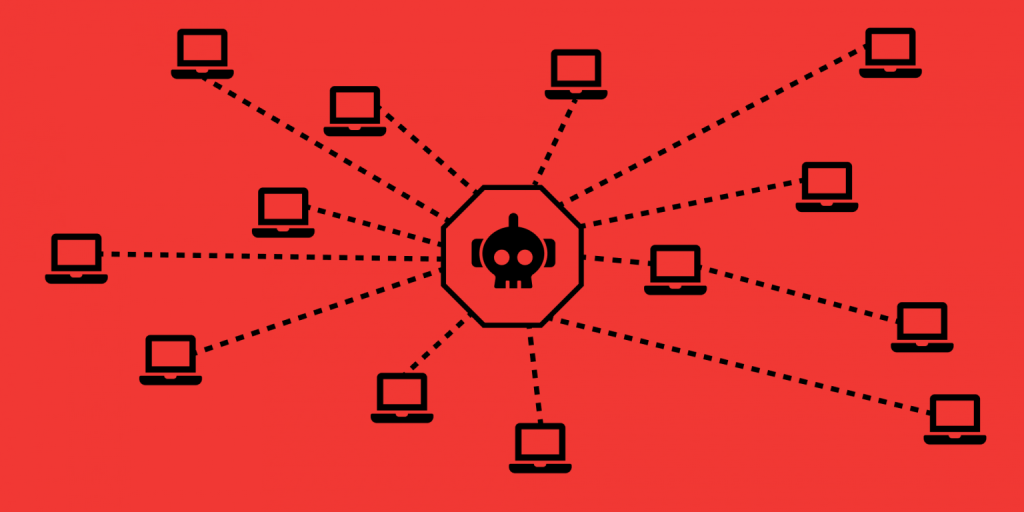
Cyberattacks have evolved over the years, and one of the most impactful types of attack is Denial of Service (DoS) and Distributed Denial of Service (DDoS). These attacks are designed to disrupt the normal functioning of networks, systems, and services, causing significant downtime and potential financial losses. These types of attacks are often powered by botnets—networks of compromised devices that can be remotely controlled by cybercriminals. In this comprehensive guide, we’ll delve into the mechanisms of DoS/DDoS attacks, explore current active botnets (both free and paid), and discuss how Virtual Private Servers (VPS) can be used for bulletproof security to mitigate these attacks.
What is a DoS (Denial of Service) Attack?
A Denial of Service (DoS) attack occurs when a single machine is used to flood a target system with traffic or malicious requests, causing it to become slow or unresponsive. The goal is to overwhelm the system’s resources—such as CPU, memory, bandwidth, or network connections—so it can no longer process legitimate requests from users.
- How It Works: The attacker sends an overwhelming volume of traffic to the target system or a specific service, exhausting its resources and leading to service degradation or failure.
- Types of DoS Attacks:
- Flooding Attacks: These attacks involve sending large volumes of traffic to the target, such as UDP floods, SYN floods, and ICMP floods.
- Amplification Attacks: Attackers exploit publicly accessible servers to amplify the attack, making it more difficult to trace. Common examples include DNS amplification and NTP amplification.
- Application Layer Attacks: These attacks focus on exhausting the target’s resources by exploiting application-level vulnerabilities, often leading to HTTP floods and Slowloris attacks.
Common DoS Attack Tools:
- LOIC (Low Orbit Ion Cannon): A popular tool used for launching DoS attacks, capable of sending HTTP, UDP, or TCP flood attacks.
- HOIC (High Orbit Ion Cannon): An upgraded version of LOIC, capable of launching HTTP floods.
- Slowloris: A tool designed to keep many connections to the target web server open and hold them open as long as possible, consuming resources.
What is a DDoS (Distributed Denial of Service) Attack?
A Distributed Denial of Service (DDoS) attack is a more sophisticated version of the DoS attack. Instead of one machine, multiple systems (often thousands or millions) are used to flood a target system or network with massive amounts of traffic, overwhelming it and causing service disruptions.
- How It Works: In DDoS attacks, cybercriminals leverage botnets—a network of compromised devices (often IoT devices)—to distribute the attack’s traffic across many machines. This decentralizes the attack and makes it much harder to block.
- DDoS Attack Categories:
- Volumetric Attacks: These attacks aim to consume the bandwidth of the target with high volumes of traffic. Examples include UDP floods, DNS floods, and ICMP floods.
- Protocol Attacks: These attacks focus on exploiting a protocol vulnerability, such as SYN floods, Smurf attacks, or ACK floods, which consume server or network device resources.
- Application Layer Attacks: These attacks are focused on the application layer, often targeting specific web applications and consuming server resources, e.g., HTTP floods or Slowloris attacks.
DDoS Attack Tools:
- Mirai Botnet: One of the most notorious DDoS tools, targeting IoT devices to launch massive attacks.
- XerXes: A tool that targets web servers and causes DDoS attacks via HTTP requests.
