Black Hat Hacking: Understanding the Threat and How to Mitigate It
Black hat hackers pose a significant threat, but understanding their tactics and implementing robust defenses can significantly reduce the risk of compromise. By staying vigilant, using advanced security tools, and…
How to Install and Set Up Burp Suite: A Step-by-Step Guide
Burp Suite is an indispensable tool for web application security testing. By following this guide, you can set up the tool in no time and begin your journey into ethical…
Google Dorking and Google Hacking Database: A Complete Guide
Google Dorking is a powerful tool that can be used for both ethical and malicious purposes. By understanding how Google Dorking works and utilizing the Google Hacking Database, cybersecurity professionals…
Understanding Cross-Site Scripting (XSS) and How to Protect Your Web Application
XSS vulnerabilities are one of the most commonly exploited attacks on the web, but they’re also one of the easiest to prevent with proper security practices. By sanitizing inputs, escaping…
Complete Guide to Digital Forensics: Tools, Techniques, and Methodologies
Digital forensics is a powerful field that combines technical expertise with legal knowledge to uncover the truth behind digital incidents. As cyber threats become increasingly sophisticated, the role of digital…
In-Depth Guide to Carding, Cracking, and Mitigation Strategies
Carding and cracking are complex and evolving threats that require comprehensive security strategies to defend against. Understanding how these attacks work and implementing advanced protections, such as multi-factor authentication, encryption,…
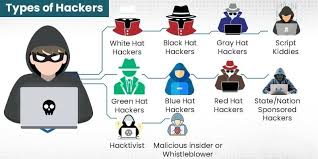
Types of Hackers: A Comprehensive Guide to Understanding the Different Faces of Cybersecurity
The world of hacking is diverse, with hackers coming from different backgrounds and motives. Whether they are working ethically to protect systems or maliciously exploiting vulnerabilities for personal gain, each…
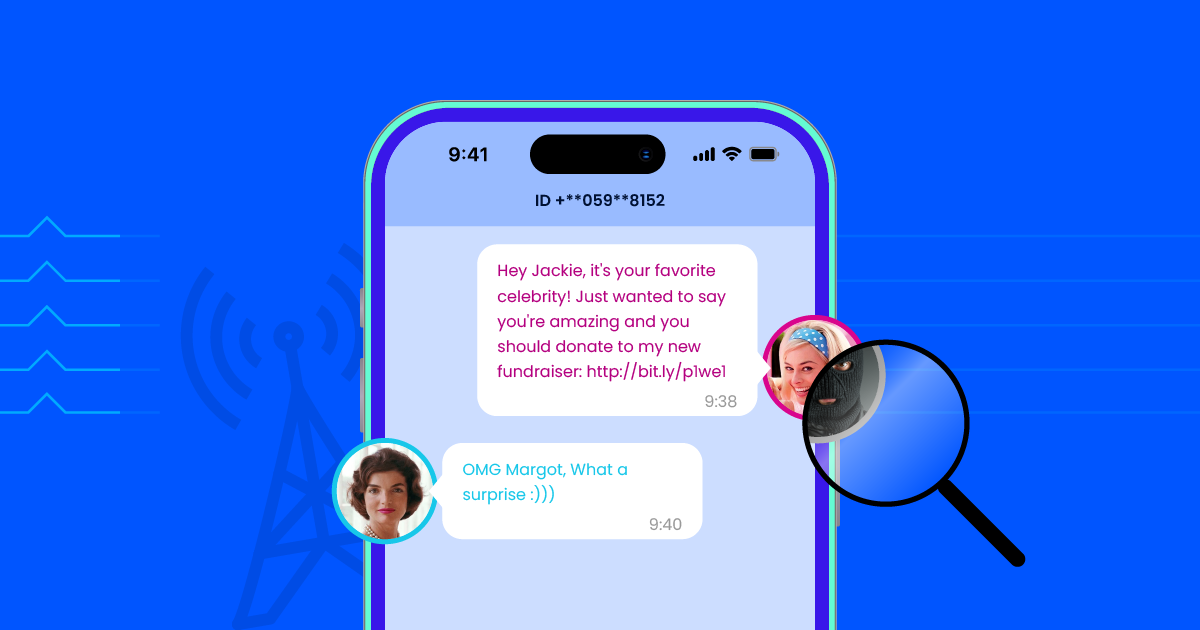
SMS Spoofing: What It Is, How It Works, and How to Protect Yourself
SMS spoofing is a powerful tool for cybercriminals and can be used to target individuals, businesses, and organizations. While it can be difficult to completely prevent spoofing attacks, being cautious…
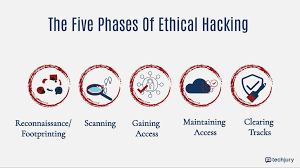
The 5 Stages of Hacking: A Comprehensive Guide to Understanding the Hacking Process
Hacking is a multi-step process, and understanding the stages can help cybersecurity professionals anticipate attacks, recognize vulnerabilities, and defend against intrusions more effectively. While the techniques and tools used by…
How to Maintain Your Privacy and Stay Anonymous Online: A Complete Guide
Privacy is not just about keeping secrets; it's about maintaining control over your personal data. As cyber threats grow and online tracking becomes more invasive, it’s essential to take steps…