Google Dorking and Google Hacking Database: A Complete Guide
Google Dorking is a powerful tool that can be used for both…
Understanding Cross-Site Scripting (XSS) and How to Protect Your Web Application
XSS vulnerabilities are one of the most commonly exploited attacks on the…
Complete Guide to Digital Forensics: Tools, Techniques, and Methodologies
Digital forensics is a powerful field that combines technical expertise with legal…
In-Depth Guide to Carding, Cracking, and Mitigation Strategies
Carding and cracking are complex and evolving threats that require comprehensive security…
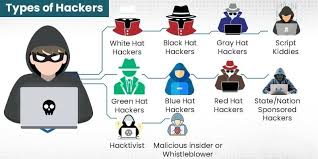
Types of Hackers: A Comprehensive Guide to Understanding the Different Faces of Cybersecurity
The world of hacking is diverse, with hackers coming from different backgrounds…
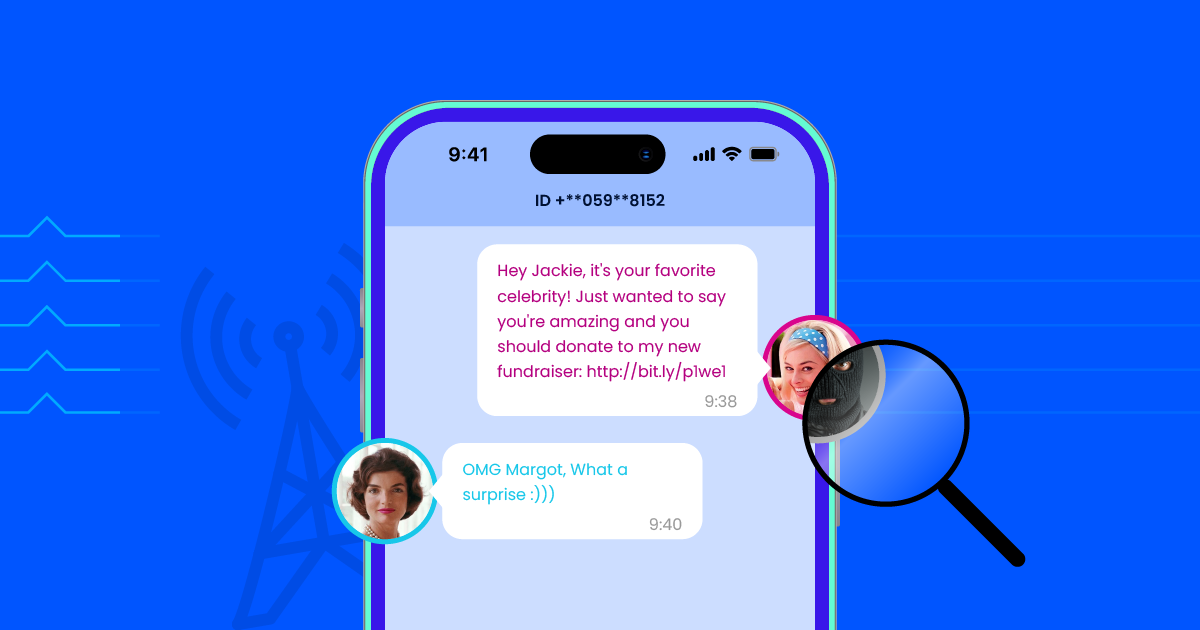
SMS Spoofing: What It Is, How It Works, and How to Protect Yourself
SMS spoofing is a powerful tool for cybercriminals and can be used…
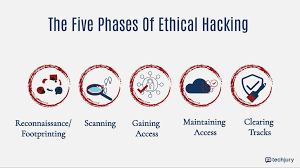
The 5 Stages of Hacking: A Comprehensive Guide to Understanding the Hacking Process
Hacking is a multi-step process, and understanding the stages can help cybersecurity…
How to Maintain Your Privacy and Stay Anonymous Online: A Complete Guide
Privacy is not just about keeping secrets; it's about maintaining control over…
The Surface Web, Deep Web, and Dark Web: A Comprehensive Guide
The Surface Web, Deep Web, and Dark Web form three distinct layers…
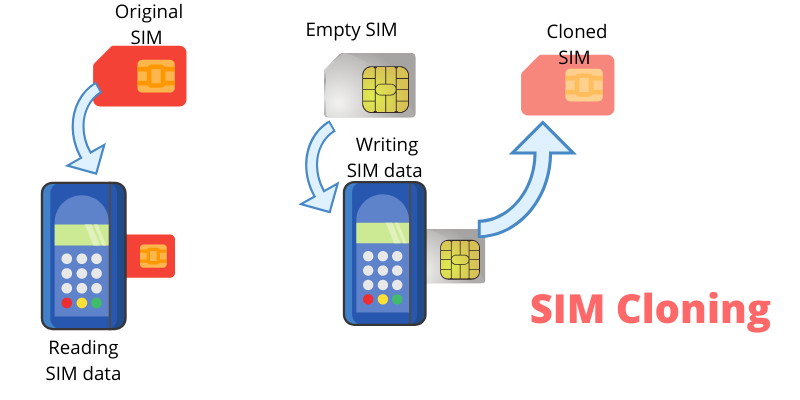
SIM Cloning and Its Mitigations: Understanding the Threat and How to Protect Yourself
SIM cloning is a dangerous and growing threat that can compromise your…