In the world of penetration testing and cybersecurity, enumeration and discovery of hidden resources on web servers are crucial steps. One of the most popular tools for this task is Gobuster, a fast and efficient tool used to perform directory brute-forcing and DNS subdomain enumeration. This article will dive into Gobuster’s features, usage, and technical aspects, providing cybersecurity professionals with an in-depth understanding of this powerful tool.
What is Gobuster?
Gobuster is an open-source tool designed for web application security assessments. It helps penetration testers and security researchers discover hidden directories and subdomains on a target web server by using wordlist-based brute-forcing. Written in Go (Golang), Gobuster is known for its speed, efficiency, and ease of use, making it a popular choice for security professionals.
Gobuster can be used for two main purposes:
- Directory/Files Brute-forcing: Discover hidden files or directories on web servers.
- DNS Subdomain Brute-forcing: Enumerate subdomains under a specified domain.
Both of these capabilities are essential for uncovering vulnerabilities, misconfigurations, or additional attack vectors that might be overlooked.
Installation of Gobuster
Installing Gobuster is relatively simple and can be done in various environments. Here’s how to install it on common systems.
Installing on Linux (Debian/Ubuntu)
sudo apt update ;
sudo apt install golang-go ;
go install github.com/OJ/gobuster/v3@latest
Ensure that the Go binary path is added to the PATH environment variable:
export PATH=$PATH:$(go env GOPATH)/binInstalling on Windows
On Windows, you can either use Windows Subsystem for Linux (WSL) or Go for native installation:
- Install Golang from the official Go website.
- Use the following command to install Gobuster:
sudo apt install golang-go ;
go install github.com/OJ/gobuster/v3@latest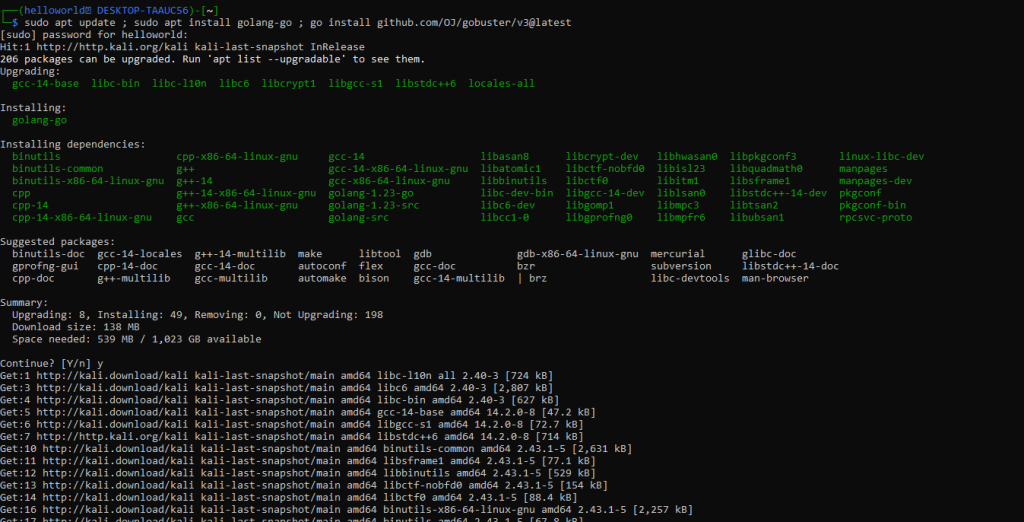
Gobuster Usage
Gobuster supports both directory brute-forcing and DNS subdomain enumeration. Let’s explore how to use these features.
1. Directory/Files Brute-forcing
This is the most common use case of Gobuster. It involves trying various URL paths (such as /admin, /images, /login) to see if there are hidden resources or endpoints that can be exploited.
Basic Command for Directory Brute-forcing
gobuster dir -u http://127.0.0.1 -w /path/to/wordlist.txtdir: Specifies the mode for directory brute-forcing.-u http://example.com: The target URL.-w /path/to/wordlist.txt: The wordlist file containing potential directory names.
Example:
gobuster dir -u http://127.0.0.1 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt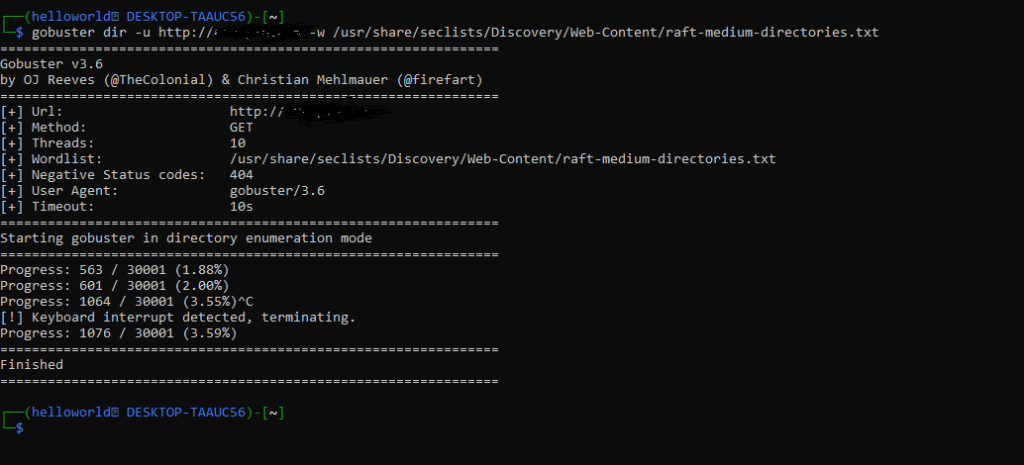
This command will brute-force directories on example.com using a medium wordlist found in Kali Linux’s default directory.