- LOIC: Though initially a DoS tool, LOIC is commonly used in DDoS attacks, especially when launched from a botnet.
What are Botnets?
A botnet is a network of computers and devices infected with malware that allows cybercriminals to control them remotely. These compromised devices, also called zombies, can be used to launch DDoS attacks, spread spam, steal data, and perform other malicious activities. Botnets are the primary tools used to execute large-scale DDoS attacks.
- How Botnets Are Created: Attackers use malware to infect devices, and once a device is infected, it becomes part of the botnet. The botnet operator (often referred to as the botmaster) can send commands to these infected devices from a central Command and Control (C&C) server or through a decentralized peer-to-peer network.
- Types of Botnets:
- Centralized Botnets: These botnets rely on a single C&C server to issue commands to the infected devices.
- Peer-to-Peer (P2P) Botnets: These botnets distribute commands and communications across infected machines without relying on a single C&C server, making them harder to trace and disrupt.
Botnet Examples:
- Mirai Botnet: One of the most famous botnets, created by exploiting default credentials in IoT devices like security cameras and routers.
- Emotet: A malware family that initially served as a banking Trojan, but evolved into a botnet used for large-scale spam and phishing campaigns.
- Sora Botnet: A botnet primarily focused on attacking IoT devices and utilizing them for DDoS attacks.
Active Botnets (Paid vs Free)
Paid Botnets
Paid botnets are often offered as DDoS-as-a-Service, where cybercriminals can rent a botnet to carry out attacks. These services are usually more advanced and provide reliable support and customizable attacks.
- Satori Botnet: An advanced DDoS botnet that targets IoT devices, particularly routers. It can launch multiple types of DDoS attacks, including SYN floods and DNS amplification.
- Koto Botnet: A paid botnet that provides DDoS services and is capable of executing sophisticated attacks like HTTP Floods, DNS Floods, and more.
Free Botnets
Free botnets are typically less powerful and more likely to be unstable. However, they are widely available on underground forums or dark web marketplaces and are sometimes used for smaller, targeted attacks.
- Mirai Botnet: Originally free and open-source, it has evolved into a widely used botnet for DDoS attacks, often targeting IoT devices with weak security.
- Reaper Botnet: Once available for free, this botnet was designed to exploit vulnerabilities in IoT devices, spreading itself rapidly across networks.
Using VPS for Bulletproof Security
A Virtual Private Server (VPS) can serve as an effective measure for bulletproof security when used correctly. VPS solutions provide users with isolated environments, offering flexibility and control over the server while simultaneously protecting against DDoS attacks and botnets.
How VPS Helps in Mitigating Attacks:
- Isolation of Resources: A VPS ensures that resources are isolated from other users, making it harder for a botnet to exploit weaknesses in a shared hosting environment.
- DDoS Protection: Many VPS providers offer built-in DDoS protection and firewall rules that can filter malicious traffic and prevent attacks from reaching your server.
- Geographical Distribution: Providers such as OVH or Vultr have multiple data center locations across the globe, allowing you to distribute your services across different regions. This can help mitigate the risk of a DDoS attack targeting a single location.
VPS Providers for Bulletproof Security
| VPS Provider | Key Features | DDoS Protection |
|---|---|---|
| OVH | Known for high-performance servers and a wide selection of VPS options. | Advanced DDoS mitigation tools, customizable plans. |
| Vultr | Provides flexible VPS plans with locations worldwide. | Built-in DDoS protection with Cloud Firewalls. |
| Sharktech | Specializes in offering high-performance VPS with advanced DDoS mitigation. | Dedicated DDoS protection and free mitigation. |
| HostHorde | Offers fast and secure VPS hosting. | Free DDoS protection included. |
| DigitalOcean | Known for simplicity and scalability, great for developers. | DDoS mitigation available through firewalls. |
Mitigating DDoS and Botnet Attacks
Mitigation Techniques for DDoS Attacks:
- Rate Limiting: Limit the number of requests a server can handle per unit of time.
- Traffic Filtering: Using tools like Cloudflare to filter malicious traffic before it reaches the server.
- Geographical Restrictions: Block traffic coming from regions or countries that do not serve your user base.
Mitigating Botnets:
- IoT Device Security: Ensure IoT devices are updated regularly and have strong passwords to prevent them from being infected by botnets.
- Botnet Detection Tools: Utilize tools like Honeyd or NetFlow Analyzer to detect botnet activity on your network.
- Botnet Blacklisting: Use firewall rules to block known IP addresses associated with botnet traffic.
All informations in this blog is just for educational purposes we are not responsible for your actions .








Unquestionably believe that that you stated. Your favorite reason appeared to
be on the net the simplest factor to remember of. I say to
you, I certainly get annoyed while other people consider worries
that they just don’t recognise about. You controlled to hit the nail upon the top and outlined
out the entire thing without having side-effects , folks can take a signal.
Will probably be again to get more. Thanks