Additional Options for Directory Brute-forcing:
-t 50: Specifies the number of concurrent threads to use. Increasing this value speeds up the attack but can also put more load on the server.-x .php,.html: Specifies file extensions to be appended to each word in the list. This is useful for discovering files with specific extensions like.phpor.html.-s 200: Limits the response status codes to those you are interested in (e.g.,200for a valid page).-l: List the results with details like status codes and content-length.
Example with Multiple Extensions:
gobuster dir -u http://example.com -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .php,.html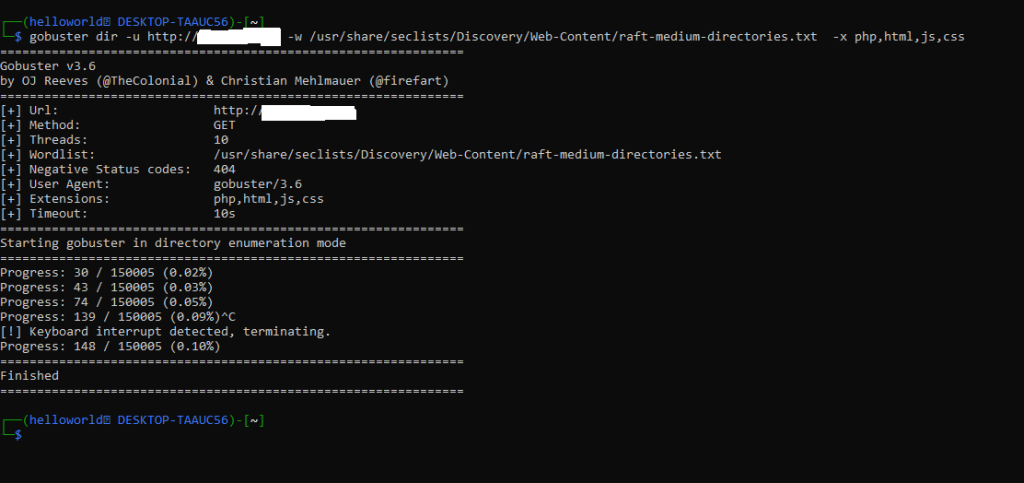
This command will try appending .php and .html to the words in the wordlist.
2. DNS Subdomain Brute-forcing
Gobuster also supports DNS subdomain brute-forcing, which is useful for discovering additional domains or subdomains that are not publicly known.
Basic Command for DNS Subdomain Enumeration
gobuster dns -d localhost -w /path/to/wordlist.txtdns: Specifies the mode for DNS subdomain brute-forcing.-d example.com: The target domain.-w /path/to/wordlist.txt: The wordlist file containing possible subdomain names.
Example:
gobuster dns -d localhost -w /usr/share/wordlists/rockyou.txtThis will brute-force subdomains of example.com using the Rockyou wordlist.
Additional Options for DNS Brute-forcing:
-t 50: Specifies the number of concurrent threads to use.-o output.txt: Save the results to a file.-v: Enable verbose output to see more detailed information about the requests and responses.
Example with Output File:
gobuster dns -d localhost -w /usr/share/wordlists/rockyou.txt -o subdomains.txtThis will save the discovered subdomains to the subdomains.txt file.
Advanced Features and Configurations
1. Proxy Support
Gobuster supports the use of an HTTP/HTTPS proxy for conducting tests in a more anonymous or controlled manner.
gobuster dir -u http://my-domain-that-didnot-exist.com -w /path/to/wordlist.txt -p http://127.0.0.1:8080This will route the traffic through the specified proxy.
2. Custom User-Agent
You can specify a custom user-agent to avoid detection by certain security systems that monitor HTTP requests.
gobuster dir -u http://example.com -w /path/to/wordlist.txt -a "Mozilla/5.0"3. Rate Limiting
In some cases, you may want to control the rate of requests to avoid overwhelming the server or triggering rate-limiting mechanisms. This can be controlled using the -r flag.
gobuster dir -u http://example.com -w /path/to/wordlist.txt -r 5This will limit the rate of requests to 5 per second.
4. Use of Tuning Parameters
Gobuster allows you to fine-tune parameters, like timeouts or retries, to optimize the brute-forcing process.
gobuster dir -u http://example.com -w /path/to/wordlist.txt -t 100 -r 10 -w /path/to/wordlist.txt-t 100: This sets 100 concurrent threads, speeding up the attack.
-r 10: Allows 10 retries for failed requests.
Best Practices for Using Gobuster
- Start Slow: When using Gobuster on a target, begin with fewer threads and a basic wordlist. Monitor the server’s response and adjust the parameters accordingly.
- Use a Good Wordlist: The quality of the wordlist is paramount. Using a larger, more exhaustive wordlist can find more hidden resources, but it will also increase the time and server load. Popular wordlists include SecLists and DirBuster.
- Analyze Response Codes: Pay attention to the HTTP status codes returned by the server. Codes such as
200 OK,301 Moved Permanently, or403 Forbiddenmay indicate valid paths, while404 Not Foundgenerally means the path doesn’t exist. - Be Ethical: Always have permission before running Gobuster against any system. Unauthorized testing can lead to legal consequences.